EC-Council ECSAv10 EC-Council Certified Security Analyst Online Training
EC-Council ECSAv10 Online Training
The questions for ECSAv10 were last updated at Dec 11,2025.
- Exam Code: ECSAv10
- Exam Name: EC-Council Certified Security Analyst
- Certification Provider: EC-Council
- Latest update: Dec 11,2025
Sandra, a wireless network auditor, discovered her client is using WEP. To prove the point that the WEP encryption is very weak, she wants to decrypt some WEP packets. She successfully captured the WEP data packets, but could not reach the content as the data is encrypted.
Which of the following will help Sandra decrypt the data packets without knowing the key?
- A . Fragmentation Attack
- B . Chopchop Attack
- C . ARP Poisoning Attack
- D . Packet injection Attack
Peter, a disgruntled ex-employee of Zapmaky Solutions Ltd., is trying to jeopardize the company’s website http://zapmaky.com. He conducted the port scan of the website by using the Nmap tool to extract the information about open ports and their corresponding services. While performing the scan, he recognized that some of his requests are being blocked by the firewall deployed by the IT personnel of Zapmaky and he wants to bypass the same. For evading the firewall, he wanted to employ the stealth scanning technique which is an incomplete TCP three-way handshake method that can effectively bypass the firewall rules and logging mechanisms.
Which if the following Nmap commands should Peter execute to perform stealth scanning?
- A . nmap -sT -v zapmaky.com
- B . nmap -T4 -A -v zapmaky.com
- C . nmap -sX -T4 -A -v zapmaky.com
- D . nmap -sN -A zapmaky.com
Richard, a penetration tester was asked to assess a web application. During the assessment, he discovered a file upload field where users can upload their profile pictures. While scanning the page for vulnerabilities, Richard found a file upload exploit on the website. Richard wants to test the web application by uploading a malicious PHP shell, but the web page denied the file upload. Trying to get around the security, Richard added the ‘jpg’ extension to the end of the file. The new file name ended with ‘.php.jpg’. He then used the Burp suite tool and removed the ‘jpg’’ extension from the request while uploading the file. This enabled him to successfully upload the PHP shell.
Which of the following techniques has Richard implemented to upload the PHP shell?
- A . Session stealing
- B . Cookie tampering
- C . Cross site scripting
- D . Parameter tampering
Richard is working on a web app pen testing assignment for one of his clients. After preliminary information, gathering and vulnerability scanning Richard runs the SQLMAP tool to extract the database information.
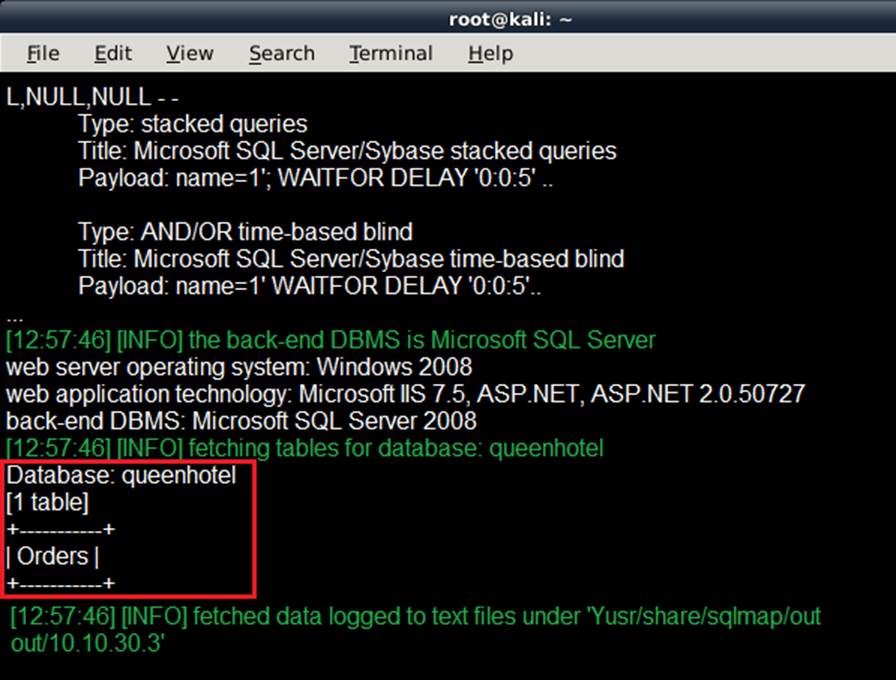
Which of the following commands will give Richard an output as shown in the screenshot?
- A . sqlmap Curl http://quennhotel.com/about.aspx?name=1 CD queenhotel –tables
- B . sqlmap Curl http://quennhotel.com/about.aspx?name=1 Cdbs
- C . sqlmap Curl http://quennhotel.com/about.aspx?name=1 CD queenhotel CT –columns
- D . sqlmap Curl http://quennhotel.com/about.aspx?name=1 Cdatabase queenhotel Ctables
Identify the PRGA from the following screenshot:
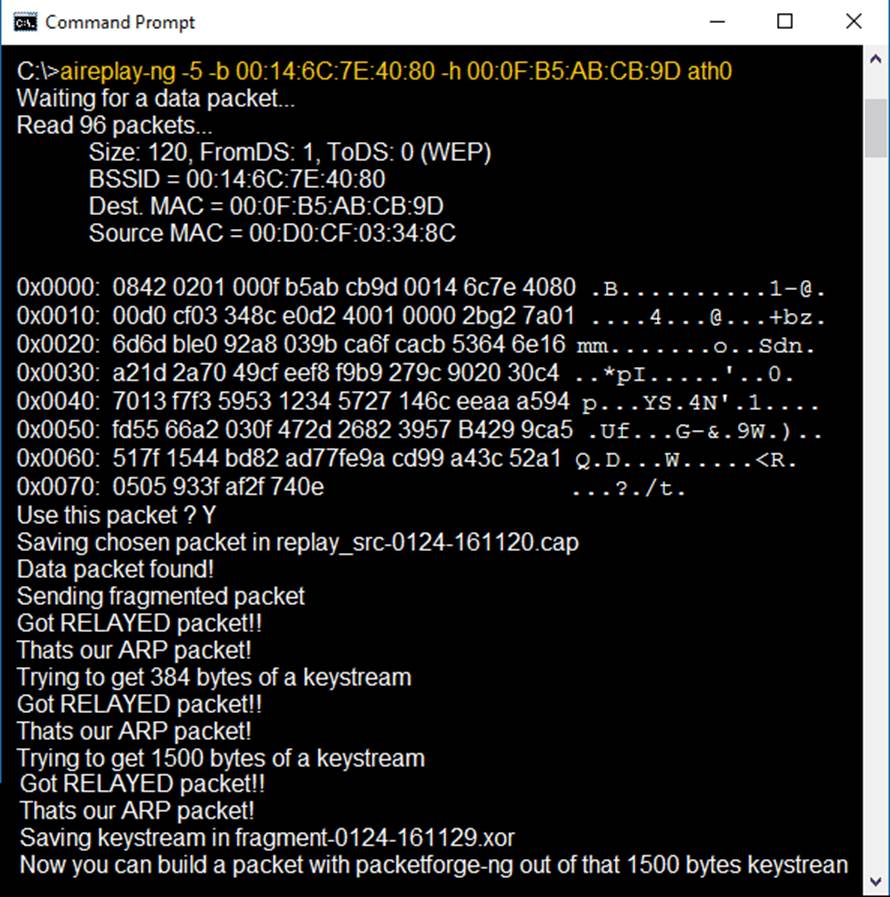
- A . replay_src-0124-161120.cap
- B . fragment-0124-161129.xor
- C . 0505 933f af2f 740e
- D . 0842 0201 000f b5ab cd9d 0014 6c7e 4080
James is an attacker who wants to attack XYZ Inc. He has performed reconnaissance over all the publicly available resources of the company and identified the official company website http://xyz.com. He scanned all the pages of the company website to find for any potential vulnerabilities to exploit. Finally, in the user account login page of the company’s website, he found a user login form which consists of several fields that accepts user inputs like username and password. He also found than any non-validated query that is requested can be directly communicated to the active directory and enable unauthorized users to obtain direct access to the databases. Since James knew an employee named Jason from XYZ Inc., he enters a valid username “jason” and injects “jason)(&))” in the username field. In the password field, James enters “blah” and clicks Submit button. Since the complete URL string entered by James becomes “(& (USER=jason)(&))(PASS=blah)),” only the first filter is processed by the Microsoft Active Directory, that is, the query “(&(USER=jason)(&))” is processed. Since this query always stands true, James successfully logs into the user account without a valid password of Jason.
In the above scenario, identify the type of attack performed by James?
- A . LDAP injection attack
- B . HTML embedding attack
- C . Shell injection attack
- D . File injection attack
An organization has deployed a web application that uses encoding technique before transmitting the data over the Internet. This encoding technique helps the organization to hide the confidential data such as user credentials, email attachments, etc. when in transit. This encoding technique takes 3 bytes of binary data and divides it into four chunks of 6 bits. Each chunk is further encoded into respective printable character.
Identify the encoding technique employed by the organization?
- A . Unicode encoding
- B . Base64 encoding
- C . URL encoding
- D . HTMS encoding
During an internal network audit, you are asked to see if there is any RPC server running on the network and if found, enumerate the associate RPC services.
Which port would you scan to determine the RPC server and which command will you use to enumerate the RPC services?
- A . Port 111, rpcinfo
- B . Port 111, rpcenum
- C . Port 145, rpcinfo
- D . Port 145, rpcenum
The penetration testing team of MirTech Inc. identified the presence of various vulnerabilities in the web application coding. They prepared a detailed report addressing to the web developers regarding the findings. In the report, the penetration testing team advised the web developers to avoid the use of dangerous standard library functions. They also informed the web developers that the web application copies the data without checking whether it fits into the target destination memory and is susceptible in supplying the application with large amount of data.
According to the findings by the penetration testing team, which type of attack was possible on the web application?
- A . Buffer overflow
- B . SQL injection
- C . Cross-site scripting
- D . Denial-of-service
Alisa is a Network Security Manager at Aidos Cyber Security. During a regular network audit, she sent specially crafted ICMP packet fragments with different offset values into the network, causing a system crash.
Which attack Alisa is trying to perform?
- A . Ping-of-death attack
- B . Fraggle attack
- C . Session hijacking
- D . Smurf attack
Latest ECSAv10 Dumps Valid Version with 150 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

