Refer to the exhibit.
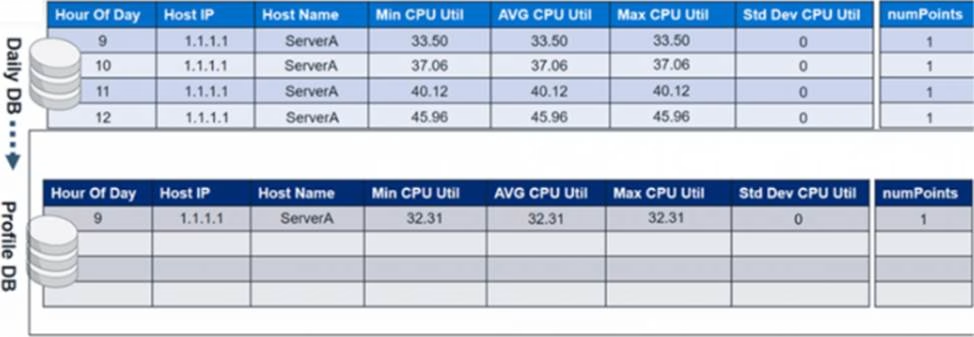
The profile database contains CPU utilization values from day one. At midnight on the second day, the CPU utilization values from the daily database will be merged with the profile database.
In the profile database, in the Hour of Day column where 9 is the value, what will be the updated minimum, maximum, and average CPU utilization values?
- A . Min CPU Util=32.31, Max CPU Util=33.50 and AVG CPU Util=33.50
- B . Min CPU Util=32.31, Max CPU Util=33.50 and AVG CPU Util=32.67
- C . Min CPU Util=32.31, Max CPU Util=32.31 and AVG CPU Util=32.31
- D . Min CPU Util=33.50, Max CPU Util=33.50 and AVG CPU Util=33.50
What is the primary purpose of remediation in FortiSIEM?
- A . To add new users to the network?
- B . To address and resolve detected security incidents?
- C . To upgrade the FortiSIEM software?
- D . To change the visual theme of the FortiSIEM interface?
Refer to the exhibit.
An administrator deploys a new collector for the first time, and notices that all the processes except the phMonitor are down.
How can the administrator bring the processes up?
- A . The administrator needs to run the command phtools –start all on the collector.
- B . Rebooting the collector will bring up the processes.
- C . The processes will come up after the collector is registered to the supervisor.
- D . The collector was not deployed properly and must be redeployed.
Refer to the exhibit.
Why was this incident auto cleared?
- A . Within five minutes the packet loss percentage dropped to a level where the reporting IP is the same as the host IP
- B . The original rule did not trigger within five minutes
- C . Within five minutes, the packet loss percentage dropped to a level where the reporting IP is same as the source IP
- D . Within five minutes, the packet loss percentage dropped to a level where the host IP of the original rule matches the host IP of the clear condition pattern
Which are key considerations when installing FortiSIEM agents on diverse operating systems?
- A . Verifying proper communication between the agent and the collector.
- B . Ensuring ample storage space on the device.
- C . Checking system compatibility and prerequisites.
- D . Validating the latest version of the web browser.
Which function of Linux is used by FortiSIEM for collecting logs?
- A . aureport
- B . ausearch
- C . autrace
- D . auditd
What will be the correct data type for inner query?
- A . INT16
- B . STRING
- C . INT32
- D . IP
On which disk are the SQLite databases that are used for the baselining stored?
- A . Disk1
- B . Disk4
- C . Disk2
- D . Disk3
Identify the processes associated with Machine Learning/Al on FortiSIEM. (Choose two.)
- A . phFortiInsightAI
- B . phReportMaster
- C . phRuleMaster
- D . phAnomaly
- E . phRuleWorker
How can FortiSIEM baseline and profile reports assist in enhancing security?
- A . By highlighting deviations from established norms?
- B . By detailing the software version details of network devices?
- C . By providing insights into potential areas of vulnerability?
- D . By generating a list of user passwords for verification purposes?
The MITRE ATT&CK® framework is primarily designed to:
- A . Boost the performance of security tools?
- B . Offer a detailed map of adversary tactics and techniques?
- C . Provide a guide for hardware installations?
- D . Recommend cybersecurity training programs?
Refer to the exhibit.
The service provider deployed FortiSIEM without a collector and added three customers on the supervisor.
What mistake did the administrator make?
- A . Customer A and customer B have overlapping IP addresses.
- B . Collectors must be deployed on all customer premises before they are added to organizations on the supervisor.
- C . The number of workers on the FortiSIEM cluster must match the number of customers added.
- D . At least one collector must be deployed to collect logs from service provider infrastructure devices.
Refer to the exhibit.
Based on the information provided in the exhibit, calculate the unused events for the next three minutes for a 520 EPS license.
- A . 72460
- B . 73460
- C . 74460
- D . 71460
Multi-tenancy solutions for SOC environments primarily serve to:
- A . Allow multiple clients to share a single application instance.
- B . Enable faster boot times for SOC servers.
- C . Streamline antivirus scans in the environment.
- D . Deploy agents at a faster rate.
One primary advantage of UEBA in FortiSIEM is:
- A . Assisting in network device installations?
- B . Identifying potentially harmful activities that deviate from established patterns?
- C . Streamlining software update processes?
- D . Designing a better user interface for administrators?
Where can you define automated remediation on FortiSIEM?
- A . Integration policy
- B . Notification policy
- C . Authentication policy
- D . Remediation policy
How can you invoke an integration policy on FortiSIEM rules?
- A . Through Notification Policy settings
- B . Through Incident Notification settings
- C . Through remediation scripts
- D . Through External Authentication settings
Refer to the exhibit.
What is the collector ID?
- A . 2000
- B . 50000
- C . 99
- D . 10000
What are two reasons that agents maintain communication with the supervisor after registration? (Choose two.)
- A . To report incoming EPS value
- B . To report logs and events
- C . To report health and its status
- D . To collect new agent template
In the context of FortiSIEM, agents are primarily tasked to:
- A . Act as a firewall and protect endpoints.
- B . Provide backup and restore capabilities.
- C . Forward logs and events to the FortiSIEM solution.
- D . Ensure smooth communication between different tenants.
Which of the following is crucial when defining and deploying collectors and agents in a SOC environment?
- A . Ensuring high-speed internet connectivity.
- B . Managing software licenses effectively.
- C . Ensuring compatibility with the target system.
- D . Coordinating with the software vendor for updates.
How do customers connect to a shared multi-tenant instance on FortiSOAR?
- A . The MSSP must provide secure network connectivity between the FortiSOAR manager node and the customer devices.
- B . The MSSP must install a Secure Message Exchange node to connect to the customer’s shared multi-tenant instance.
- C . The customer must install a tenant node to connect to the MSSP shared multi-tenant instance.
- D . The MSSP must install an agent node on the customer’s network to connect to the customer’s shared multi-tenant instance.
What happens to UEBA events when a user is off-net?
- A . The agent will upload the events to the Worker if it cannot upload them to a FortiSIEM collector
- B . The agent will cache events locally if it cannot upload them to a FortiSIEM collector
- C . The agent will upload the events to the Supervisor if it cannot upload them to a FortiSIEM collector
- D . The agent will drop the events if it cannot upload them to a FortiSIEM collector
What are the modes of Data Ingestion on FortiSOAR? (Choose three.)
- A . Rule based
- B . Notification based
- C . App Push
- D . Policy based
- E . Schedule based
FortiSIEM’s UEBA capabilities primarily focus on:
- A . Ensuring all users have similar access privileges?
- B . Monitoring and analyzing behavior patterns to identify potential risks?
- C . Providing encryption algorithms for data transfers?
- D . Streamlining the software update process?
Which two statements are true regarding template creation? (Choose two.)
- A . Templates must be created on the individual customer scope.
- B . You must be logged into the super global scope with an admin level account to create templates.
- C . Template name can contain spaces.
- D . You can create one or more templates and use it across multiple customers.
How does the MITRE ATT&CK® framework assist cybersecurity professionals?
- A . By providing a sales strategy for security products?
- B . By detailing a list of recommended security vendors?
- C . By offering insights into attacker behavior and techniques?
- D . By setting up firewall rules for different environments?
Refer to the exhibit.
Is the Windows agent delivering event logs correctly?
- A . The logs are buffered by the agent and will be sent once the status changes to managed.
- B . The agent is registered and it is sending logs correctly.
- C . The agent is not sending logs because it did not receive a monitoring template.
- D . Because the agent is unmanaged. the logs are dropped silently by the supervisor.
The main benefit of a multi-tenancy SOC solution for an MSSP is:
- A . Decreased overhead costs.
- B . The ability to host multiple tenants within a shared environment.
- C . Increased storage capacity for logs.
- D . Automatic software updates across all agents.
Manually remediating incidents in FortiSIEM is beneficial when:
- A . There is no internet connection?
- B . An incident is unique or complex and requires human judgment?
- C . The FortiSIEM software is due for an update?
- D . Incidents occur outside business hours?
