EC-Council CEH-001 Certified Ethical Hacker (CEH) Online Training
EC-Council CEH-001 Online Training
The questions for CEH-001 were last updated at Dec 16,2025.
- Exam Code: CEH-001
- Exam Name: Certified Ethical Hacker (CEH)
- Certification Provider: EC-Council
- Latest update: Dec 16,2025
While performing a ping sweep of a local subnet you receive an ICMP reply of Code 3/Type 13 for all the pings you have sent out.
What is the most likely cause of this?
- A . The firewall is dropping the packets
- B . An in-line IDS is dropping the packets
- C . A router is blocking ICMP
- D . The host does not respond to ICMP packets
You are the Security Administrator of Xtrinity, Inc. You write security policies and conduct assessments to protect the company’s network. During one of your periodic checks to see how well policy is being observed by the employees, you discover an employee has attached cell phone 3G modem to his telephone line and workstation. He has used this cell phone 3G modem to dial in to his workstation, thereby bypassing your firewall. A security breach has occurred as a direct result of this activity. The employee explains that he used the modem because he had to download software for a department project.
How would you resolve this situation?
- A . Reconfigure the firewall
- B . Enforce the corporate security policy
- C . Install a network-based IDS
- D . Conduct a needs analysis
The SYN flood attack sends TCP connections requests faster than a machine can process them.
✑ Attacker creates a random source address for each packet
✑ SYN flag set in each packet is a request to open a new connection to the server from the spoofed IP address
✑ Victim responds to spoofed IP address, then waits for confirmation that never arrives (timeout wait is about 3 minutes)
✑ Victim’s connection table fills up waiting for replies and ignores new connections
✑ Legitimate users are ignored and will not be able to access the server
How do you protect your network against SYN Flood attacks?
- A . SYN cookies. Instead of allocating a record, send a SYN-ACK with a carefully constructed sequence number generated as a hash of the clients IP address, port number, and other information. When the client responds with a normal ACK, that special sequence number will be included, which the server then verifies. Thus, the server first allocates memory on the third packet of the handshake, not the first.
- B . RST cookies – The server sends a wrong SYN/ACK back to the client. The client should then generate a RST packet telling the server that something is wrong. At this point, the server knows the client is valid and will now accept incoming connections from that client normally
- C . Check the incoming packet’s IP address with the SPAM database on the Internet and enable the filter using ACLs at the Firewall
- D . Stack Tweaking. TCP stacks can be tweaked in order to reduce the effect of SYN floods. Reduce the timeout before a stack frees up the memory allocated for a connection
- E . Micro Blocks. Instead of allocating a complete connection, simply allocate a micro record of 16-bytes for the incoming SYN object
Which type of scan does NOT open a full TCP connection?
- A . Stealth Scan
- B . XMAS Scan
- C . Null Scan
- D . FIN Scan
Vulnerability scanners are automated tools that are used to identify vulnerabilities and misconfigurations of hosts. They also provide information regarding mitigating discovered vulnerabilities.
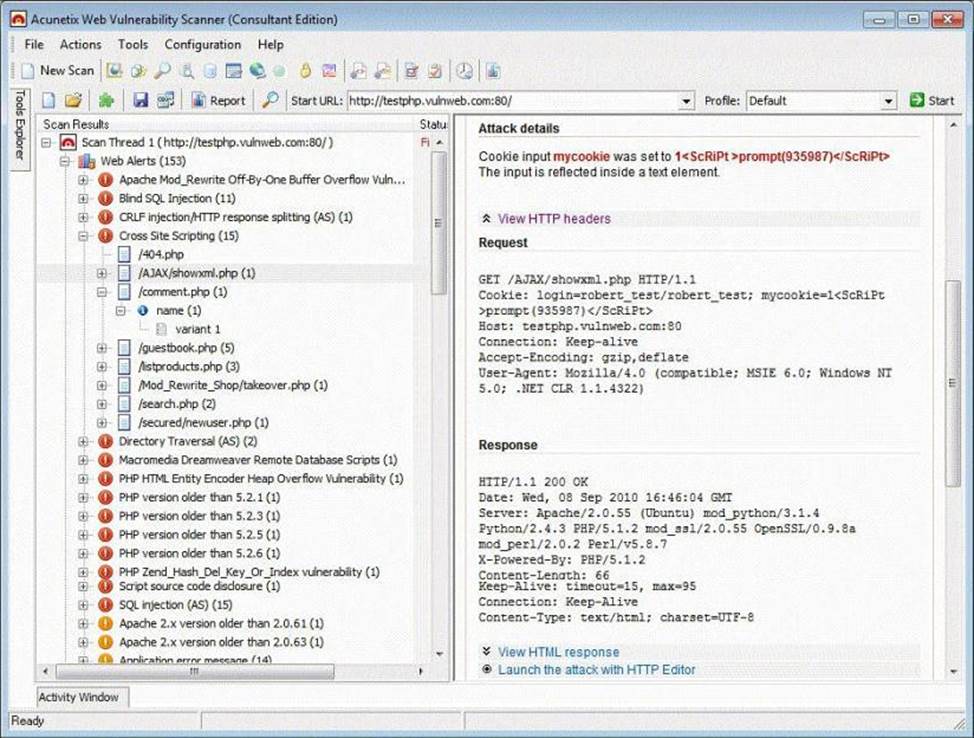
Which of the following statements is incorrect?
- A . Vulnerability scanners attempt to identify vulnerabilities in the hosts scanned.
- B . Vulnerability scanners can help identify out-of-date software versions, missing patches, or system upgrades
- C . They can validate compliance with or deviations from the organization’s security policy
- D . Vulnerability scanners can identify weakness and automatically fix and patch the vulnerabilities without user intervention
TCP/IP Session Hijacking is carried out in which OSI layer?
- A . Datalink layer
- B . Transport layer
- C . Network layer
- D . Physical layer
This attack technique is used when a Web application is vulnerable to an SQL Injection but the results of the Injection are not visible to the attacker.
- A . Unique SQL Injection
- B . Blind SQL Injection
- C . Generic SQL Injection
- D . Double SQL Injection
What is War Dialing?
- A . War dialing involves the use of a program in conjunction with a modem to penetrate the modem/PBX-based systems
- B . War dialing is a vulnerability scanning technique that penetrates Firewalls
- C . It is a social engineering technique that uses Phone calls to trick victims
- D . Involves IDS Scanning Fragments to bypass Internet filters and stateful Firewalls
Lori is a Certified Ethical Hacker as well as a Certified Hacking Forensics Investigator working as an IT security consultant. Lori has been hired on by Kiley Innovators, a large marketing firm that recently underwent a string of thefts and corporate espionage incidents. Lori is told that a rival marketing company came out with an exact duplicate product right before Kiley Innovators was about to release it. The executive team believes that an employee is leaking information to the rival company. Lori questions all employees, reviews server logs, and firewall logs; after which she finds nothing. Lori is then given permission to search through the corporate email system. She searches by email being sent to and sent from the rival marketing company.
She finds one employee that appears to be sending very large email to this other marketing company, even though they should have no reason to be communicating with them. Lori tracks down the actual emails sent and upon opening them, only finds picture files attached to them. These files seem perfectly harmless, usually containing some kind of joke. Lori decides to use some special software to further examine the pictures and finds that each one had hidden text that was stored in each picture.
What technique was used by the Kiley Innovators employee to send information to the rival marketing company?
- A . The Kiley Innovators employee used cryptography to hide the information in the emails sent
- B . The method used by the employee to hide the information was logical watermarking
- C . The employee used steganography to hide information in the picture attachments
- D . By using the pictures to hide information, the employee utilized picture fuzzing
Which type of hacker represents the highest risk to your network?
- A . black hat hackers
- B . grey hat hackers
- C . disgruntled employees
- D . script kiddies
Latest CEH-001 Dumps Valid Version with 878 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

