DELL EMC D-ISM-FN-23 Dell Information Storage and Management Foundations 2023 Online Training
DELL EMC D-ISM-FN-23 Online Training
The questions for D-ISM-FN-23 were last updated at Apr 26,2025.
- Exam Code: D-ISM-FN-23
- Exam Name: Dell Information Storage and Management Foundations 2023
- Certification Provider: DELL EMC
- Latest update: Apr 26,2025
A company is using an intrusion detection and prevention system (IDPS) to scan and analyze intrusion events.
Which IDPS technique uses a database that contains known attack patterns?
- A . Role-based
- B . Profile-based
- C . Signature-based
- D . Anomaly-based
Which data protection solution provides the ability to select a backup technology based on demand?
- A . Agent-Based backup
- B . Cloud-Based backup
- C . File-Based backup
- D . Image-Based backup
Which layer of the OSI model provides the functional and procedural methods to transfer data between network entities?
- A . Data link
- B . Presentation
- C . Session
- D . Application
Which cloud service model provides the highest level of control over operating systems, applications, and storage?
- A . Platform as a Service (PaaS)
- B . Software as a Service (SaaS)
- C . Infrastructure as a Service (IaaS)
- D . Function as a Service (FaaS)
What is a characteristic of an FC-AL implementation?
- A . Devices can be added and removed dynamically without any impact
- B . Supports connectivity up to 15 million nodes
- C . Requires at least one connectivity device
- D . Reserves one address for connecting an FC-SW port
In a NAS environment, which file system provides a public or open variation of the Server Message Block (SMB) protocol and uses the TCP/IP protocol?
- A . Hadoop Distributed File System (HDFS)
- B . New Technology File System (NTFS)
- C . Common Internet File System (CIFS)
- D . Network File System (NFS)
What is the purpose of monitoring capacity in a storage infrastructure?
- A . Tracking the amount of storage infrastructure resources used and available
- B . Evaluating utilization of components and identifying bottlenecks
- C . Tracking configuration changes to the storage infrastructure elements
- D . Identifying component failures that may lead to service unavailability
What is used to implement a fully functional SAN?
- A . IPFC
- B . iSCSI
- C . VXLAN
- D . FCIP
Which product provides an organization with the power to search and analyze vast amounts of data in one place and helps administrators to discover suspicious event trends?
- A . Dell InTrust
- B . Dell Change Auditor
- C . VMware AppDefense
- D . VMware AirWatch
Based on the exhibit, which type of storage does the “X” represent?
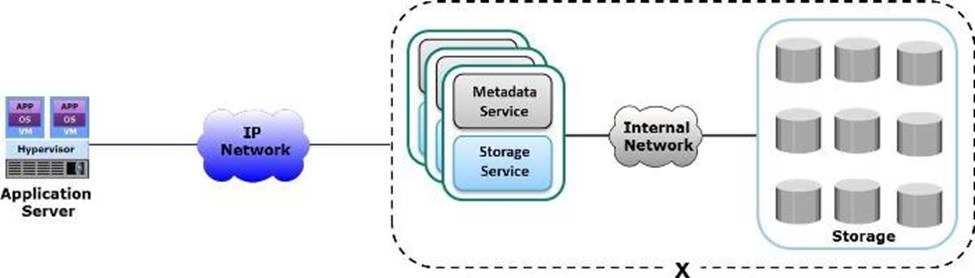
- A . File-based
- B . Block-based
- C . Object-based
- D . Unified-based
Latest D-ISM-FN-23 Dumps Valid Version with 580 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

