EC-Council 312-50v10 Certified Ethical Hacker Exam (C|EH v10) Online Training
EC-Council 312-50v10 Online Training
The questions for 312-50v10 were last updated at Dec 22,2025.
- Exam Code: 312-50v10
- Exam Name: Certified Ethical Hacker Exam (C|EH v10)
- Certification Provider: EC-Council
- Latest update: Dec 22,2025
Which utility will tell you in real time which ports are listening or in another state?
- A . Netsat
- B . Loki
- C . Nmap
- D . TCP View
What is the least important information when you analyze a public IP address in a security alert?
- A . ARP
- B . Who is
- C . DNS
- D . Geolocation
Emil uses nmap to scan two hosts using this command:
nmap -sS -T 4 -O 192.168.99.1 192.168.99.7
He receives this output:
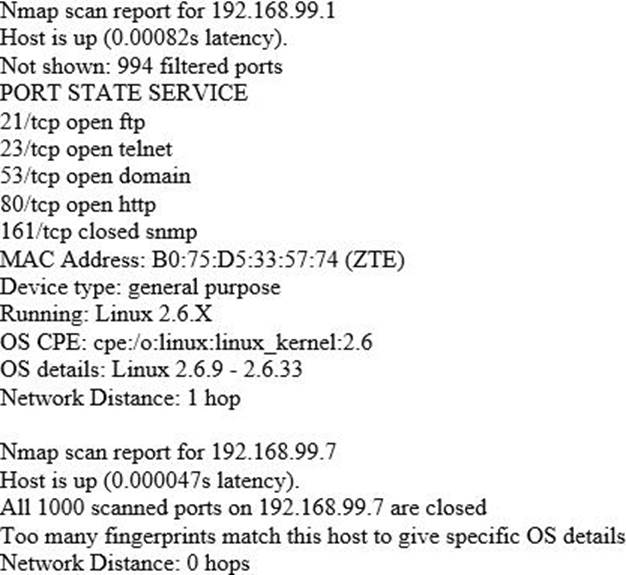
What is his conclusion?
- A . Host 192.168.99.7isaniPad.
- B . He performed a SYN scan and OSs canon hosts 192.16899.1 and 192.168.99.7
- C . Host 192.168.99.1is the host that he launched the scan from.
- D . Host 192.168.99.7is down.
PGP, SSL, and IKE are all examples of which type of cryptography?
- A . Hash Algorithm
- B . Digest
- C . Secret Key
- D . Public Key
An IT employee got a call from one of our best customers. The caller wanted to know about the company’s network infrastructure, systems, and team. New opportunities of integration are insight for both company and customer.
What should this employee do?
- A . The employees cannot provide any information; but, anyway, he/she will provide the name of the person in charge.
- B . Since the company’s policy is all about Customer Service, he/she will provide information.
- C . Disregarding the call, the employee should hang up.
- D . The employee should not provide any information without previous management authorization
While performing online banking using a Web browser, a user receives an email that contains a link to an
interesting Website. When the user click son the link, another Web browser session starts and displays
a video of cats playing a piano. The next business day, the user receives what looks like an email from
his bank, indicating that his bank account has been accessed from a foreign country. The email asks the
user to call his bank and verify the authorization of a funds transfer that took place.
What Web browser-based security vulnerability was exploited to compromise the user?
- A . Cross-Site Request Forgery
- B . Cross-Site Scripting
- C . Clickjacking
- D . Web form input validation
You have successfully comprised a server having an IP address of 10.10.0.5. You would like to enumerate all machines in the same network quickly.
What is the best Nmap command you will use?
- A . nmap -T4 -q 10.10.0.0/ 24
- B . nmap -T4 -F 10.10.0.0/ 24
- C . nmap -T4 -r 10.10.1.0/ 24
- D . nmap -T4 -0 10.10.0.0/ 24
A penetration tester is conducting a ports canon a specific host. The tester found several ports opened that were confusing in concluding the Operating System (OS) version installed.
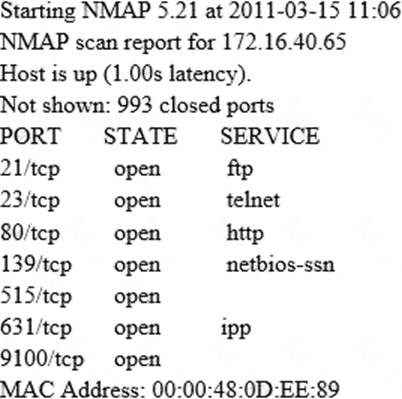
Considering that NMAP result below, which of the following is likely to be installed on the target machine by the OS?
- A . The host is likely a Linux machine.
- B . The host is likely a printer.
- C . The host is likely a router.
- D . The host is likely a Windows machine.
Which of the following areas is considered a strength of symmetric key cryptography when compared with asymmetric algorithms?
- A . Scalability
- B . Speed
- C . Key distribution
- D . Security
Which tool allows analysts and pen testers to examine links between data using graphs and link analysis?
- A . Metasploit
- B . Cain & Abel
- C . Malte go
- D . Wire shark
Latest 312-50v10 Dumps Valid Version with 736 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

