Fortinet FCSS_SASE_AD-23 FCSS – FortiSASE 23 Administrator Online Training
Fortinet FCSS_SASE_AD-23 Online Training
The questions for FCSS_SASE_AD-23 were last updated at Dec 27,2025.
- Exam Code: FCSS_SASE_AD-23
- Exam Name: FCSS - FortiSASE 23 Administrator
- Certification Provider: Fortinet
- Latest update: Dec 27,2025
Refer to the exhibits.
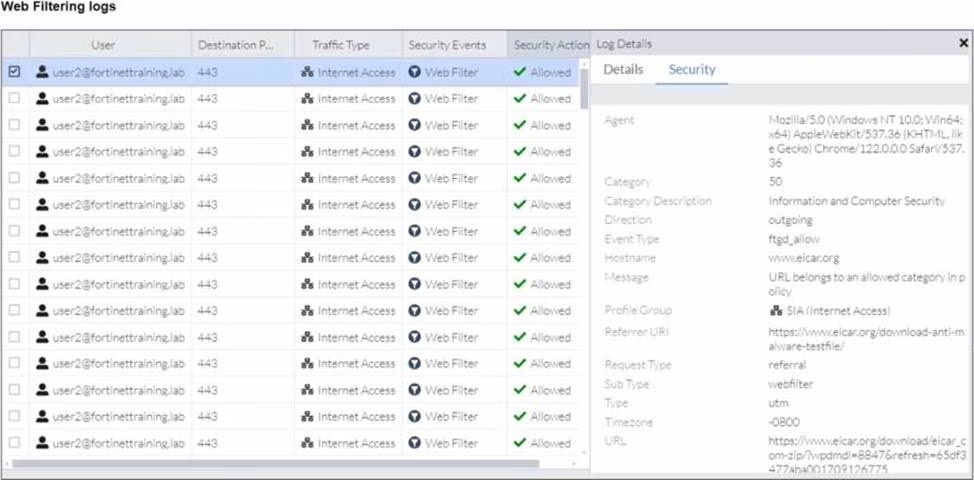
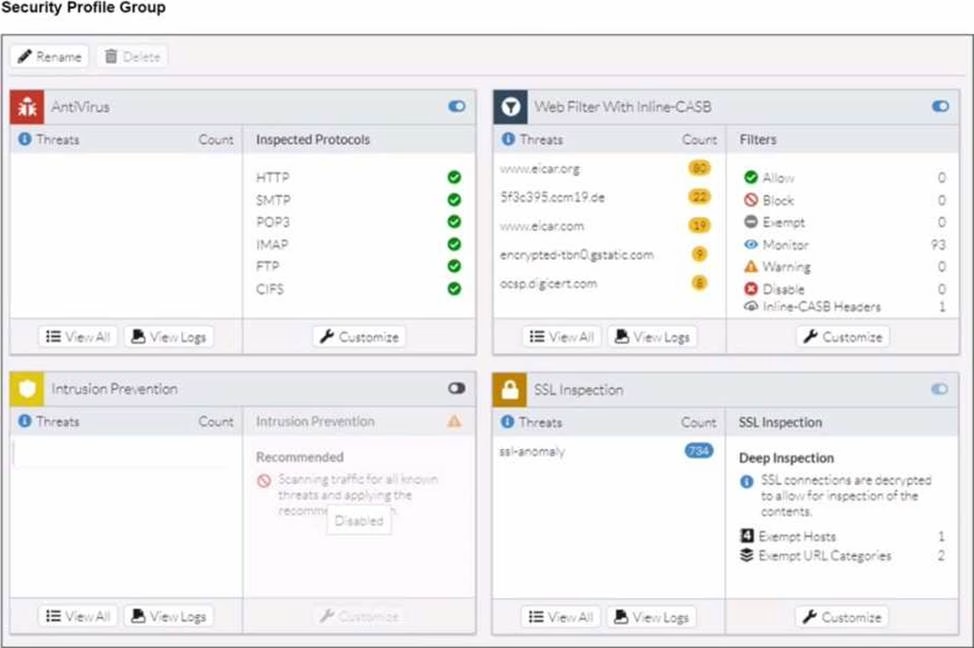
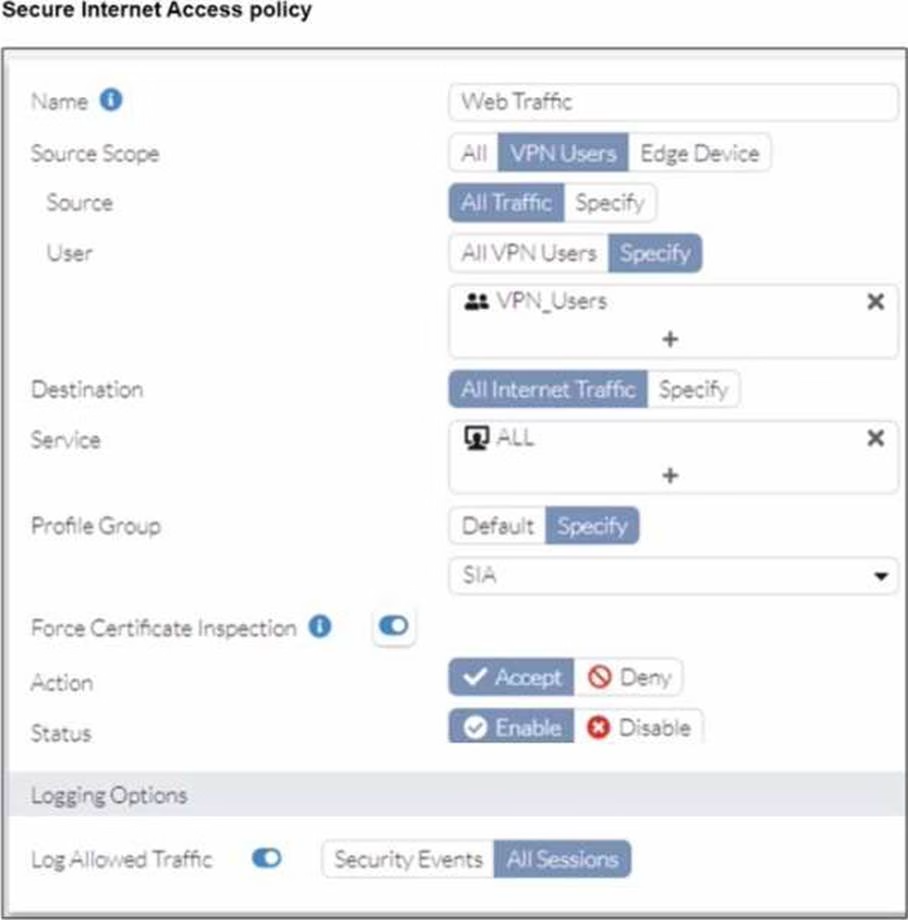
A FortiSASE administrator has configured an antivirus profile in the security profile group and applied it to the internet access policy. Remote users are still able to download the eicar.com-zip file from https://eicar.org. Traffic logs show traffic is allowed by the policy.
Which configuration on FortiSASE is allowing users to perform the download?
- A . Web filter is allowing the traffic.
- B . IPS is disabled in the security profile group.
- C . The HTTPS protocol is not enabled in the antivirus profile.
- D . Force certificate inspection is enabled in the policy.
An organization wants to block all video and audio application traffic but grant access to videos from CNN.
Which application override action must you configure in the Application Control with Inline-CASB?
- A . Allow
- B . Pass
- C . Permit
- D . Exempt
Refer to the exhibits.
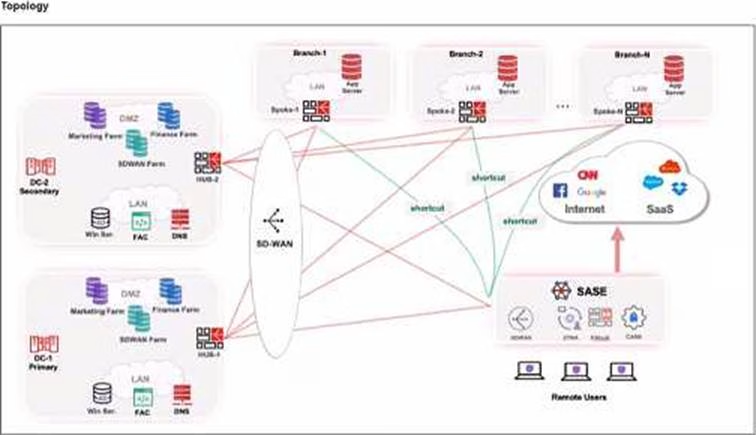
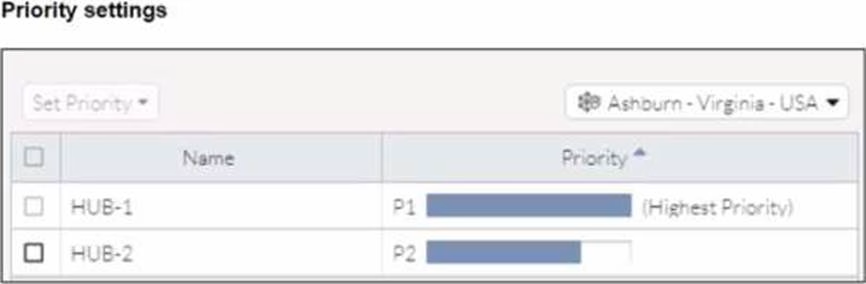
When remote users connected to FortiSASE require access to internal resources on Branch-2. how will traffic be routed?
- A . FortiSASE will use the SD-WAN capability and determine that traffic will be directed to HUB-2. which will then route traffic to Branch-2.
- B . FortiSASE will use the AD VPN protocol and determine that traffic will be directed to Branch-2 directly, using a static route
- C . FortiSASE will use the SD-WAN capability and determine that traffic will be directed to HUB-1, which will then route traffic to Branch-2.
- D . FortiSASE will use the AD VPN protocol and determine that traffic will be directed to Branch-2 directly, using a dynamic route
What are two advantages of using zero-trust tags? (Choose two.)
- A . Zero-trust tags can be used to allow or deny access to network resources
- B . Zero-trust tags can determine the security posture of an endpoint.
- C . Zero-trust tags can be used to create multiple endpoint profiles which can be applied to different endpoints
- D . Zero-trust tags can be used to allow secure web gateway (SWG) access
Refer to the exhibit.
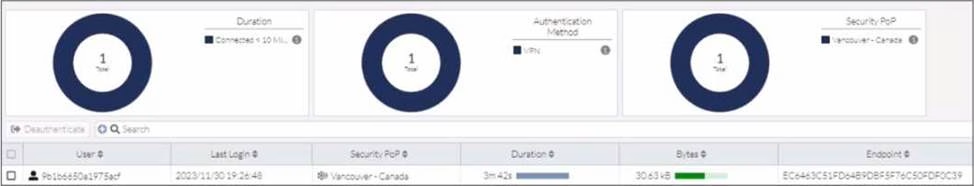
In the user connection monitor, the FortiSASE administrator notices the user name is showing random characters.
Which configuration change must the administrator make to get proper user information?
- A . Turn off log anonymization on FortiSASE.
- B . Add more endpoint licenses on FortiSASE.
- C . Configure the username using FortiSASE naming convention.
- D . Change the deployment type from SWG to VPN.
Refer to the exhibit.
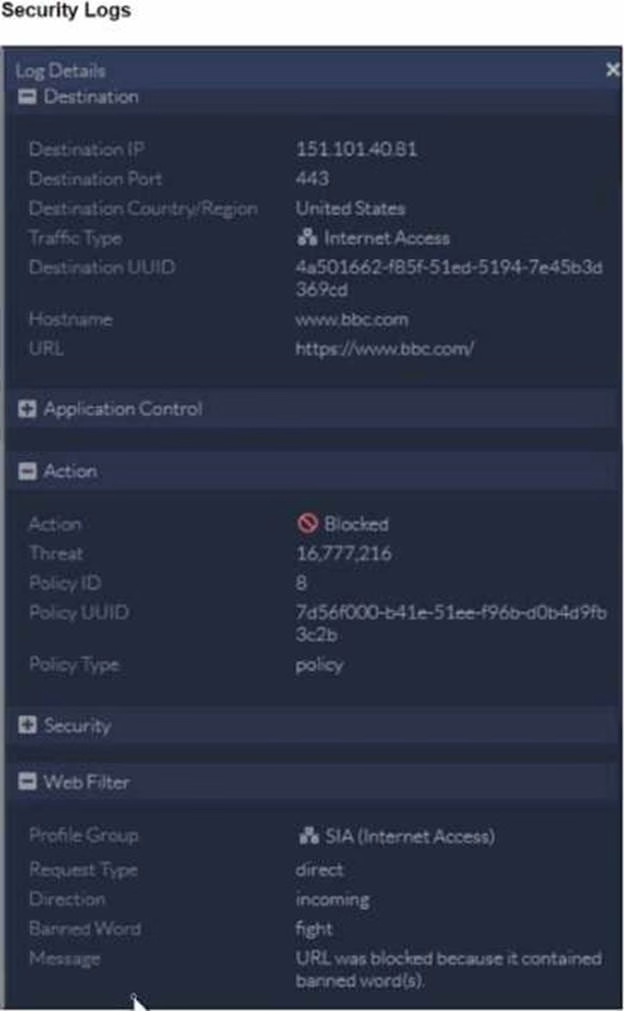
To allow access, which web tiller configuration must you change on FortiSASE?
- A . FortiGuard category-based filter
- B . content filter
- C . URL Filter
- D . inline cloud access security broker (CASB) headers
Which policy type is used to control traffic between the FortiClient endpoint to FortiSASE for secure internet access?
- A . VPN policy
- B . thin edge policy
- C . private access policy
- D . secure web gateway (SWG) policy
Which role does FortiSASE play in supporting zero trust network access (ZTNA) principles9
- A . It offers hardware-based firewalls for network segmentation.
- B . It integrates with software-defined network (SDN) solutions.
- C . It can identify attributes on the endpoint for security posture check.
- D . It enables VPN connections for remote employees.
When deploying FortiSASE agent-based clients, which three features are available compared to an agentless solution? (Choose three.)
- A . Vulnerability scan
- B . SSL inspection
- C . Anti-ransomware protection
- D . Web filter
- E . ZTNA tags
Which FortiSASE feature ensures least-privileged user access to all applications?
- A . secure web gateway (SWG)
- B . SD-WAN
- C . zero trust network access (ZTNA)
- D . thin branch SASE extension
Latest FCSS_SASE_AD-23 Dumps Valid Version with 30 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

