EC-Council CEH-001 Certified Ethical Hacker (CEH) Online Training
EC-Council CEH-001 Online Training
The questions for CEH-001 were last updated at Dec 09,2025.
- Exam Code: CEH-001
- Exam Name: Certified Ethical Hacker (CEH)
- Certification Provider: EC-Council
- Latest update: Dec 09,2025
You want to hide a secret.txt document inside c:windowssystem32tcpip.dll kernel library using ADS streams.
How will you accomplish this?
- A . copy secret.txt c:windowssystem32tcpip.dll kernel>secret.txt
- B . copy secret.txt c:windowssystem32tcpip.dll: secret.txt
- C . copy secret.txt c:windowssystem32tcpip.dll |secret.txt
- D . copy secret.txt >< c:windowssystem32tcpip.dll kernel secret.txt
Most cases of insider abuse can be traced to individuals who are introverted, incapable of dealing with stress or conflict, and frustrated with their job, office politics, and lack of respect or promotion. Disgruntled employees may pass company secrets and intellectual property to competitors for monitory benefits.
Here are some of the symptoms of a disgruntled employee:
a) Frequently leaves work early, arrive late or call in sick
b) Spends time surfing the Internet or on the phone
c) Responds in a confrontational, angry, or overly aggressive way to simple requests or comments
d) Always negative; finds fault with everything
These disgruntled employees are the biggest threat to enterprise security.
How do you deal with these threats? (Select 2 answers)
- A . Limit access to the applications they can run on their desktop computers and enforce strict work hour rules
- B . By implementing Virtualization technology from the desktop to the data centre, organizations can isolate different environments with varying levels of access and security to various employees
- C . Organizations must ensure that their corporate data is centrally managed and delivered to users just and when needed
- D . Limit Internet access, e-mail communications, access to social networking sites and job hunting portals
Peter extracts the SID list from Windows 2008 Server machine using the hacking tool "SIDExtracter". Here is the output of the SIDs:
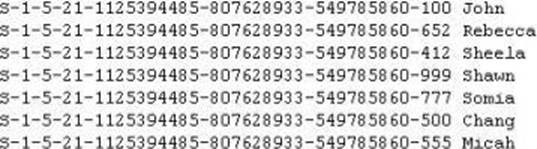
From the above list identify the user account with System Administrator privileges?
- A . John
- B . Rebecca
- C . Sheela
- D . Shawn
- E . Somia
- F . Chang
- G . Micah
Stephanie works as a records clerk in a large office building in downtown Chicago. On Monday, she went to a mandatory security awareness class (Security5) put on by her company’s IT department. During the class, the IT department informed all employees that everyone’s Internet activity was thenceforth going to be monitored.
Stephanie is worried that her Internet activity might give her supervisor reason to write her up, or worse get her fired. Stephanie’s daily work duties only consume about four hours of her time, so she usually spends the rest of the day surfing the web. Stephanie really enjoys surfing the Internet but definitely does not want to get fired for it.
What should Stephanie use so that she does not get in trouble for surfing the Internet?
- A . Stealth IE
- B . Stealth Anonymizer
- C . Stealth Firefox
- D . Cookie Disabler
Google uses a unique cookie for each browser used by an individual user on a computer. This cookie contains information that allows Google to identify records about that user on its database. This cookie is submitted every time a user launches a Google search, visits a site using AdSense etc.
The information stored in Google’s database, identified by the cookie, includes
✑ Everything you search for using Google
✑ Every web page you visit that has Google Adsense ads
How would you prevent Google from storing your search keywords?
- A . Block Google Cookie by applying Privacy and Security settings in your web browser
- B . Disable the Google cookie using Google Advanced Search settings on Google Search page
- C . Do not use Google but use another search engine Bing which will not collect and store your search keywords
- D . Use MAC OS X instead of Windows 7. Mac OS has higher level of privacy controls by default.
Jimmy, an attacker, knows that he can take advantage of poorly designed input validation routines to create or alter SQL commands to gain access to private data or execute commands in the database.
What technique does Jimmy use to compromise a database?
- A . Jimmy can submit user input that executes an operating system command to compromise a target system
- B . Jimmy can gain control of system to flood the target system with requests, preventing legitimate users from gaining access
- C . Jimmy can utilize an incorrect configuration that leads to access with higher-than expected privilege of the database
- D . Jimmy can utilize this particular database threat that is an SQL injection technique to penetrate a target system
Bob waits near a secured door, holding a box. He waits until an employee walks up to the secured door and uses the special card in order to access the restricted area of the target company. Just as the employee opens the door, Bob walks up to the employee (still holding the box) and asks the employee to hold the door open so that he can enter.
What is the best way to undermine the social engineering activity of tailgating?
- A . Issue special cards to access secure doors at the company and provide a one-time only brief description of use of the special card
- B . Educate and enforce physical security policies of the company to all the employees on a regular basis
- C . Setup a mock video camera next to the special card reader adjacent to the secure door
- D . Post a sign that states, "no tailgating" next to the special card reader adjacent to the secure door
Which of the following tool would be considered as Signature Integrity Verifier (SIV)?
- A . Nmap
- B . SNORT
- C . VirusSCAN
- D . Tripwire
How do you defend against ARP Spoofing? Select three.
- A . Use ARPWALL system and block ARP spoofing attacks
- B . Tune IDS Sensors to look for large amount of ARP traffic on local subnets
- C . Use private VLANS
- D . Place static ARP entries on servers, workstation and routers
Latest CEH-001 Dumps Valid Version with 878 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

