Refer to the exhibits.
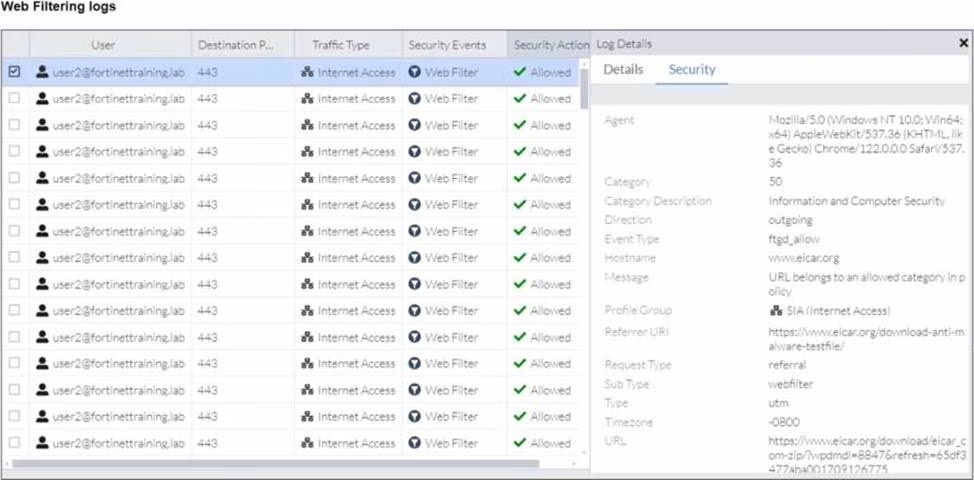
A FortiSASE administrator has configured an antivirus profile in the security profile group and applied it to the internet access policy. Remote users are still able to download the eicar.com-zip file from https://eicar.org. Traffic logs show traffic is allowed by the policy.
Which configuration on FortiSASE is allowing users to perform the download?
- A . Web filter is allowing the traffic.
- B . IPS is disabled in the security profile group.
- C . The HTTPS protocol is not enabled in the antivirus profile.
- D . Force certificate inspection is enabled in the policy.
A
Explanation:
Based on the provided exhibits and the configuration details, the reason why users are still able to
download the eicar.com-zip file despite having an antivirus profile applied is due to the Web Filter allowing the traffic.
Here is the step-by-step detailed explanation:
Web Filtering Logs Analysis:
The logs show that the traffic to the destination port 443 (which is HTTPS) is allowed and the security event triggered is Web Filter.
The log details indicate that the URL belongs to an allowed category in the policy and thus, the traffic is permitted by the Web Filter.
Security Profile Group Configuration:
The Web Filter with Inline-CASB section indicates that the site www.eicar.org is being monitored (93 occurrences) and not blocked.
Since the Web Filter is set to allow traffic from this site, the antivirus profile will not block it because the Web Filter decision takes precedence.
Antivirus Profile Configuration:
Although the antivirus profile is configured, the logs do not show any antivirus actions being triggered. This indicates that the web filter is overriding the antivirus action.
Policy Configuration:
The policy named "Web Traffic" shows that it has logging enabled and is set to accept traffic.
The profile group "SIA" applied to this policy includes both Web Filter and Antivirus settings.
However, since the Web Filter is allowing the traffic, the antivirus profile does not get the chance to inspect it.
Reference: FortiGate Security 7.2 Study Guide: Provides details on the precedence of web filtering over antivirus in security profiles.
Fortinet Knowledge Base: Detailed explanation of web filtering and antivirus profiles interaction.
An organization wants to block all video and audio application traffic but grant access to videos from CNN.
Which application override action must you configure in the Application Control with Inline-CASB?
- A . Allow
- B . Pass
- C . Permit
- D . Exempt
D
Explanation:
To block all video and audio application traffic while granting access to videos from CNN, you need to configure an application override action in the Application Control with Inline-CASB.
Here is the step-by-step detailed explanation:
Application Control Configuration:
Application Control is used to identify and manage application traffic based on predefined or custom application signatures.
Inline-CASB (Cloud Access Security Broker) extends these capabilities by allowing more granular
control over cloud applications.
Blocking Video and Audio Applications:
To block all video and audio application traffic, you can create a policy within Application Control to deny all categories related to video and audio streaming.
Granting Access to Specific Videos (CNN):
To allow access to videos from CNN specifically, you must create an override rule within the same Application Control profile.
The override action "Exempt" ensures that traffic to specified URLs (such as those from CNN) is not subjected to the blocking rules set for other video and audio traffic.
Configuration Steps:
Navigate to the Application Control profile in the FortiSASE interface.
Set the application categories related to video and audio streaming to "Block." Add a new override entry for CNN video traffic and set the action to "Exempt."
Reference: FortiOS 7.2 Administration Guide: Detailed steps on configuring Application Control and Inline-CASB. Fortinet Training Institute: Provides scenarios and examples of using Application Control with Inline-CASB for specific use cases.
Refer to the exhibits.
When remote users connected to FortiSASE require access to internal resources on Branch-2. how will traffic be routed?
- A . FortiSASE will use the SD-WAN capability and determine that traffic will be directed to HUB-2. which will then route traffic to Branch-2.
- B . FortiSASE will use the AD VPN protocol and determine that traffic will be directed to Branch-2 directly, using a static route
- C . FortiSASE will use the SD-WAN capability and determine that traffic will be directed to HUB-1, which will then route traffic to Branch-2.
- D . FortiSASE will use the AD VPN protocol and determine that traffic will be directed to Branch-2 directly, using a dynamic route
C
Explanation:
When remote users connected to FortiSASE require access to internal resources on Branch-2, the following process occurs:
SD-WAN Capability:
FortiSASE leverages SD-WAN to optimize traffic routing based on performance metrics and priorities. In the priority settings, HUB-1 is configured with the highest priority (P1), whereas HUB-2 has a lower priority (P2).
Traffic Routing Decision:
FortiSASE evaluates the available hubs (HUB-1 and HUB-2) and selects HUB-1 due to its highest priority setting.
Once the traffic reaches HUB-1, it is then routed to the appropriate branch based on internal routing policies.
Branch-2 Access:
Since HUB-1 has the highest priority, FortiSASE directs the traffic to HUB-1.
HUB-1 then routes the traffic to Branch-2, providing the remote users access to the internal resources.
Reference: FortiOS 7.2 Administration Guide: Details on SD-WAN configurations and priority settings. FortiSASE 23.2 Documentation: Explains how FortiSASE integrates with SD-WAN to route traffic based on defined priorities and performance metrics.
What are two advantages of using zero-trust tags? (Choose two.)
- A . Zero-trust tags can be used to allow or deny access to network resources
- B . Zero-trust tags can determine the security posture of an endpoint.
- C . Zero-trust tags can be used to create multiple endpoint profiles which can be applied to different endpoints
- D . Zero-trust tags can be used to allow secure web gateway (SWG) access
AB
Explanation:
Zero-trust tags are critical in implementing zero-trust network access (ZTNA) policies.
Here are the two key advantages of using zero-trust tags:
Access Control (Allow or Deny):
Zero-trust tags can be used to define policies that either allow or deny access to specific network resources based on the tag associated with the user or device.
This granular control ensures that only authorized users or devices with the appropriate tags can access sensitive resources, thereby enhancing security. Determining Security Posture:
Zero-trust tags can be utilized to assess and determine the security posture of an endpoint. Based on the assigned tags, FortiSASE can evaluate the device’s compliance with security policies, such as antivirus status, patch levels, and configuration settings.
Devices that do not meet the required security posture can be restricted from accessing the network or given limited access.
Reference: FortiOS 7.2 Administration Guide: Provides detailed information on configuring and using zero-trust tags for access control and security posture assessment.
FortiSASE 23.2 Documentation: Explains how zero-trust tags are implemented and used within the FortiSASE environment for enhancing security and compliance.
Refer to the exhibit.
In the user connection monitor, the FortiSASE administrator notices the user name is showing random characters.
Which configuration change must the administrator make to get proper user information?
- A . Turn off log anonymization on FortiSASE.
- B . Add more endpoint licenses on FortiSASE.
- C . Configure the username using FortiSASE naming convention.
- D . Change the deployment type from SWG to VPN.
A
Explanation:
In the user connection monitor, the random characters shown for the username indicate that log anonymization is enabled. Log anonymization is a feature that hides the actual user information in the logs for privacy and security reasons. To display proper user information, you need to disable log anonymization.
Log Anonymization:
When log anonymization is turned on, the actual usernames are replaced with random characters to protect user privacy.
This feature can be beneficial in certain environments but can cause issues when detailed user monitoring is required.
Disabling Log Anonymization:
Navigate to the FortiSASE settings.
Locate the log settings section.
Disable the log anonymization feature to ensure that actual usernames are displayed in the logs and user connection monitors.
Reference: FortiSASE 23.2 Documentation: Provides detailed steps on enabling and disabling log anonymization.
Fortinet Knowledge Base: Explains the impact of log anonymization on user monitoring and logging.
Refer to the exhibit.
To allow access, which web tiller configuration must you change on FortiSASE?
- A . FortiGuard category-based filter
- B . content filter
- C . URL Filter
- D . inline cloud access security broker (CASB) headers
C
Explanation:
The exhibit indicates that the URL https://www.bbc.com/ is being blocked due to containing a banned word ("fight"). To allow access to this specific URL, you need to adjust the URL filter settings on FortiSASE.
URL Filtering:
URL filtering allows administrators to define policies that block or allow access to specific URLs or URL patterns.
In this case, the URL filter is set to block any URL containing the word "fight."
Modifying URL Filter:
Navigate to the Web Filter configuration in FortiSASE.
Locate the URL filter settings.
Add an exception for the URL https://www.bbc.com/ to allow access, even if it contains a banned word.
Alternatively, remove or adjust the banned word list to exclude the word "fight" if it’s not critical to the security policy.
Reference: FortiOS 7.2 Administration Guide: Provides details on configuring and managing URL filters.
FortiSASE 23.2 Documentation: Explains how to set up and modify web filtering policies, including URL filters.
Which policy type is used to control traffic between the FortiClient endpoint to FortiSASE for secure internet access?
- A . VPN policy
- B . thin edge policy
- C . private access policy
- D . secure web gateway (SWG) policy
D
Explanation:
The Secure Web Gateway (SWG) policy is used to control traffic between the FortiClient endpoint and FortiSASE for secure internet access. SWG provides comprehensive web security by enforcing policies that manage and monitor user access to the internet.
Secure Web Gateway (SWG) Policy:
SWG policies are designed to protect users from web-based threats and enforce acceptable use policies.
These policies control and monitor user traffic to and from the internet, ensuring that security protocols are followed.
Traffic Control:
The SWG policy intercepts all web traffic, inspects it, and applies security rules before allowing or blocking access.
This policy type is crucial for providing secure internet access to users connecting through FortiSASE.
Reference: FortiOS 7.2 Administration Guide: Details on configuring and managing SWG policies.
FortiSASE 23.2 Documentation: Explains the role of SWG in securing internet access for endpoints.
Which role does FortiSASE play in supporting zero trust network access (ZTNA) principles9
- A . It offers hardware-based firewalls for network segmentation.
- B . It integrates with software-defined network (SDN) solutions.
- C . It can identify attributes on the endpoint for security posture check.
- D . It enables VPN connections for remote employees.
C
Explanation:
FortiSASE supports zero trust network access (ZTNA) principles by identifying attributes on the endpoint for security posture checks. ZTNA principles require continuous verification of user and device credentials, as well as their security posture, before granting access to network resources. Security Posture Check:
FortiSASE can evaluate the security posture of endpoints by checking for compliance with security policies, such as antivirus status, patch levels, and configuration settings.
This ensures that only compliant and secure devices are granted access to the network.
Zero Trust Network Access (ZTNA):
ZTNA is based on the principle of "never trust, always verify," which requires continuous assessment of user and device trustworthiness.
FortiSASE plays a crucial role in implementing ZTNA by performing these security posture checks and
enforcing access control policies.
Reference: FortiOS 7.2 Administration Guide: Provides information on ZTNA and endpoint security posture checks.
FortiSASE 23.2 Documentation: Details on how FortiSASE implements ZTNA principles.
When deploying FortiSASE agent-based clients, which three features are available compared to an agentless solution? (Choose three.)
- A . Vulnerability scan
- B . SSL inspection
- C . Anti-ransomware protection
- D . Web filter
- E . ZTNA tags
ABD
Explanation:
When deploying FortiSASE agent-based clients, several features are available that are not typically available with an agentless solution. These features enhance the security and management capabilities for endpoints.
Vulnerability Scan:
Agent-based clients can perform vulnerability scans on endpoints to identify and remediate security weaknesses.
This proactive approach helps to ensure that endpoints are secure and compliant with security policies.
SSL Inspection:
Agent-based clients can perform SSL inspection to decrypt and inspect encrypted traffic for threats.
This feature is critical for detecting malicious activities hidden within SSL/TLS encrypted traffic.
Web Filter:
Web filtering is a key feature available with agent-based clients, allowing administrators to control and monitor web access.
This feature helps enforce acceptable use policies and protect users from web-based threats.
Reference: FortiOS 7.2 Administration Guide: Explains the features and benefits of deploying agent-based clients.
FortiSASE 23.2 Documentation: Details the differences between agent-based and agentless solutions and the additional features provided by agent-based deployments.
Which FortiSASE feature ensures least-privileged user access to all applications?
- A . secure web gateway (SWG)
- B . SD-WAN
- C . zero trust network access (ZTNA)
- D . thin branch SASE extension
C
Explanation:
Zero Trust Network Access (ZTNA) is the FortiSASE feature that ensures least-privileged user access to all applications. ZTNA operates on the principle of "never trust, always verify," providing secure access based on the identity of users and devices, regardless of their location. Zero Trust Network Access (ZTNA):
ZTNA ensures that only authenticated and authorized users and devices can access applications.
It applies the principle of least privilege by granting access only to the resources required by the user,
minimizing the potential for unauthorized access.
Implementation:
ZTNA continuously verifies user and device trustworthiness and enforces granular access control policies.
This approach enhances security by reducing the attack surface and limiting lateral movement within the network.
Reference: FortiOS 7.2 Administration Guide: Provides detailed information on ZTNA and its role in ensuring least-privileged access.
FortiSASE 23.2 Documentation: Explains the implementation and benefits of ZTNA within the FortiSASE environment.
