Fortinet FCP_FAZ_AD-7.4 FCP – FortiAnalyzer 7.4 Administrator Online Training
Fortinet FCP_FAZ_AD-7.4 Online Training
The questions for FCP_FAZ_AD-7.4 were last updated at Feb 22,2025.
- Exam Code: FCP_FAZ_AD-7.4
- Exam Name: FCP - FortiAnalyzer 7.4 Administrator
- Certification Provider: Fortinet
- Latest update: Feb 22,2025
Which two methods can you use to restrict administrative access on FortiAnalyzer? (Choose two.)
- A . Configure trusted hosts.
- B . Limit access to specific virtual domains.
- C . Fabric connectors to external LDAP servers.
- D . Use administrator profiles.
Which statement when you are upgrading the firmware on an HA cluster made up of three FortiAnalyzer devices is true?
- A . You can perform the firmware upgrade using only a console connection.
- B . All FortiAnalyzer devices will be upgraded at the same time.
- C . Enabling uninterruptible-upgrade prevents normal operations from being interrupted during the upgrade.
- D . First, upgrade the secondary devices, and then upgrade the primary device.
What is the best approach to handle a hard disk failure on a FortiAnalyzer that supports hardware RAID?
- A . There is no need to do anything because the disk will self-recover.
- B . Run execute format disk to format and restart the FortiAnalyzer device.
- C . Perform a hot swap of the disk.
- D . Shut down FortiAnalyzer and replace the disk.
Which three RAID configurations provide fault tolerance on FortiAnalyzer? (Choose three.)
- A . RAIDO
- B . RAID 5
- C . RAID1
- D . RAID 6+0
- E . RAID 0+0
Refer to the exhibit.
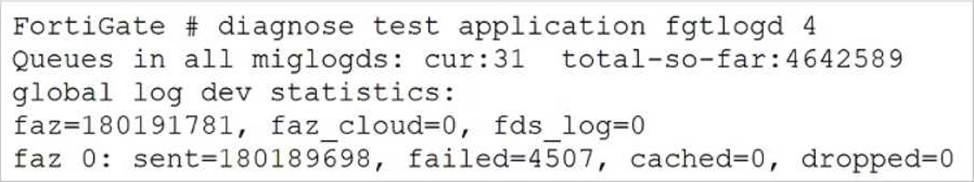
Based on the output, what can you conclude about the FortiAnalyzer logging status?
- A . The connection between FortiGate and FortiAnalyzer is overloaded.
- B . FortiGate has logs to send, but FortiAnalyzer is unavailable.
- C . FortiGate is configured to send logs in batches.
- D . FortiGate is sending logs again after it performed a reboot.
Which two methods are the most common methods to control and restrict administrative access on FortiAnalyzer? (Choose two.)
- A . Virtual domains
- B . Administrative access profiles
- C . Trusted hosts
- D . Security Fabric
Which daemon is responsible for enforcing raw log file size?
- A . logfiled
- B . oftpd
- C . sqlplugind
- D . miglogd
An administrator has configured the following settings:
config system global
set log-checksum md5-auth
end
What is the significance of executing this command?
- A . This command records the log file MD5 hash value.
- B . This command records passwords in log files and encrypts them.
- C . This command encrypts log transfer between FortiAnalyzer and other devices.
- D . This command records the log file MD5 hash value and authentication code.
Which two of the following must you configure on FortiAnalyzer to email a FortiAnalyzer report externally? (Choose two.)
- A . Mail server
- B . Output profile
- C . SFTP server
- D . Report scheduling
For which two purposes would you use the command set log checksum? (Choose two.)
- A . To help protect against man-in-the-middle attacks during log upload from FortiAnalyzer to an SFTP server
- B . To prevent log modification or tampering
- C . To encrypt log communications
- D . To send an identical set of logs to a second logging server
Latest FCP_FAZ_AD-7.4 Dumps Valid Version with 30 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

