EC-Council 312-50v10 Certified Ethical Hacker Exam (C|EH v10) Online Training
EC-Council 312-50v10 Online Training
The questions for 312-50v10 were last updated at Dec 23,2025.
- Exam Code: 312-50v10
- Exam Name: Certified Ethical Hacker Exam (C|EH v10)
- Certification Provider: EC-Council
- Latest update: Dec 23,2025
Peter is surfing the internet looking for if main about DX Company.
Which hacking process is Peer doing?
- A . Scanning
- B . Footprinting
- C . Enumeration
- D . System Hacking
A company’s security policy states that all Web browsers must automatically delete their HTTP browser cookies upon terminating.
What sort of security breach is this policy attempting to mitigate?
- A . Attempts by attackers to access the user and password information stored in the company’s SQL database.
- B . Attempts by attackers to access Websites that trust the Web browser user by stealing the user’s authentication credentials.
- C . Attempts by attackers to access password stored on the user’s computer without the user’s knowledge
- D . Attempts by attackers to determine the user’s Web browser usage patterns, including when sites were visited and for how long.
Peter issuing the internet looking for i format in about DX Company.
Which hacking process is Peer doing?
- A . Scanning
- B . Footprinting
- C . Enumeration
- D . System Hacking
Port scanning can be used as part of a technical assessment to determine network vulnerabilities. The TCP XMAS scan is used to identify listening ports on the targeted system.
If a scanned port is open, what happens?
- A . The port will ignore the packets.
- B . The port will send an RST.
- C . The port will send an ACK.
- D . The port will send a SYN
An LDAP directory can be used to store information similar to a SQL database. LDAP uses a______ database structure instead of SQL’s________ structure.
Because of this, LDAP has difficulty representing many-to-one relationships.
- A . Strict, Abstract
- B . Simple, Complex
- C . Relational, Hierarchical
- D . Hierarchical, Relational
You want to analyze packets on your wireless network.
Which program would you use?
- A . Wireshark with Airpcap
- B . Airsnort with Airpcap
- C . Wireshark with Winpcap
- D . Ethereal with Winpcap
What is not a PCI compliance recommendation?
- A . Use a firewall between the pubic network and the payment card data.
- B . Use encryption to protect all transmission of cardholder data over any public network.
- C . Rotate employees handling credit card transactions on a yearly basis to different departments.
- D . Limit access to cardholder data to as few individuals as possible.
An attacker scans a host with the below command.
Which three flags are set? (Choose three.)
#nmap-sXhost.domain.com
- A . This is ACK scan. ACK flag is set
- B . This is Xmas scan. SYN and ACK flags are set
- C . This is Xmas scan. URG, PUSH and FIN are set
- D . This is SYN scan. SYN flag is set
A hacker has managed to gain access to a Linux host and stolen the password file from/etc/passwd.
How can he use it?
- A . The file reveals the passwords to the root user only.
- B . The password file does not contain the passwords themselves.
- C . He cannot read it because it is encrypted
- D . He can open it and read the user ids and corresponding passwords.
Which of the following parameters describe LM Hash (see exhibit):
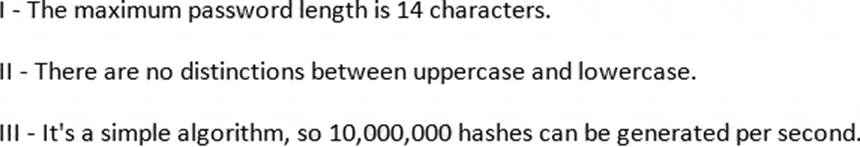
- A . II
- B . I
- C . I, II, and III
- D . I and II
Latest 312-50v10 Dumps Valid Version with 736 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

