DELL EMC D-ISM-FN-23 Dell Information Storage and Management Foundations 2023 Online Training
DELL EMC D-ISM-FN-23 Online Training
The questions for D-ISM-FN-23 were last updated at Dec 18,2025.
- Exam Code: D-ISM-FN-23
- Exam Name: Dell Information Storage and Management Foundations 2023
- Certification Provider: DELL EMC
- Latest update: Dec 18,2025
Which three parameters define information availability in a modern data center environment?
- A . Reliability – Accessibility – Timeliness
- B . Capacity – Availability – Security
- C . Confidentiality – Integrity – Availability
- D . Reliability – Integrity – Performance
Which type of Fibre Channel (FC) ports do “X” and “Y” represent in the graphic?
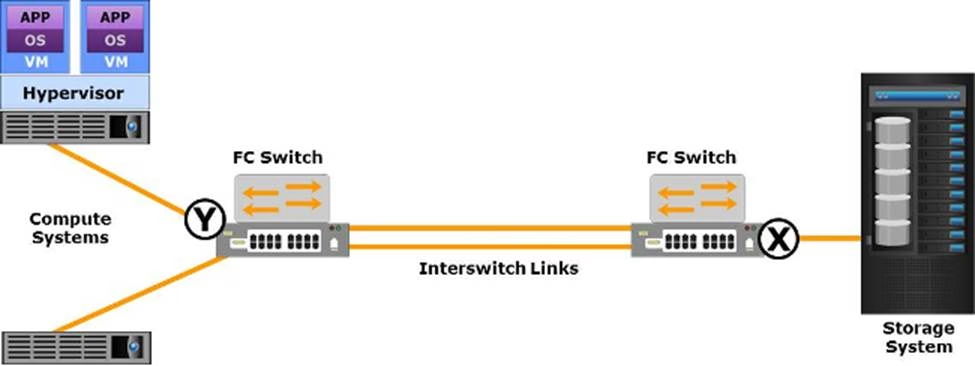
- A . X is an E_Port and Y is an N_Port
- B . X is an F_Port and Y is an F_Port
- C . X is an N_Port and Y is an E_Port
- D . X is an N_Port and Y is an N_Port
Which operation is performed by a scale-out NAS cluster when clients send data to the cluster?
- A . Data is divided and stored on multiple nodes in parallel
- B . Data is consolidated into a block and then stored on the NAS head
- C . Data is evenly distributed to every file system in the cluster
- D . NAS file system and cluster grow dynamically to store the data
What is an advantage of deploying a purpose-built, disk-based backup appliance in a data center environment?
- A . Eliminate the need for performing source-based deduplication.
- B . Convert the capital expenditure to an operational expenditure.
- C . Lower the recovery time objective of an organization.
- D . Retain the fixed content for longer periods in the data center.
An institution has made the decision to exit a client relationship due to anti-money laundering concerns. Prior to starting the close out process, the institution receives a written request from a law enforcement agency to keep the account open. The client is the subject of an ongoing investigation and law enforcement wants the institution to continue to monitor the account and report any suspicious activity.
What is primary consideration the institution should keep in mind when deciding whether to agree to this request?
- A . The anticipated cost of complying with the law enforcement request
- B . The number of suspicious transaction reports previously filed on the client
- C . The fact that the institution has a solid record in complying with law enforcement requests
- D . Whether the institution can continue to meet its regulatory obligations with the accounts open
Which functionality is provided by a process login in a Fibre Channel (FC) SAN environment?
- A . Exchanges service relevant parameters between an N_port and an N_port
- B . Establishes a connection to the fabric between an N_port and an F_port
- C . Exchange ULP-related parameters between two N_ports
- D . Establishes a session that occurs between two E_ports
Which logical components are required in compute systems?
- A . Operating system
Deduplicating file system
RAID LUN manager
Device drivers - B . Operating system
File system
RAID LUN manager
Device drivers - C . Operating system
File system
Logical volume manager
Device drivers - D . Operating system
Deduplicating File system
Logical volume manager
Device drivers
A company’s Finance department needs 200 GB of storage for their business applications. A LUN is created with 200 GB and RAID 1 is configured to support the applications.
If the cost of storage per GB is $2, what is the chargeback cost to the department for application storage?
- A . $ 200
- B . $ 400
- C . $ 800
- D . $ 1500
What happens when a write request to a valid page is received in a solid-state drive?
- A . Requested page is electrically erased and the write continues with the erased page
- B . Requested page is overwritten by the new page
- C . Requested page is marked invalid and the write continues with an available empty page
- D . Write request is queued until the requested page is erased
An organization wants to use an application for their business communication. However, they do not have the skills or the time to deploy and manage an application in-house.
Which recommended cloud service model will meet their requirement?
- A . Infrastructure as a Service
- B . Database as a Service
- C . Software as a Service
- D . Platform as a Service
Latest D-ISM-FN-23 Dumps Valid Version with 580 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

