EC-Council 312-50v12 Certified Ethical Hacker Exam (CEHv12) Online Training
EC-Council 312-50v12 Online Training
The questions for 312-50v12 were last updated at Dec 15,2025.
- Exam Code: 312-50v12
- Exam Name: Certified Ethical Hacker Exam (CEHv12)
- Certification Provider: EC-Council
- Latest update: Dec 15,2025
A large mobile telephony and data network operator has a data center that houses network elements. These are essentially large computers running on Linux. The perimeter of the data center is secured with firewalls and IPS systems.
What is the best security policy concerning this setup?
- A . Network elements must be hardened with user ids and strong passwords. Regular security tests and audits should be performed.
- B . As long as the physical access to the network elements is restricted, there is no need for additional measures.
- C . There is no need for specific security measures on the network elements as long as firewalls and IPS systems exist.
- D . The operator knows that attacks and down time are inevitable and should have a backup site.
An attacker with access to the inside network of a small company launches a successful STP manipulation attack.
What will he do next?
- A . He will create a SPAN entry on the spoofed root bridge and redirect traffic to his computer.
- B . He will activate OSPF on the spoofed root bridge.
- C . He will repeat this action so that it escalates to a DoS attack.
- D . He will repeat the same attack against all L2 switches of the network.
Which system consists of a publicly available set of databases that contain domain name registration contact information?
- A . WHOIS
- B . CAPTCHA
- C . IANA
- D . IETF
What is the proper response for a NULL scan if the port is closed?
- A . SYN
- B . ACK
- C . FIN
- D . PSH
- E . RST
- F . No response
Shellshock allowed an unauthorized user to gain access to a server. It affected many Internet-facing services, which OS did it not directly affect?
- A . Linux
- B . Unix
- C . OS X
- D . Windows
Which of the following is a command line packet analyzer similar to GUI-based Wireshark?
- A . nessus
- B . tcpdump
- C . ethereal
- D . jack the ripper
Which regulation defines security and privacy controls for Federal information systems and organizations?
- A . HIPAA
- B . EU Safe Harbor
- C . PCI-DSS
- D . NIST-800-53
An attacker, using a rogue wireless AP, performed an MITM attack and injected an HTML
code to embed a malicious applet in all HTTP connections.
When users accessed any page, the applet ran and exploited many machines.
Which one of the following tools the hacker probably used to inject HTML code?
- A . Wireshark
- B . Ettercap
- C . Aircrack-ng
- D . Tcpdump
You have successfully comprised a server having an IP address of 10.10.0.5. You would like to enumerate all machines in the same network quickly.
What is the best Nmap command you will use?
- A . nmap -T4 -q 10.10.0.0/24
- B . nmap -T4 -F 10.10.0.0/24
- C . nmap -T4 -r 10.10.1.0/24
- D . nmap -T4 -O 10.10.0.0/24
Peter extracts the SIDs list from Windows 2000 Server machine using the hacking tool "SIDExtractor".
Here is the output of the SIDs:
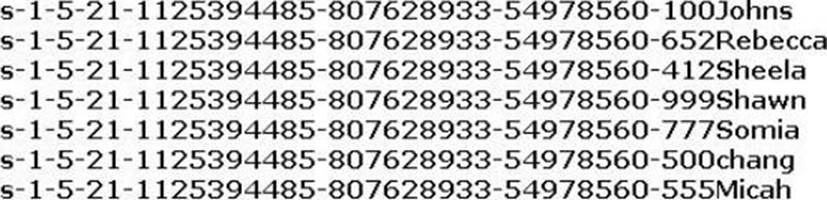
From the above list identify the user account with System Administrator privileges.
- A . John
- B . Rebecca
- C . Sheela
- D . Shawn
- E . Somia
- F . Chang
- G . Micah
Latest 312-50v12 Dumps Valid Version with 503 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

