DELL EMC DEA-3TT2 Associate – Data Protection and Management Version 2 Exam Online Training
DELL EMC DEA-3TT2 Online Training
The questions for DEA-3TT2 were last updated at Mar 02,2026.
- Exam Code: DEA-3TT2
- Exam Name: Associate - Data Protection and Management Version 2 Exam
- Certification Provider: DELL EMC
- Latest update: Mar 02,2026
A backup administrator has defined a backup policy where full backups are scheduled at 8 PM every Saturday and differential backups for the rest of the week at same time. A data loss happened on Friday at 11 AM.
How many backup copies are required to restore the requested files?
- A . 2
- B . 3
- C . 6
- D . 7
A storage system is configured with erasure coding, divided up into 12 data segments and 4 coding segments. Each segment is written to different drives.
What is the maximum number of drive failures that can be withstood without losing the data in this configuration?
- A . 6
- B . 4
- C . 3
- D . 5
A computer has an MTBF of 7000 hours and an MTTR of 18 hours? What is the availability of the data?
- A . 90.7%
- B . 99.1%
- C . 99.7%
- D . 99.8%
What are the considerations when designing a disaster recovery plan based on RTO and RPO?
- A . Lower RTO and RPO have no effect on cost
- B . Lower RTO and RPO simplify the solution
- C . Lower RTO and RPO decrease the cost
- D . Lower RTO and RPO increase the cost
At which layer is the risk of backup data recovered to an unauthorized destination considered a security threat?
- A . Protection Application
- B . Management Domain
- C . Data Source
- D . Database Application
What is true of hot-swappable hardware?
- A . All components need to be rearranged after swap
- B . Reboot is required after a change
- C . All fans need to be running to ensure proper cooling
- D . Replaceable with zero downtime
Refer to the exhibit.
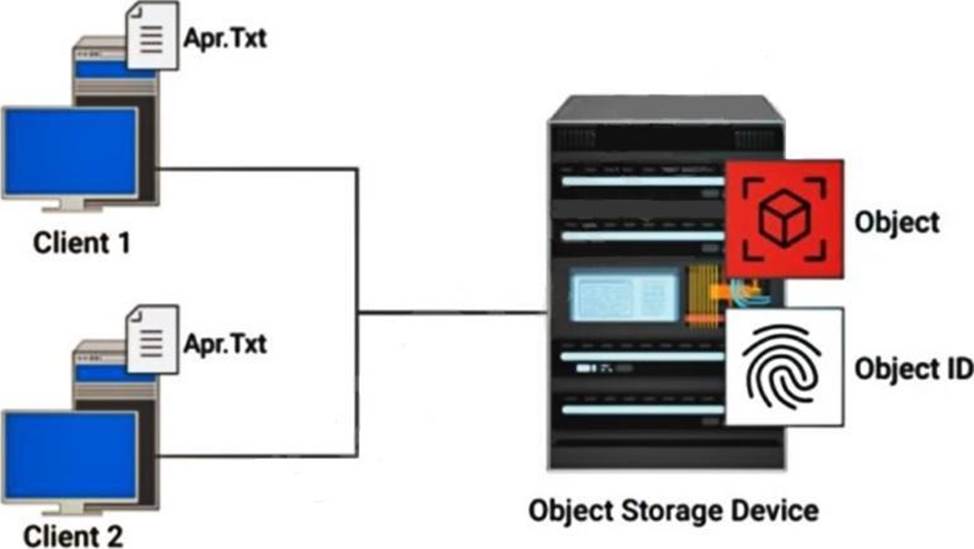
How is a hash created on file Apr.Txt in an object-level deduplication?
- A . from content with variable-length
- B . from the metadata of the file
- C . from the content of the file
- D . from content with fixed-length
Which security control detects and blocks unusual network behavior?
- A . IDPA
- B . VPN
- C . IDPS
- D . Zoning
Which security control provides logical isolation of devices on Ethernet?
- A . VPN
- B . Firewall
- C . VSAN
- D . VLAN
What is a characteristic of data archiving?
- A . Secondary copy of data
- B . Primary copy of data
- C . Short-term retention
- D . Used for operational recovery
Latest DEA-3TT2 Dumps Valid Version with 60 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

