EC-Council 312-39 Certified SOC Analyst (CSA) Online Training
EC-Council 312-39 Online Training
The questions for 312-39 were last updated at Jun 29,2025.
- Exam Code: 312-39
- Exam Name: Certified SOC Analyst (CSA)
- Certification Provider: EC-Council
- Latest update: Jun 29,2025
Properly applied cyber threat intelligence to the SOC team help them in discovering TTPs.
What does these TTPs refer to?
- A . Tactics, Techniques, and Procedures
- B . Tactics, Threats, and Procedures
- C . Targets, Threats, and Process
- D . Tactics, Targets, and Process
David is a SOC analyst in Karen Tech. One day an attack is initiated by the intruders but David was not able to find any suspicious events.
This type of incident is categorized into?
- A . True Positive Incidents
- B . False positive Incidents
- C . True Negative Incidents
- D . False Negative Incidents
An organization is implementing and deploying the SIEM with following capabilities.
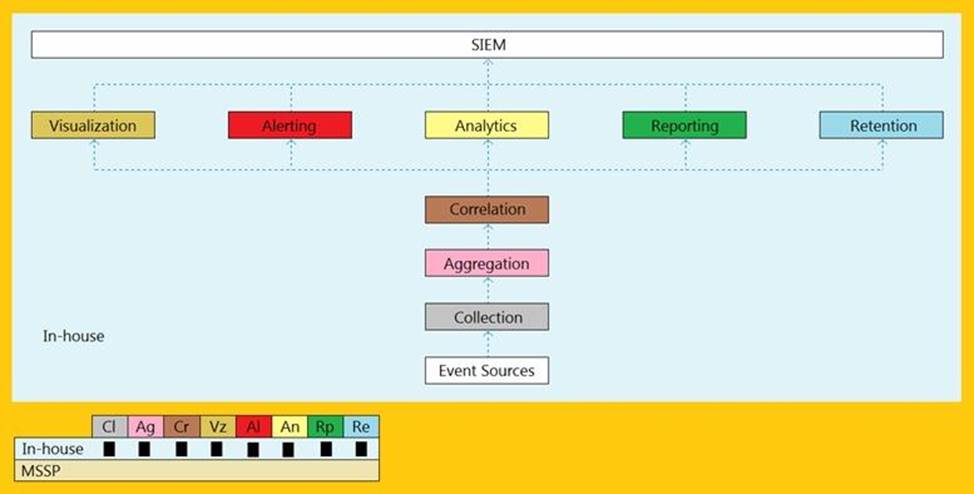
What kind of SIEM deployment architecture the organization is planning to implement?
- A . Cloud, MSSP Managed
- B . Self-hosted, Jointly Managed
- C . Self-hosted, Self-Managed
- D . Self-hosted, MSSP Managed
In which log collection mechanism, the system or application sends log records either on the local disk or over the network.
- A . rule-based
- B . pull-based
- C . push-based
- D . signature-based
Chloe, a SOC analyst with Jake Tech, is checking Linux systems logs. She is investigating files at /var/log/wtmp.
What Chloe is looking at?
- A . Error log
- B . System boot log
- C . General message and system-related stuff
- D . Login records
Where will you find the reputation IP database, if you want to monitor traffic from known bad IP reputation using OSSIM SIEM?
- A . /etc/ossim/reputation
- B . /etc/ossim/siem/server/reputation/data
- C . /etc/siem/ossim/server/reputation.data
- D . /etc/ossim/server/reputation.data
According to the forensics investigation process, what is the next step carried out right after collecting the evidence?
- A . Create a Chain of Custody Document
- B . Send it to the nearby police station
- C . Set a Forensic lab
- D . Call Organizational Disciplinary Team
Which of the following command is used to enable logging in iptables?
- A . $ iptables -B INPUT -j LOG
- B . $ iptables -A OUTPUT -j LOG
- C . $ iptables -A INPUT -j LOG
- D . $ iptables -B OUTPUT -j LOG
Peter, a SOC analyst with Spade Systems, is monitoring and analyzing the router logs of the company and wanted to check the logs that are generated by access control list numbered 210.
What filter should Peter add to the ‘show logging’ command to get the required output?
- A . show logging | access 210
- B . show logging | forward 210
- C . show logging | include 210
- D . show logging | route 210
What does the HTTP status codes 1XX represents?
- A . Informational message
- B . Client error
- C . Success
- D . Redirection
Latest 312-39 Dumps Valid Version with 100 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund


good