EC-Council 412-79V10 EC-Council Certified Security Analyst (ECSA) V10 Online Training
EC-Council 412-79V10 Online Training
The questions for 412-79V10 were last updated at Dec 22,2025.
- Exam Code: 412-79V10
- Exam Name: EC-Council Certified Security Analyst (ECSA) V10
- Certification Provider: EC-Council
- Latest update: Dec 22,2025
Identify the policy that defines the standards for the organizational network connectivity and security standards for computers that are connected in the organizational network.
- A . Information-Protection Policy
- B . Special-Access Policy
- C . Remote-Access Policy
- D . Acceptable-Use Policy
By default, the TFTP server listens on UDP port 69.
Which of the following utility reports the port status of target TCP and UDP ports on a local or a remote computer and is used to troubleshoot TCP/IP connectivity issues?
- A . PortQry
- B . Netstat
- C . Telnet
- D . Tracert
Traffic on which port is unusual for both the TCP and UDP ports?
- A . Port 81
- B . Port 443
- C . Port 0
- D . Port 21
Identify the type of testing that is carried out without giving any information to the employees or administrative head of the organization.
- A . Unannounced Testing
- B . Double Blind Testing
- C . Announced Testing
- D . Blind Testing
Identify the person who will lead the penetration-testing project and be the client point of contact.
- A . Database Penetration Tester
- B . Policy Penetration Tester
- C . Chief Penetration Tester
- D . Application Penetration Tester
ARP spoofing is a technique whereby an attacker sends fake ("spoofed") Address Resolution Protocol (ARP) messages onto a Local Area Network. Generally, the aim is to associate the attacker’s MAC address with the IP address of another host (such as the default gateway), causing any traffic meant for that IP address to be sent to the attacker instead.
ARP spoofing attack is used as an opening for other attacks.
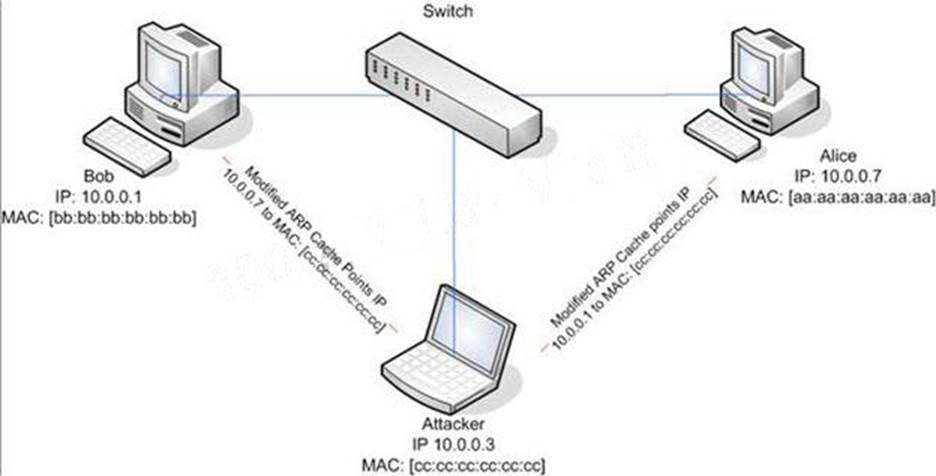
What type of attack would you launch after successfully deploying ARP spoofing?
- A . Parameter Filtering
- B . Social Engineering
- C . Input Validation
- D . Session Hijacking
Which of the following password hashing algorithms is used in the NTLMv2 authentication mechanism?
- A . AES
- B . DES (ECB mode)
- C . MD5
- D . RC5
Which of the following will not handle routing protocols properly?
- A . “Internet-router-firewall-net architecture”
- B . “Internet-firewall-router-net architecture”
- C . “Internet-firewall -net architecture”
- D . “Internet-firewall/router(edge device)-net architecture”
TCP/IP provides a broad range of communication protocols for the various applications on the network. The TCP/IP model has four layers with major protocols included within each layer.
Which one of the following protocols is used to collect information from all the network devices?
- A . Simple Network Management Protocol (SNMP)
- B . Network File system (NFS)
- C . Internet Control Message Protocol (ICMP)
- D . Transmission Control Protocol (TCP)
The term social engineering is used to describe the various tricks used to fool people (employees, business partners, or customers) into voluntarily giving away information that would not normally be known to the general public.
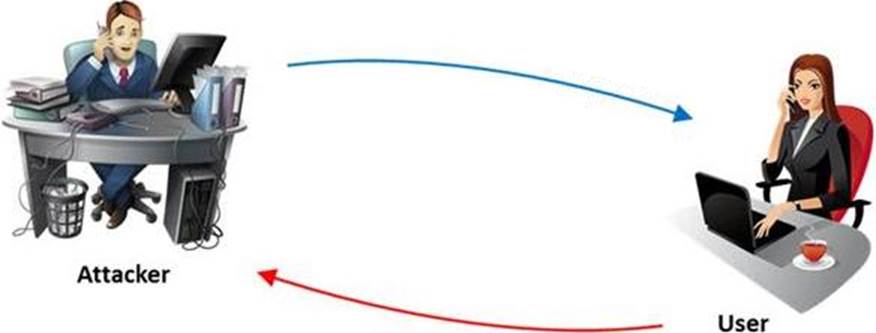
What is the criminal practice of social engineering where an attacker uses the telephone system in an attempt to scam the user into surrendering private information?
- A . Phishing
- B . Spoofing
- C . Tapping
- D . Vishing
Latest 412-79V10 Dumps Valid Version with 201 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

