DELL EMC DES-9131 Specialist – Infrastructure Security Exam Online Training
DELL EMC DES-9131 Online Training
The questions for DES-9131 were last updated at Dec 17,2025.
- Exam Code: DES-9131
- Exam Name: Specialist - Infrastructure Security Exam
- Certification Provider: DELL EMC
- Latest update: Dec 17,2025
What is the main goal of a gap analysis in the Identify function?
- A . Determine security controls to improve security measures
- B . Determine actions required to get from the current profile state to the target profile state
- C . Identify gaps between Cybersecurity Framework and Cyber Resilient Lifecycle pertaining to that function
- D . Identify business process gaps to improve business efficiency
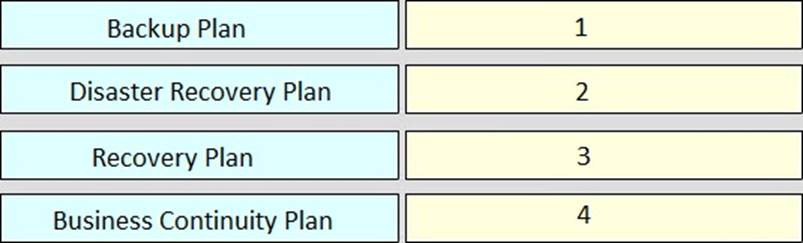
DRAG DROP
Rank order the relative severity of impact to an organization of each plan, where “1” signifies the most impact and “4” signifies the least impact.
What does a security benchmark help define?
- A . Whether or not the organization should implement ISCM
- B . The Baseline, or “as is” state
- C . Which step of the DRP to execute first
- D . What parts of the Baseline are appropriate
In which function is the SDLC implemented?
- A . Respond
- B . Protect
- C . Detect
- D . Recover
Which category addresses the detection of unauthorized code in software?
- A . PR.DS
- B . DE.DP
- C . PR.AT
- D . DE.CM
What database is used to record and manage assets?
- A . Configuration Management Database
- B . Asset Inventory Management Database
- C . High Availability Mirrored Database
- D . Patch Management Inventory Database
The CSIRT team is following the existing recovery plans on non-production systems in a PRE-BREACH scenario.
This action is being executed in which function?
- A . Protect
- B . Recover
- C . Identify
- D . Respond
What is a consideration when performing data collection in Information Security Continuous Monitoring?
- A . Data collection efficiency is increased through automation.
- B . The more data collected, the better chances to catch an anomaly.
- C . Collection is used only for compliance requirements.
- D . Data is best captured as it traverses the network.
An organization has a policy to respond “ASAP” to security incidents. The security team is having a difficult time prioritizing events because they are responding to all of them, in order of receipt.
Which part of the IRP does the team need to implement or update?
- A . Scheduling of incident responses
- B . ‘Post mortem’ documentation
- C . Classification of incidents
- D . Containment of incidents
Your firewall blocked several machines on your network from connecting to a malicious IP address. After reviewing the logs, the CSIRT discovers all Microsoft Windows machines on the network have been affected based on a newly published CVE.
Based on the IRP, what should be done immediately?
- A . Update the asset inventory
- B . Contain the breach
- C . Eradicate the breach
- D . Revise the IRP
Latest DES-9131 Dumps Valid Version with 60 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund