EC-Council 312-50v11 Certified Ethical Hacker Exam – C|EH v11 Online Training
EC-Council 312-50v11 Online Training
The questions for 312-50v11 were last updated at Dec 15,2025.
- Exam Code: 312-50v11
- Exam Name: Certified Ethical Hacker Exam - C|EH v11
- Certification Provider: EC-Council
- Latest update: Dec 15,2025
You want to do an ICMP scan on a remote computer using hping2 .
What is the proper syntax?
- A . hping2 host.domain.com
- B . hping2 –set-ICMP host.domain.com
- C . hping2 -i host.domain.com
- D . hping2 -1 host.domain.com
Jake, a professional hacker, installed spyware on a target iPhone to spy on the target user’s activities. He can take complete control of the target mobile device by jailbreaking the device remotely and record audio, capture screenshots, and monitor all phone calls and SMS messages .
What is the type of spyware that Jake used to infect the target device?
- A . DroidSheep
- B . Androrat
- C . Zscaler
- D . Trident
You are programming a buffer overflow exploit and you want to create a NOP sled of 200 bytes in the program exploit.c
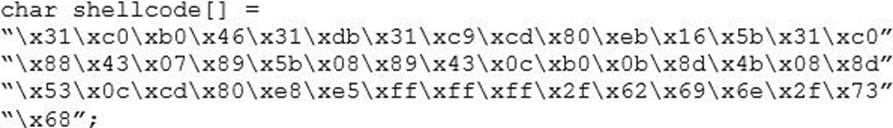
What is the hexadecimal value of NOP instruction?
- A . 0x60
- B . 0x80
- C . 0x70
- D . 0x90
How can you determine if an LM hash you extracted contains a password that is less than 8 characters long?
- A . There is no way to tell because a hash cannot be reversed
- B . The right most portion of the hash is always the same
- C . The hash always starts with AB923D
- D . The left most portion of the hash is always the same
- E . A portion of the hash will be all 0’s
You are tasked to perform a penetration test. While you are performing information gathering, you find an employee list in Google. You find the receptionist’s email, and you send her an email changing the source email to her boss’s email (boss@company). In this email, you ask for a pdf with information. She reads your email and sends back a pdf with links. You exchange the pdf links with your malicious links (these links contain malware) and send back the modified pdf, saying that the links don’t work. She reads your email, opens the links, and her machine gets infected. You now have access to the company network .
What testing method did you use?
- A . Social engineering
- B . Piggybacking
- C . Tailgating
- D . Eavesdropping
BitLocker encryption has been implemented for all the Windows-based computers in an organization. You are concerned that someone might lose their cryptographic key. Therefore, a mechanism was implemented to recover the keys from Active Directory .
What is this mechanism called in cryptography?
- A . Key archival
- B . Key escrow.
- C . Certificate rollover
- D . Key renewal
Attempting an injection attack on a web server based on responses to True/False questions is called which of the following?
- A . Compound SQLi
- B . Blind SQLi
- C . Classic SQLi
- D . DMS-specific SQLi
Your company was hired by a small healthcare provider to perform a technical assessment on the network.
What is the best approach for discovering vulnerabilities on a Windows-based computer?
- A . Use the built-in Windows Update tool
- B . Use a scan tool like Nessus
- C . Check MITRE.org for the latest list of CVE findings
- D . Create a disk image of a clean Windows installation
Which results will be returned with the following Google search query?
site:target.com C site: Marketing.target.com accounting
- A . Results from matches on the site marketing.target.com that are in the domain target.com but do not include the word accounting.
- B . Results matching all words in the query.
- C . Results for matches on target.com and Marketing.target.com that include the word “accounting”
- D . Results matching “accounting” in domain target.com but not on the site Marketing.target.com
Jack, a professional hacker, targets an organization and performs vulnerability scanning on the target web server to identify any possible weaknesses, vulnerabilities, and misconfigurations. In this process, Jack uses an automated tool that eases his work and performs vulnerability scanning to find hosts, services, and other vulnerabilities in the target server .
Which of the following tools is used by Jack to perform vulnerability scanning?
- A . Infoga
- B . WebCopier Pro
- C . Netsparker
- D . NCollector Studio
Latest 312-50v11 Dumps Valid Version with 432 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

