EC-Council CEH-001 Certified Ethical Hacker (CEH) Online Training
EC-Council CEH-001 Online Training
The questions for CEH-001 were last updated at Dec 12,2025.
- Exam Code: CEH-001
- Exam Name: Certified Ethical Hacker (CEH)
- Certification Provider: EC-Council
- Latest update: Dec 12,2025
Choose one of the following pseudo codes to describe this statement:
"If we have written 200 characters to the buffer variable, the stack should stop because it cannot hold any more data."
- A . If (I > 200) then exit (1)
- B . If (I < 200) then exit (1)
- C . If (I <= 200) then exit (1)
- D . If (I >= 200) then exit (1)
Which of the following statements would NOT be a proper definition for a Trojan Horse?
- A . An authorized program that has been designed to capture keyboard keystroke while the user is unaware of such activity being performed
- B . An unauthorized program contained within a legitimate program. This unauthorized program performs functions unknown (and probably unwanted) by the user
- C . A legitimate program that has been altered by the placement of unauthorized code within it; this code performs functions unknown (and probably unwanted) by the user
- D . Any program that appears to perform a desirable and necessary function but that (because of unauthorized code within it that is unknown to the user) performs functions unknown (and definitely unwanted) by the user
Syslog is a standard for logging program messages. It allows separation of the software that generates messages from the system that stores them and the software that reports and analyzes them. It also provides devices, which would otherwise be unable to communicate a means to notify administrators of problems or performance.
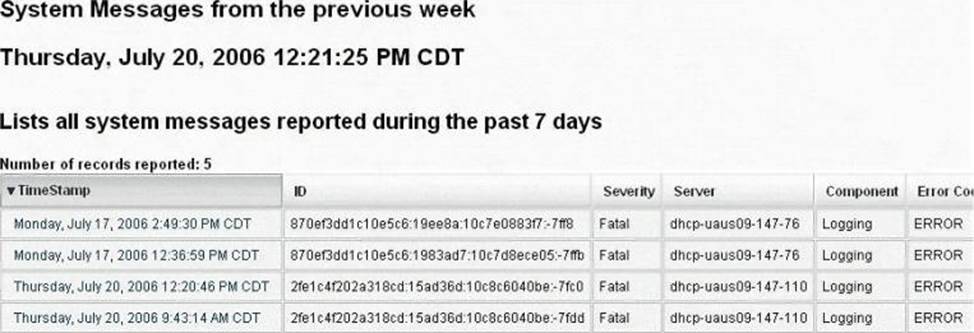
What default port Syslog daemon listens on?
- A . 242
- B . 312
- C . 416
- D . 514
This IDS defeating technique works by splitting a datagram (or packet) into multiple fragments and the IDS will not spot the true nature of the fully assembled datagram. The datagram is not reassembled until it reaches its final destination. It would be a processor-intensive task for IDS to reassemble all fragments itself, and on a busy system the packet will slip through the IDS onto the network.
What is this technique called?
- A . IP Routing or Packet Dropping
- B . IDS Spoofing or Session Assembly
- C . IP Fragmentation or Session Splicing
- D . IP Splicing or Packet Reassembly
Annie has just succeeded in stealing a secure cookie via a XSS attack. She is able to replay the cookie even while the session is invalid on the server.
Why do you think this is possible?
- A . It works because encryption is performed at the application layer (single encryption key)
- B . The scenario is invalid as a secure cookie cannot be replayed
- C . It works because encryption is performed at the network layer (layer 1 encryption)
- D . Any cookie can be replayed irrespective of the session status
More sophisticated IDSs look for common shellcode signatures. But even these systems can be bypassed, by using polymorphic shellcode. This is a technique common among virus writers?it basically hides the true nature of the shellcode in different disguises.
How does a polymorphic shellcode work?
- A . They encrypt the shellcode by XORing values over the shellcode, using loader code to decrypt the shellcode, and then executing the decrypted shellcode
- B . They convert the shellcode into Unicode, using loader to convert back to machine code then executing them
- C . They reverse the working instructions into opposite order by masking the IDS signatures
- D . They compress shellcode into normal instructions, uncompress the shellcode using loader code and then executing the shellcode
Fake Anti-Virus, is one of the most frequently encountered and persistent threats on the web. This malware uses social engineering to lure users into infected websites with a technique called Search Engine Optimization.
Once the Fake AV is downloaded into the user’s computer, the software will scare them into believing their system is infected with threats that do not really exist, and then push users to purchase services to clean up the non-existent threats.
The Fake AntiVirus will continue to send these annoying and intrusive alerts until a payment is made.
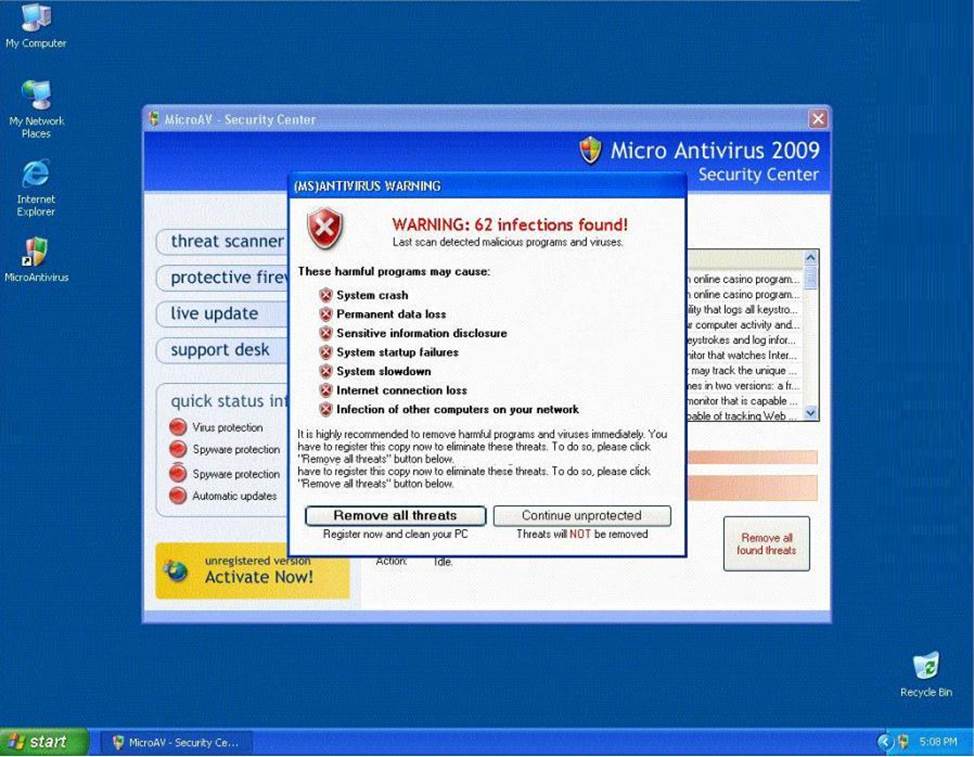
What is the risk of installing Fake AntiVirus?
- A . Victim’s Operating System versions, services running and applications installed will be published on Blogs and Forums
- B . Victim’s personally identifiable information such as billing address and credit card details, may be extracted and exploited by the attacker
- C . Once infected, the computer will be unable to boot and the Trojan will attempt to format the hard disk
- D . Denial of Service attack will be launched against the infected computer crashing other machines on the connected network
Bret is a web application administrator and has just read that there are a number of surprisingly common web application vulnerabilities that can be exploited by unsophisticated attackers with easily available tools on the Internet. He has also read that when an organization deploys a web application, they invite the world to send HTTP requests. Attacks buried in these requests sail past firewalls, filters, platform hardening, SSL, and IDS without notice because they are inside legal HTTP requests. Bret is determined to weed out vulnerabilities.
What are some of the common vulnerabilities in web applications that he should be concerned about?
- A . Non-validated parameters, broken access control, broken account and session management, cross-site scripting and buffer overflows are just a few common vulnerabilities
- B . Visible clear text passwords, anonymous user account set as default, missing latest security patch, no firewall filters set and no SSL configured are just a few common vulnerabilities
- C . No SSL configured, anonymous user account set as default, missing latest security patch, no firewall filters set and an inattentive system administrator are just a few common vulnerabilities
- D . No IDS configured, anonymous user account set as default, missing latest security patch, no firewall filters set and visible clear text passwords are just a few common vulnerabilities
Dan is conducting penetration testing and has found a vulnerability in a Web Application which gave him the sessionID token via a cross site scripting vulnerability. Dan wants to replay this token. However, the session ID manager (on the server) checks the originating IP address as well. Dan decides to spoof his IP address in order to replay the sessionID.
Why do you think Dan might not be able to get an interactive session?
- A . Dan cannot spoof his IP address over TCP network
- B . The scenario is incorrect as Dan can spoof his IP and get responses
- C . The server will send replies back to the spoofed IP address
- D . Dan can establish an interactive session only if he uses a NAT
Latest CEH-001 Dumps Valid Version with 878 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

