EC-Council ECSAv10 EC-Council Certified Security Analyst Online Training
EC-Council ECSAv10 Online Training
The questions for ECSAv10 were last updated at Jan 10,2026.
- Exam Code: ECSAv10
- Exam Name: EC-Council Certified Security Analyst
- Certification Provider: EC-Council
- Latest update: Jan 10,2026
Which of the following roles of Microsoft Windows Active Directory refers to the ability of an active directory to transfer roles to any domain controller (DC) in the enterprise?
- A . Master Browser (MB)
- B . Global Catalog (GC)
- C . Flexible Single Master Operation (FSMO)
- D . Rights Management Services (RMS)
A user unknowingly installed a fake malicious banking app in his Android mobile. This app includes a configuration file that consists of phone numbers of the bank. When the user makes a call to the bank, he is automatically redirected to the number being used by the attacker. The attacker impersonates as a banking official. Also, the app allows the attacker to call the user, then the app displays fake caller ID on the user’s mobile resembling call from a legitimate bank.
Identify the attack being performed on the Android mobile user?
- A . Tailgating
- B . SMiShing
- C . Vishing
- D . Eavesdropping
How does OS Fingerprinting help you as a pen tester?
- A . It defines exactly what software the target has installed
- B . It doesn’t depend on the patches that have been applied to fix existing security holes
- C . It opens a security-delayed window based on the port being scanned
- D . It helps to research vulnerabilities that you can use to exploit on a target system
While scanning a server, you found rpc, nfs and mountd services running on it. During the investigation, you were told that NFS Shares were mentioned in the /etc/exports list of the NFS server.
Based on this information, which among the following commands would you issue to view the NFS Shares running on the server?
- A . showmount
- B . nfsenum
- C . mount
- D . rpcinfo
SecGlobal Corporation hired Michael, a penetration tester. Management asked Michael to perform cloud penetration testing on the company’s cloud infrastructure. As a part of his task, he started checking all the agreements with cloud service provider and came to a conclusion that it is not possible to perform penetration testing on the cloud services that are being used by the organization due to the level of responsibilities between company and the Cloud Service Provider (CSP).
Identify the type of cloud service deployed by the organization?
- A . Platform as a service (PaaS)
- B . Software as a service (SaaS)
- C . Anything as a service (XaaS)
- D . Infrastructure as a service (IaaS)
A team of cyber criminals in Germany has sent malware-based emails to workers of a fast-food center which is having multiple outlets spread geographically. When any of the employees click on the malicious email, it will give backdoor access to the point of sale (POS) systems located at various outlets. After gaining access to the POS systems, the criminals will be able to obtain credit card details of the fast-food center’s customers.
In the above scenario, identify the type of attack being performed on the fast-food center?
- A . Phishing
- B . Vishing
- C . Tailgating
- D . Dumpster diving
As a part of the pen testing process, James performs a FIN scan as given below:
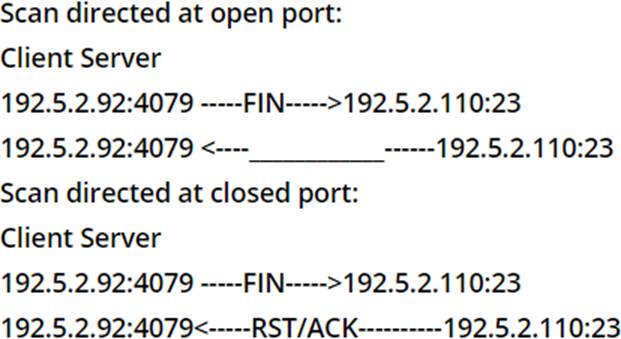
What will be the response if the port is open?
- A . No response
- B . FIN/RST
- C . FIN/ACK
- D . RST
Peter works as a lead penetration tester in a security service firm named Xsecurity. Recently, Peter was assigned a white-box pen test assignment testing the security of an IDS system deployed by a client. During the preliminary information gathering, Peter discovered the TTL to reach the IDS system from his end is 30. Peter created a Trojan and fragmented it in to 1-character packets using the Colasoft packet builder tool. He then used a packet flooding utility to bombard the IDS with these fragmented packets with the destination address of a target host behind the IDS whose TTL is 35.
What is Peter trying to achieve?
- A . Peter is trying to bypass the IDS system using a Trojan
- B . Peter is trying to bypass the IDS system using the broadcast address
- C . Peter is trying to bypass the IDS system using the insertion attack
- D . Peter is trying to bypass the IDS system using inconsistent packets
Robert is a network admin in XYZ Inc. He deployed a Linux server in his enterprise network and wanted to share some critical and sensitive files that are present in the Linux server with his subordinates. He wants to set the file access permissions using chmod command in such a way that his subordinates can only read/view the files but cannot edit or delete the files.
Which of the following chmod commands can Robert use in order to achieve his objective?
- A . chmod 666
- B . chmod 644
- C . chmod 755
- D . chmod 777
Tecty Motors Pvt. Ltd. has recently deployed RFID technology in the vehicles which allows the car owner to unlock the car with the exchange of a valid RFID signal between a reader and a tag. Jamie, on the other hand, is a hacker who decided to exploit this technology with the aim of stealing the target vehicle. To perform this attack on the target vehicle, he first used an automated tool to intercept the signals between the reader and the tag to capture a valid RFID signal and then later used the same signal to unlock and steal the victim’s car.
Which of the following RFID attacks Jamie has performed in the above scenario?
- A . RFID cloning
- B . Replay attack
- C . DoS attack
- D . Power analysis attack
Latest ECSAv10 Dumps Valid Version with 150 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

