Fortinet FCP_FGT_AD-7.4 FCP – FortiGate 7.4 Administrator Online Training
Fortinet FCP_FGT_AD-7.4 Online Training
The questions for FCP_FGT_AD-7.4 were last updated at Mar 03,2025.
- Exam Code: FCP_FGT_AD-7.4
- Exam Name: FCP - FortiGate 7.4 Administrator
- Certification Provider: Fortinet
- Latest update: Mar 03,2025
To complete the final step of a Security Fabric configuration, an administrator must authorize all the devices on which device?
- A . FortiManager
- B . Root FortiGate
- C . FortiAnalyzer
- D . Downstream FortiGate
NGFW mode allows policy-based configuration for most inspection rules.
Which security profile’s configuration does not change when you enable policy-based inspection?
- A . Web filtering
- B . Antivirus
- C . Web proxy
- D . Application control
Refer to the exhibit to view the application control profile.
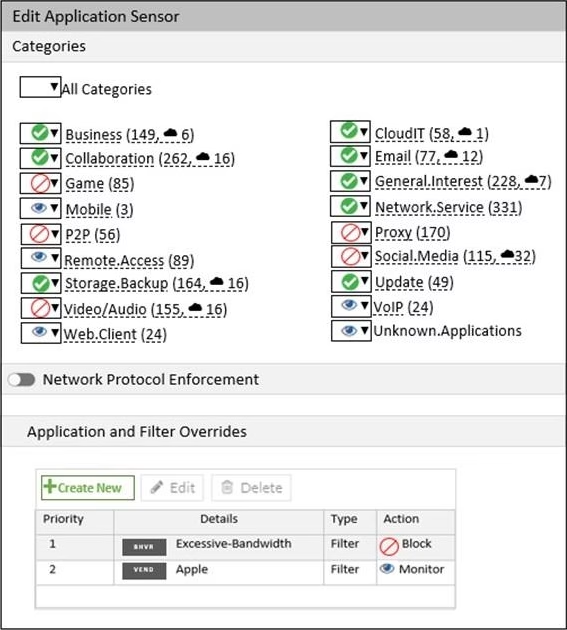
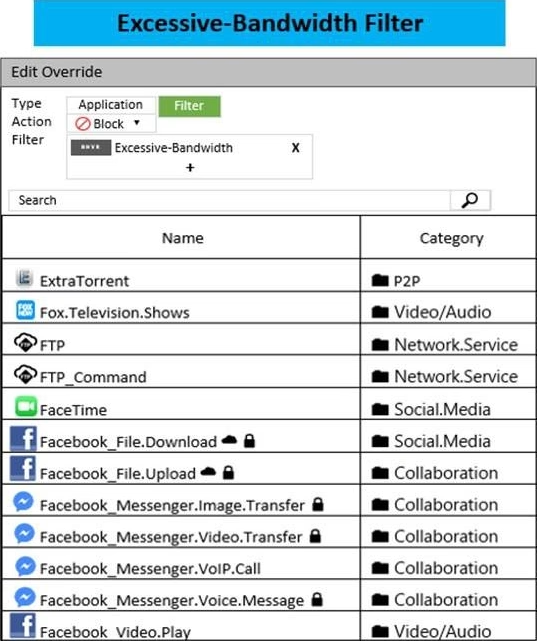
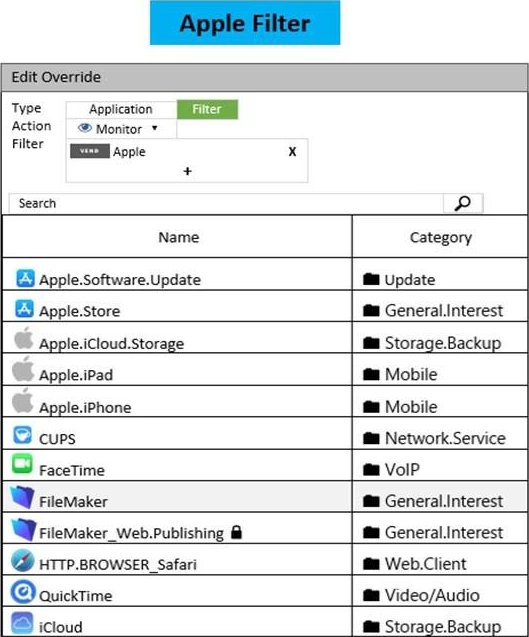
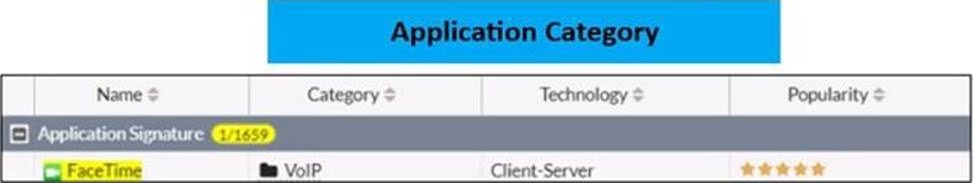
Based on the configuration, what will happen to Apple FaceTime?
- A . Apple FaceTime will be allowed, based on the Apple filter configuration.
- B . Apple FaceTime will be allowed, based on the Categories configuration.
- C . Apple FaceTime will be blocked, based on the Excessive-Bandwidth filter configuration.
- D . Apple FaceTime will be allowed only if the filter in Application and Filter Overrides is set to Learn.
Which two statements are true about collector agent standard access mode? (Choose two.)
- A . Standard mode uses Windows convention-NetBios: DomainUsername.
- B . Standard mode security profiles apply to organizational units (OU).
- C . Standard mode security profiles apply to user groups.
- D . Standard access mode supports nested groups.
What is the effect of enabling auto-negotiate on the phase 2 configuration of an IPsec tunnel?
- A . FortiGate automatically negotiates different local and remote addresses with the remote peer.
- B . FortiGate automatically negotiates a new security association after the existing security association expires.
- C . FortiGate automatically negotiates different encryption and authentication algorithms with the remote peer.
- D . FortiGate automatically brings up the IPsec tunnel and keeps it up, regardless of activity on the IPsec tunnel.
Which two types of traffic are managed only by the management VDOM? (Choose two.)
- A . FortiGuard web filter queries
- B . PKI
- C . Traffic shaping
- D . DNS
Which two protocol options are available on the CLI but not on the GUI when configuring an SD-WAN Performance SLA? (Choose two.)
- A . udp-echo
- B . DNS
- C . TWAMP
- D . ping
Which two VDOMs are the default VDOMs created when FortiGate is set up in split VDOM mode? (Choose two.)
- A . FG-traffic
- B . Mgmt
- C . FG-Mgmt
- D . Root
Which three methods are used by the collector agent for AD polling? (Choose three.)
- A . WMI
- B . Novell API
- C . WinSecLog
- D . NetAPI
- E . FortiGate polling
If the Services field is configured in a Virtual IP (VIP), which of the following statements is true when central NAT is used?
- A . The Services field removes the requirement of creating multiple VIPs for different services.
- B . The Services field is used when several VIPs need to be bundled into VIP groups.
- C . The Services field does not allow source NAT and destination NAT to be combined in the same policy.
- D . The Services field does not allow multiple sources of traffic, to use multiple services, to connect to a
single computer.
Latest FCP_FGT_AD-7.4 Dumps Valid Version with 200 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

