Fortinet FCP_FGT_AD-7.4 FCP – FortiGate 7.4 Administrator Online Training
Fortinet FCP_FGT_AD-7.4 Online Training
The questions for FCP_FGT_AD-7.4 were last updated at Mar 01,2025.
- Exam Code: FCP_FGT_AD-7.4
- Exam Name: FCP - FortiGate 7.4 Administrator
- Certification Provider: Fortinet
- Latest update: Mar 01,2025
An administrator has configured central DNAT and virtual IPs.
Which item can be selected in the firewall policy Destination field?
- A . An IP pool
- B . A VIP object
- C . A VIP group
- D . The mapped IP address object of the VIP object
Which three actions are valid for static URL filtering? (Choose three.)
- A . Block
- B . Warning
- C . Shape
- D . Exempt
- E . Allow
Which two settings must you configure when FortiGate is being deployed as a root FortiGate in a Security Fabric topology? (Choose two.)
- A . FortiManager IP address
- B . FortiAnalyzer IP address
- C . Pre-authorize downstream FortiGate devices
- D . Fabric name
Which two statements about the application control profile mode are true? (Choose two.)
- A . It uses flow-based scanning techniques, regardless of the inspection mode used.
- B . It cannot be used in conjunction with IPS scanning.
- C . It can be selected in either flow-based or proxy-based firewall policy.
- D . It can scan only unsecure protocols.
Which are two benefits of using SD-WAN? (Choose two.)
- A . FortiGate performs per-packet distribution across multiple SD-WAN members.
- B . WAN is used effectively.
- C . Application steering is available.
- D . Firewall policies are not required.
Which two statements about advanced AD access mode for the FSSO collector, agent are true? (Choose two.)
- A . FortiGate can act as an LDAP client to configure the group filters.
- B . It uses the Windows convention for naming; that is, DomainUsername.
- C . It supports monitoring of nested groups.
- D . It is only supported if DC agents are deployed.
An administrator needs to create a tunnel mode SSL-VPN to access an internal web server from the Internet. The web server is connected to port1. The Internet is connected to port2. Both interfaces belong to the VDOM named Corporation.
What interface must be used as the source for the firewall policy that will allow this traffic?
- A . ssl.root
- B . ssl.Corporation
- C . port2
- D . port1
View the exhibit.
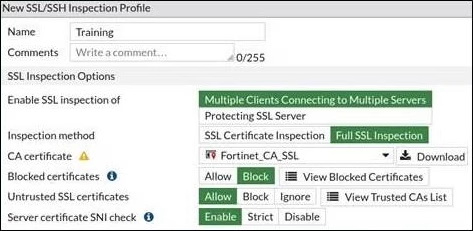
Which two behaviors result from this full (deep) SSL configuration? (Choose two.)
- A . The browser bypasses all certificate warnings and allows the connection.
- B . A temporary trusted FortiGate certificate replaces the server certificate, even when the server certificate is untrusted.
- C . A temporary trusted FortiGate certificate replaces the server certificate when the server certificate is trusted.
- D . A temporary untrusted FortiGate certificate replaces the server certificate when the server certificate is untrusted.
Which statement best describes the role of a DC agent in an FSSO DC agent mode solution?
- A . It captures the login and logoff events and forwards them to the collector agent.
- B . It captures the login events and forwards them to the collector agent.
- C . It captures the login events and forwards them to FortiGate.
- D . It captures the user IP address and workstation name and forwards them to FortiGate.
Which two IP pool types enable you to identify user connections without having to log user traffic? (Choose two.)
- A . Fixed port range
- B . Port block allocation
- C . One-to-one
- D . Overload
Latest FCP_FGT_AD-7.4 Dumps Valid Version with 200 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

