DELL EMC DEA-1TT5 Associate – Information Storage and Management Exam Online Training
DELL EMC DEA-1TT5 Online Training
The questions for DEA-1TT5 were last updated at Apr 24,2025.
- Exam Code: DEA-1TT5
- Exam Name: Associate - Information Storage and Management Exam
- Certification Provider: DELL EMC
- Latest update: Apr 24,2025
What is a feature of 5G technology?
- A . Higher LAN bandwidth
- B . Higher connectivity density
- C . Higher WAN bandwidth
- D . Higher transmission distances
In a RAID 6 array with four disks, what is the total usable data storage capacity on the array if the disk size is 200 GB?
- A . 200 GB
- B . 400 GB
- C . 600 GB
- D . 800 GB
Why is it important for organizations to implement a multi-site remote replication solution?
- A . Ensure data protection is always available if there are any single site failures
- B . Provide consistent near-zero RPO in the event of source and remote site failures
- C . Perform synchronous replication with low network bandwidth
- D . Recover data to any point-in-time in the event of a remote site failure
What accurately describes an object-based storage device (OSD)?
- A . One object can be placed inside another object
- B . Objects are created based on the name and location of the file
- C . Objects exist at the same level in the address space
- D . Numerous objects can be stored in a single namespace
Which Dell EMC product is a software-defined storage platform that abstracts, pools, and automates a data center’s physical storage infrastructure?
- A . XtremIO
- B . ViPR Controller
- C . VxFlex OS
- D . PowerMax
What is the functionality of the application server in a Mobile Device Management?
- A . Perform administration and management of all unmanaged devices
- B . Authenticate the device that requests access
- C . Perform administration and management of all managed devices
- D . Authorize devices directed to the server
A user lost access to a key VM due to a hardware failure. A proxy server regularly takes PIT snapshots of the VM to protect the data.
What type of data protection method is this called’?
- A . Agent-based
- B . Backup as a service
- C . Local replication
- D . Image-based
What is a function of the application hardening process’?
- A . Perform penetration testing and validate OS patch management
- B . Disable unnecessary application features or services
- C . Isolate VM network to ensure the default VM configurations are unchanged
- D . Validate unused application files and programs to ensure consistency
Refer to the Exhibit:
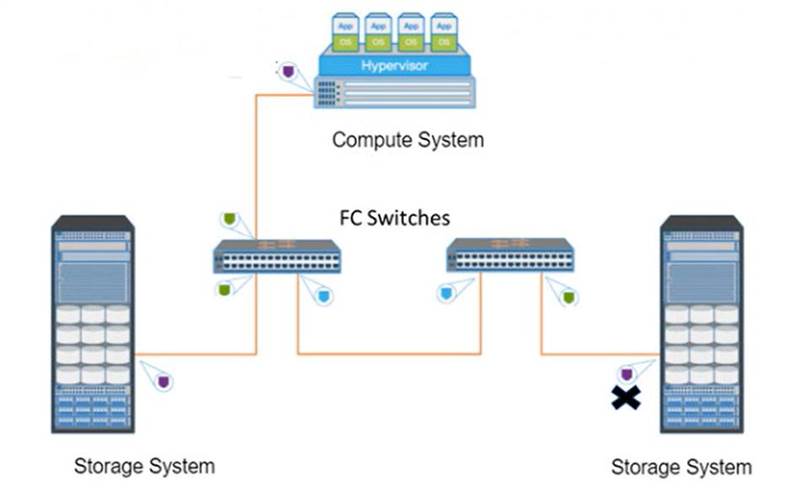
What type of FC port does the "X" represent?
- A . F_port
- B . NI_port
- C . N_port
- D . E_port
What is the result of increasing the number of FC switches in a full mesh topology?
- A . Reduces available node ports for ISL connectivity
- B . Reduces number of storage and compute ports for node connectivity
- C . Reduces switch ports available for node connectivity
- D . Reduces switch ports available bandwidth for node connectivity
Latest DEA-1TT5 Dumps Valid Version with 122 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

