Fortinet FCP_FGT_AD-7.4 FCP – FortiGate 7.4 Administrator Online Training
Fortinet FCP_FGT_AD-7.4 Online Training
The questions for FCP_FGT_AD-7.4 were last updated at Apr 23,2025.
- Exam Code: FCP_FGT_AD-7.4
- Exam Name: FCP - FortiGate 7.4 Administrator
- Certification Provider: Fortinet
- Latest update: Apr 23,2025
Refer to the exhibits.
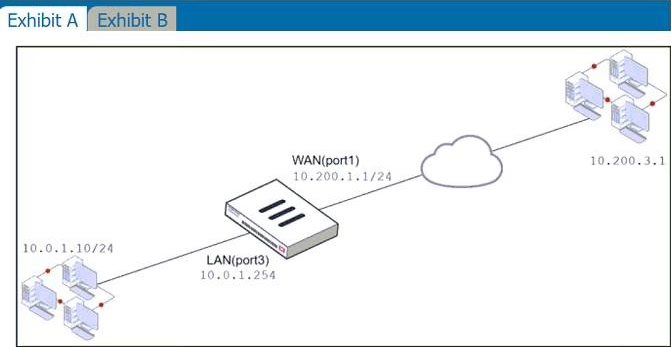
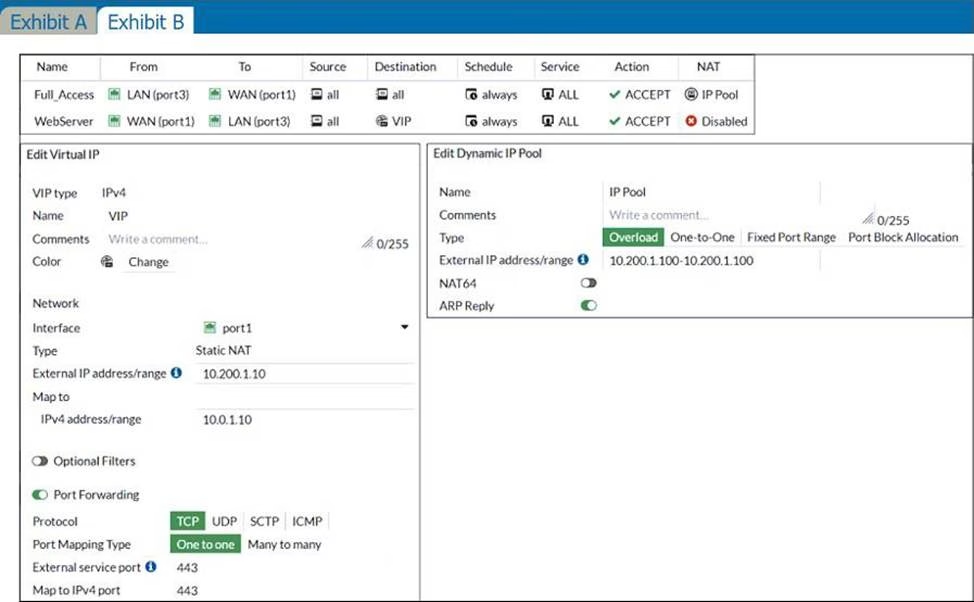
The exhibits contain a network diagram, and virtual IP, IP pool, and firewall policies configuration information.
The WAN (port1) interface has the IP address 10.200.1.1/24.
The LAN (port3) interface has the IP address 10.0.1.254/24.
The first firewall policy has NAT enabled using IP pool.
The second firewall policy is configured with a VIP as the destination address.
Which IP address will be used to source NAT (SNAT) the internet traffic coming from a workstation with the IP address 10.0.1.10?
- A . 10.200.1.1
- B . 10.0.1.254
- C . 10.200.1.10
- D . 10.200.1.100
Refer to the exhibit.
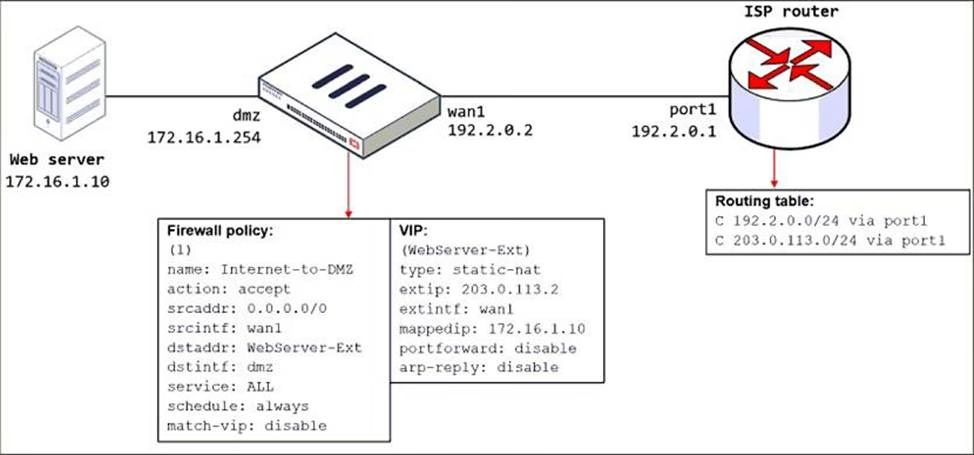
The exhibit shows a diagram of a FortiGate device connected to the network, the firewall policy and VIP configuration on the FortiGate device, and the routing table on the ISP router.
When the administrator tries to access the web server public address (203.0.113.2) from the internet, the connection times out. At the same time, the administrator runs a sniffer on FortiGate to capture incoming web traffic to the server and does not see any output.
Based on the information shown in the exhibit, what configuration change must the administrator make to fix the connectivity issue?
- A . Configure a loopback interface with address 203.0.113.2/32.
- B . In the VIP configuration, enable arp-reply.
- C . Enable port forwarding on the server to map the external service port to the internal service port.
- D . In the firewall policy configuration, enable match-vip.
Which two statements are true about the FGCP protocol? (Choose two.)
- A . FGCP elects the primary FortiGate device.
- B . FGCP is not used when FortiGate is in transparent mode.
- C . FGCP runs only over the heartbeat links.
- D . FGCP is used to discover FortiGate devices in different HA groups.
A network administrator wants to set up redundant IPsec VPN tunnels on FortiGate by using two IPsec VPN tunnels and static routes.
All traffic must be routed through the primary tunnel when both tunnels are up. The secondary tunnel must be used only if the primary tunnel goes down. In addition, FortiGate should be able to detect a dead tunnel to speed up tunnel failover.
Which two key configuration changes must the administrator make on FortiGate to meet the requirements? (Choose two.)
- A . Configure a higher distance on the static route for the primary tunnel, and a lower distance on the static route for the secondary tunnel.
- B . Configure a lower distance on the static route for the primary tunnel, and a higher distance on the
static route for the secondary tunnel. - C . Enable Auto-negotiate and Autokey Keep Alive on the phase 2 configuration of both tunnels.
- D . Enable Dead Peer Detection.
What are two benefits of flow-based inspection compared to proxy-based inspection? (Choose two.)
- A . FortiGate uses fewer resources.
- B . FortiGate performs a more exhaustive inspection on traffic.
- C . FortiGate adds less latency to traffic.
- D . FortiGate allocates two sessions per connection.
FortiGuard categories can be overridden and defined in different categories. To create a web rating override for the example.com home page, the override must be configured using a specific syntax.
Which two syntaxes are correct to configure a web rating override for the home page? (Choose two.)
- A . www.example.com
- B . www.example.com/index.html
- C . www.example.com:443
- D . example.com
Refer to exhibit.
An administrator configured the web filtering profile shown in the exhibit to block access to all social networking sites except Twitter. However, when users try to access twitter.com, they are redirected to a FortiGuard web filtering block page.
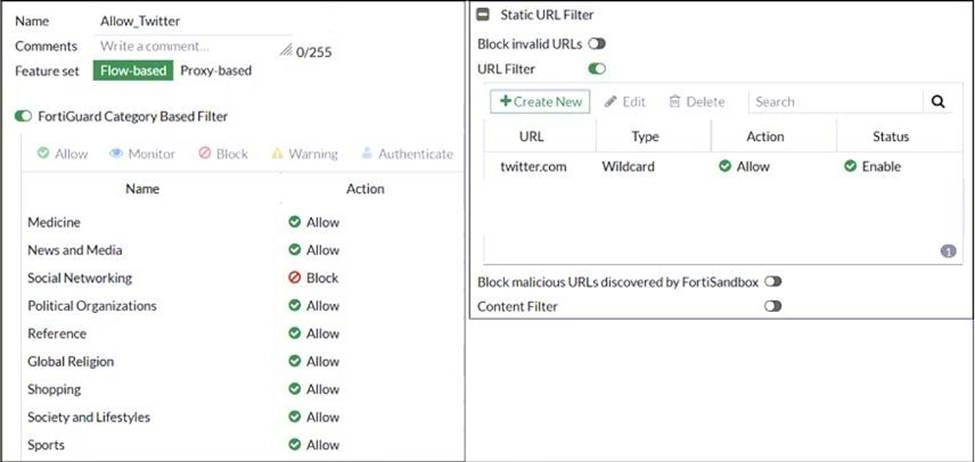
Based on the exhibit, which configuration change can the administrator make to allow Twitter while blocking all other social networking sites?
- A . On the FortiGuard Category Based Filter configuration, set Action to Warning for Social Networking.
- B . On the Static URL Filter configuration, set Type to Simple.
- C . On the Static URL Filter configuration, set Action to Exempt.
- D . On the Static URL Filter configuration, set Action to Monitor.
Which three statements explain a flow-based antivirus profile? (Choose three.)
- A . Flow-based inspection uses a hybrid of the scanning modes available in proxy-based inspection.
- B . If a virus is detected, the last packet is delivered to the client.
- C . The IPS engine handles the process as a standalone.
- D . FortiGate buffers the whole file but transmits to the client at the same time.
- E . Flow-based inspection optimizes performance compared to proxy-based inspection.
Which three criteria can FortiGate use to look for a matching firewall policy to process traffic? (Choose three.)
- A . Services defined in the firewall policy
- B . Highest to lowest priority defined in the firewall policy
- C . Destination defined as Internet Services in the firewall policy
- D . Lowest to highest policy ID number
- E . Source defined as Internet Services in the firewall policy
What are two functions of ZTNA? (Choose two.)
- A . ZTNA manages access through the client only.
- B . ZTNA manages access for remote users only.
- C . ZTNA provides a security posture check.
- D . ZTNA provides role-based access.
Latest FCP_FGT_AD-7.4 Dumps Valid Version with 200 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

