EC-Council 412-79V10 EC-Council Certified Security Analyst (ECSA) V10 Online Training
EC-Council 412-79V10 Online Training
The questions for 412-79V10 were last updated at Dec 11,2025.
- Exam Code: 412-79V10
- Exam Name: EC-Council Certified Security Analyst (ECSA) V10
- Certification Provider: EC-Council
- Latest update: Dec 11,2025
Frank is working on a vulnerability assessment for a company on the West coast. The company hired Frank to assess its network security through scanning, pen tests, and vulnerability assessments. After discovering numerous known vulnerabilities detected by a temporary IDS he set up, he notices a number of items that show up as unknown but questionable in the logs.
He looks up the behavior on the Internet, but cannot find anything related.
What organization should Frank submit the log to find out if it is a new vulnerability or not?
- A . CVE
- B . IANA
- C . RIPE
- D . APIPA
What is a difference between host-based intrusion detection systems (HIDS) and network-based intrusion detection systems (NIDS)?
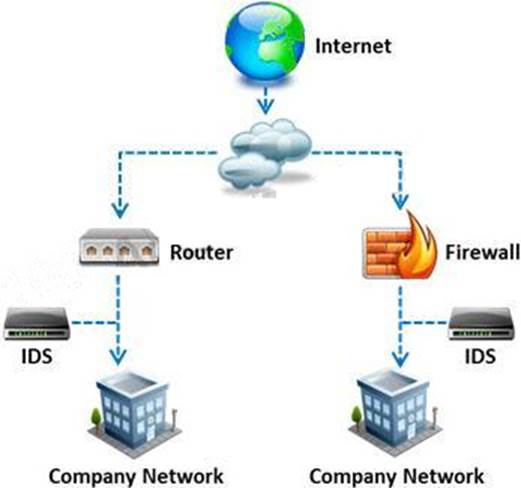
- A . NIDS are usually a more expensive solution to implement compared to HIDS.
- B . Attempts to install Trojans or backdoors cannot be monitored by a HIDS whereas NIDS can monitor and stop such intrusion events.
- C . NIDS are standalone hardware appliances that include network intrusion detection capabilities whereas HIDS consist of software agents installed on individual computers within the system.
- D . HIDS requires less administration and training compared to NIDS.
A chipset is a group of integrated circuits that are designed to work together and are usually marketed as a single product.” It is generally the motherboard chips or the chips used on the expansion card.
Which one of the following is well supported in most wireless applications?
- A . Orinoco chipsets
- B . Prism II chipsets
- C . Atheros Chipset
- D . Cisco chipset
In the process of hacking a web application, attackers manipulate the HTTP requests to subvert the application authorization schemes by modifying input fields that relate to the user ID, username, access group, cost, file names, file identifiers, etc.
They first access the web application using a low privileged account and then escalate privileges to access protected resources.
What attack has been carried out?
- A . XPath Injection Attack
- B . Authorization Attack
- C . Authentication Attack
- D . Frame Injection Attack
In which of the following IDS evasion techniques does IDS reject the packets that an end system accepts?
- A . IPS evasion technique
- B . IDS evasion technique
- C . UDP evasion technique
- D . TTL evasion technique
Besides the policy implications of chat rooms, Internet Relay Chat (IRC) is frequented by attackers and used as a command and control mechanism.
IRC normally uses which one of the following TCP ports?
- A . 6566 TCP port
- B . 6771 TCP port
- C . 6667 TCP port
- D . 6257 TCP port
Internet Control Message Protocol (ICMP) messages occur in many situations, such as whenever a datagram cannot reach the destination or the gateway does not have the buffering capacity to forward a datagram.
Each ICMP message contains three fields: type, code, and checksum. Different types of Internet Control Message Protocols (ICMPs) are identified by a TYPE field.
If the destination is not reachable, which one of the following are generated?
- A . Type 8 ICMP codes
- B . Type 12 ICMP codes
- C . Type 3 ICMP codes
- D . Type 7 ICMP codes
John and Hillary works at the same department in the company. John wants to find out Hillary’s network password so he can take a look at her documents on the file server. He enables Lophtcrack program to sniffing mode. John sends Hillary an email with a link to Error! Reference source not found.
What information will he be able to gather from this?
- A . The SID of Hillary’s network account
- B . The network shares that Hillary has permissions
- C . The SAM file from Hillary’s computer
- D . Hillary’s network username and password hash
Harold is a security analyst who has just run the rdisk /s command to grab the backup SAM file on a computer.
Where should Harold navigate on the computer to find the file?
- A . %systemroot%LSA
- B . %systemroot%repair
- C . %systemroot%system32driversetc
- D . %systemroot%system32LSA
Which one of the following log analysis tools is a Cisco Router Log Format log analyzer and it parses logs, imports them into a SQL database (or its own built-in database), aggregates them, and generates the dynamically filtered reports, all through a web interface?
- A . Event Log Tracker
- B . Sawmill
- C . Syslog Manager
- D . Event Log Explorer
Latest 412-79V10 Dumps Valid Version with 201 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

