EC-Council CEH-001 Certified Ethical Hacker (CEH) Online Training
EC-Council CEH-001 Online Training
The questions for CEH-001 were last updated at Jan 04,2026.
- Exam Code: CEH-001
- Exam Name: Certified Ethical Hacker (CEH)
- Certification Provider: EC-Council
- Latest update: Jan 04,2026
An attacker has successfully compromised a remote computer.
Which of the following comes as one of the last steps that should be taken to ensure that the compromise cannot be traced back to the source of the problem?
- A . Install patches
- B . Setup a backdoor
- C . Install a zombie for DDOS
- D . Cover your tracks
In what stage of Virus life does a stealth virus gets activated with the user performing certain actions such as running an infected program?
- A . Design
- B . Elimination
- C . Incorporation
- D . Replication
- E . Launch
- F . Detection
In the context of password security: a simple dictionary attack involves loading a dictionary file (a text file full of dictionary words) into a cracking application such as L0phtCrack or John the Ripper, and running it against user accounts located by the application. The larger the word and word fragment selection, the more effective the dictionary attack is. The brute force method is the most inclusive – though slow. Usually, it tries every possible letter and number combination in its automated exploration.
If you would use both brute force and dictionary combined together to have variations of words, what would you call such an attack?
- A . Full Blown Attack
- B . Thorough Attack
- C . Hybrid Attack
- D . BruteDict Attack
You want to capture Facebook website traffic in Wireshark.
What display filter should you use that shows all TCP packets that contain the word ‘facebook’?
- A . display==facebook
- B . traffic.content==facebook
- C . tcp contains facebook
- D . list.display.facebook
Jake works as a system administrator at Acme Corp. Jason, an accountant of the firm befriends him at the canteen and tags along with him on the pretext of appraising him about potential tax benefits. Jason waits for Jake to swipe his access card and follows him through the open door into the secure systems area.
How would you describe Jason’s behavior within a security context?
- A . Smooth Talking
- B . Swipe Gating
- C . Tailgating
- D . Trailing
A common technique for luring e-mail users into opening virus-launching attachments is to send messages that would appear to be relevant or important to many of their potential recipients. One way of accomplishing this feat is to make the virus-carrying messages appear to come from some type of business entity retailing sites, UPS, FEDEX, CITIBANK or a major provider of a common service.
Here is a fraudulent e-mail claiming to be from FedEx regarding a package that could not be delivered. This mail asks the receiver to open an attachment in order to obtain the FEDEX tracking number for picking up the package. The attachment contained in this type of e-mail activates a virus.
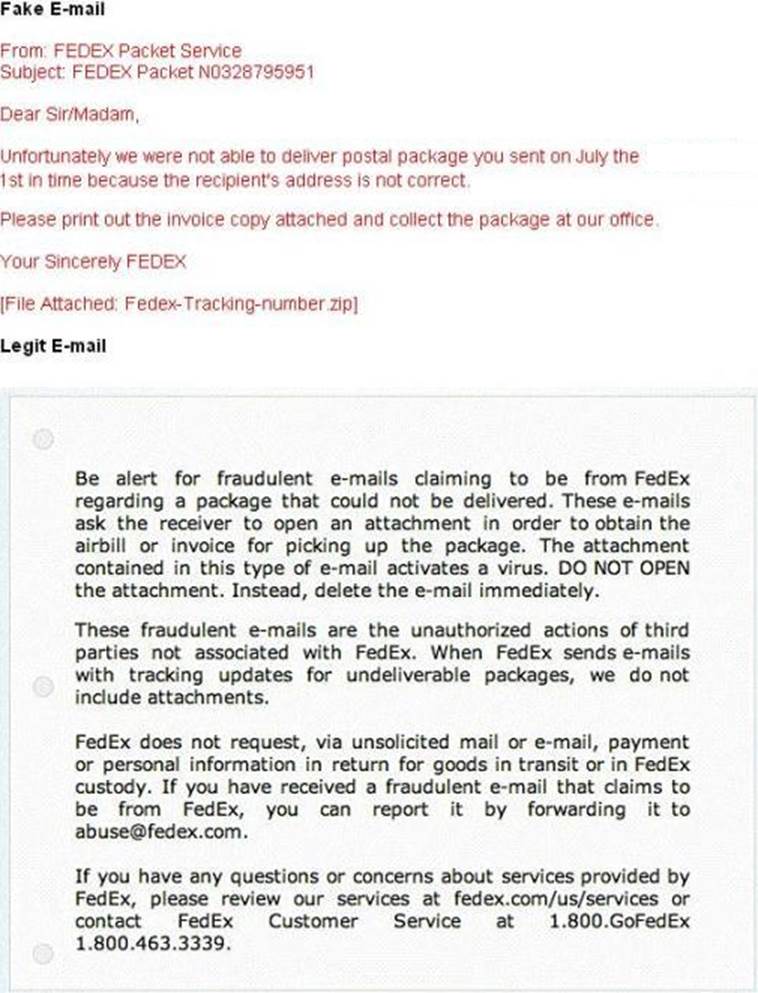
Vendors send e-mails like this to their customers advising them not to open any files attached with the mail, as they do not include attachments.
Fraudulent e-mail and legit e-mail that arrives in your inbox contain the fedex.com as the sender of the mail.
How do you ensure if the e-mail is authentic and sent from fedex.com?
- A . Verify the digital signature attached with the mail, the fake mail will not have Digital ID at all
- B . Check the Sender ID against the National Spam Database (NSD)
- C . Fake mail will have spelling/grammatical errors
- D . Fake mail uses extensive images, animation and flash content
How would you describe an attack where an attacker attempts to deliver the payload over multiple packets over long periods of time with the purpose of defeating simple pattern matching in IDS systems without session reconstruction? A characteristic of this attack would be a continuous stream of small packets.
- A . Session Hijacking
- B . Session Stealing
- C . Session Splicing
- D . Session Fragmentation
This attack uses social engineering techniques to trick users into accessing a fake Web site and divulging personal information. Attackers send a legitimate-looking e-mail asking users to update their information on the company’s Web site, but the URLs in the e-mail actually point to a false Web site.
- A . Wiresharp attack
- B . Switch and bait attack
- C . Phishing attack
- D . Man-in-the-Middle attack
Shayla is an IT security consultant, specializing in social engineering and external penetration tests. Shayla has been hired on by Treks Avionics, a subcontractor for the Department of Defense. Shayla has been given authority to perform any and all tests necessary to audit the company’s network security.
No employees for the company, other than the IT director, know about Shayla’s work she will be doing. Shayla’s first step is to obtain a list of employees through company website contact pages. Then she befriends a female employee of the company through an online chat website. After meeting with the female employee numerous times, Shayla is able to gain her trust and they become friends. One day, Shayla steals the employee’s access badge and uses it to gain unauthorized access to the Treks Avionics offices.
What type of insider threat would Shayla be considered?
- A . She would be considered an Insider Affiliate
- B . Because she does not have any legal access herself, Shayla would be considered an Outside Affiliate
- C . Shayla is an Insider Associate since she has befriended an actual employee
- D . Since Shayla obtained access with a legitimate company badge; she would be considered a Pure Insider
What type of attack is shown in the following diagram?
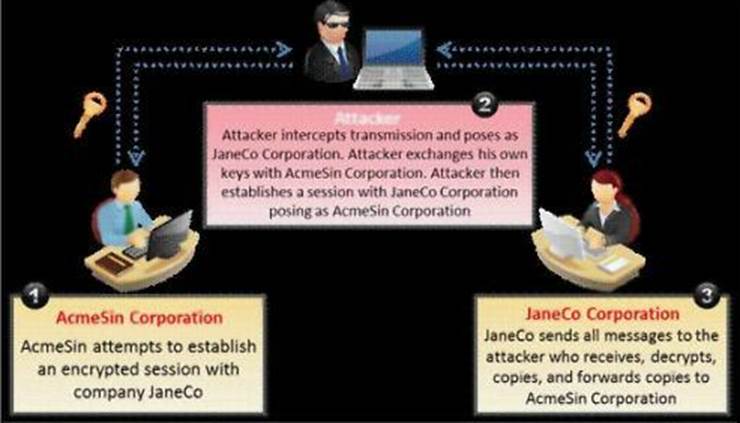
- A . Man-in-the-Middle (MiTM) Attack
- B . Session Hijacking Attack
- C . SSL Spoofing Attack
- D . Identity Stealing Attack
Latest CEH-001 Dumps Valid Version with 878 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

