EC-Council CEH-001 Certified Ethical Hacker (CEH) Online Training
EC-Council CEH-001 Online Training
The questions for CEH-001 were last updated at Dec 17,2025.
- Exam Code: CEH-001
- Exam Name: Certified Ethical Hacker (CEH)
- Certification Provider: EC-Council
- Latest update: Dec 17,2025
What is a sniffing performed on a switched network called?
- A . Spoofed sniffing
- B . Passive sniffing
- C . Direct sniffing
- D . Active sniffing
What does FIN in TCP flag define?
- A . Used to abort a TCP connection abruptly
- B . Used to close a TCP connection
- C . Used to acknowledge receipt of a previous packet or transmission
- D . Used to indicate the beginning of a TCP connection
Which Steganography technique uses Whitespace to hide secret messages?
- A . snow
- B . beetle
- C . magnet
- D . cat
Jack Hacker wants to break into Brown Co.’s computers and obtain their secret double fudge cookie recipe. Jack calls Jane, an accountant at Brown Co., pretending to be an administrator from Brown Co. Jack tells Jane that there has been a problem with some accounts and asks her to verify her password with him ”just to double check our records.” Jane does not suspect anything amiss, and parts with her password. Jack can now access Brown Co.’s computers with a valid user name and password, to steal the cookie recipe.
What kind of attack is being illustrated here?
- A . Reverse Psychology
- B . Reverse Engineering
- C . Social Engineering
- D . Spoofing Identity
- E . Faking Identity
Which of the following type of scanning utilizes automated process of proactively identifying vulnerabilities of the computing systems present on a network?
- A . Port Scanning
- B . Single Scanning
- C . External Scanning
- D . Vulnerability Scanning
How many bits encryption does SHA-1 use?
- A . 64 bits
- B . 128 bits
- C . 256 bits
- D . 160 bits
You receive an e-mail with the following text message.
"Microsoft and HP today warned all customers that a new, highly dangerous virus has been discovered which will erase all your files at midnight. If there’s a file called hidserv.exe on your computer, you have been infected and your computer is now running a hidden server that allows hackers to access your computer. Delete the file immediately. Please also pass this message to all your friends and colleagues as soon as possible."
You launch your antivirus software and scan the suspicious looking file hidserv.exe located in c:windows directory and the AV comes out clean meaning the file is not infected. You view the file signature and confirm that it is a legitimate Windows system file "Human Interface Device Service".
What category of virus is this?
- A . Virus hoax
- B . Spooky Virus
- C . Stealth Virus
- D . Polymorphic Virus
You run nmap port Scan on 10.0.0.5 and attempt to gain banner/server information from services running on ports 21, 110 and 123.
Here is the output of your scan results:
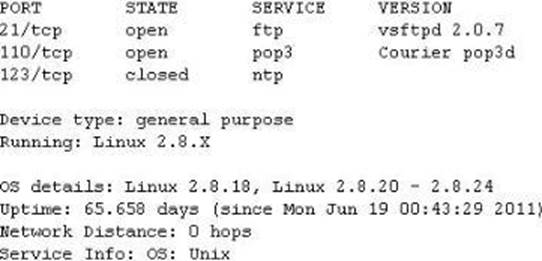
Which of the following nmap command did you run?
- A . nmap -A -sV -p21, 110, 123 10.0.0.5
- B . nmap -F -sV -p21, 110, 123 10.0.0.5
- C . nmap -O -sV -p21, 110, 123 10.0.0.5
- D . nmap -T -sV -p21, 110, 123 10.0.0.5
Stephanie works as senior security analyst for a manufacturing company in Detroit. Stephanie manages network security throughout the organization. Her colleague Jason told her in confidence that he was able to see confidential corporate information posted on the external website http://www.jeansclothesman.com. He tries random URLs on the company’s website and finds confidential information leaked over the web. Jason says this happened about a month ago. Stephanie visits the said URLs, but she finds nothing. She is very concerned about this, since someone should be held accountable if there was sensitive information posted on the website.
Where can Stephanie go to see past versions and pages of a website?
- A . She should go to the web page Samspade.org to see web pages that might no longer be on the website
- B . If Stephanie navigates to Search.com; she will see old versions of the company website
- C . Stephanie can go to Archive.org to see past versions of the company website
- D . AddressPast.com would have any web pages that are no longer hosted on the company’s website
What is the correct command to run Netcat on a server using port 56 that spawns command shell when connected?
- A . nc -port 56 -s cmd.exe
- B . nc -p 56 -p -e shell.exe
- C . nc -r 56 -c cmd.exe
- D . nc -L 56 -t -e cmd.exe
Latest CEH-001 Dumps Valid Version with 878 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

