DELL EMC D-CSF-SC-23 NIST Cybersecurity Framework 2023 Exam Online Training
DELL EMC D-CSF-SC-23 Online Training
The questions for D-CSF-SC-23 were last updated at Dec 18,2025.
- Exam Code: D-CSF-SC-23
- Exam Name: NIST Cybersecurity Framework 2023 Exam
- Certification Provider: DELL EMC
- Latest update: Dec 18,2025
What is the purpose of a baseline assessment?
- A . Enhance data integrity
- B . Determine costs
- C . Reduce deployment time
- D . Determine risk
What is the main goal of a gap analysis in the Identify function?
- A . Determine security controls to improve security measures
- B . Determine actions required to get from the current profile state to the target profile state
- C . Identify gaps between Cybersecurity Framework and Cyber Resilient Lifecycle pertaining to that function
- D . Identify business process gaps to improve business efficiency
What is concerned with availability, reliability, and recoverability of business processes and functions?
- A . Business Impact Analysis
- B . Business Continuity Plan
- C . Recovery Strategy
- D . Disaster Recovery Plan
Concerning a risk management strategy, what should the executive level be responsible for communicating?
- A . Risk mitigation
- B . Risk profile
- C . Risk tolerance
- D . Asset risk
Refer to the exhibit.
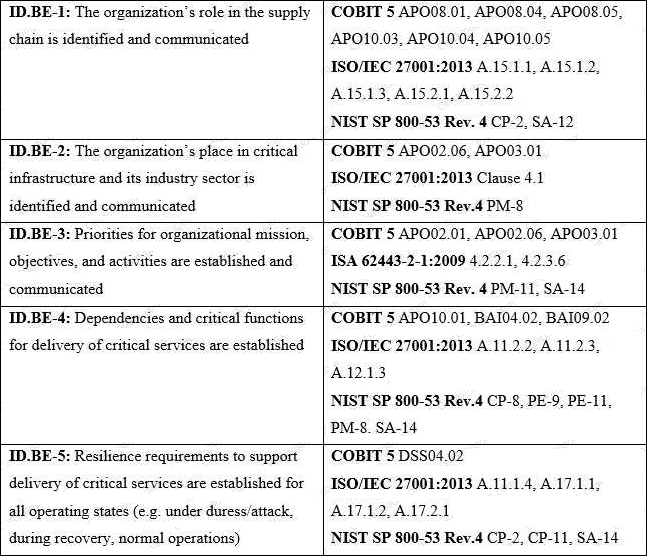
What type of item appears in the second column of the table?
- A . Subcategory
- B . Informative Reference
- C . Function
- D . Tier
At what cyber kill chain stage do attackers use malware to exploit specific software or hardware vulnerabilities on the target, based on the information retrieved at the reconnaissance stage?
- A . Installation
- B . Reconnaissance
- C . Weaponization
- D . Delivery
During what activity does an organization identify and prioritize technical, organizational, procedural, administrative, and physical security weaknesses?
- A . Table top exercise
- B . Penetration testing
- C . Vulnerability assessment
- D . White box testing
Your organization was breached. You informed the CSIRT and they contained the breach and eradicated the threat.
What is the next step required to ensure that you have an effective CSRL and a more robust cybersecurity posture in the future?
- A . Determine change agent
- B . Update the BIA
- C . Conduct a gap analysis
- D . Update the BCP
The information security manager for a major web based retailer has determined that the product catalog database is corrupt. The business can still accept orders online but the products cannot be updated. Expected downtime to rebuild is roughly four hours.
What type of asset should the product catalog database be categorized as?
- A . Mission critical
- B . Safety critical
- C . Non-critical
- D . Business critical
What should an organization use to effectively mitigate against password sharing to prevent unauthorized access to systems?
- A . Access through a ticketing system
- B . Frequent password resets
- C . Strong password requirements
- D . Two factor authentication
Latest D-CSF-SC-23 Dumps Valid Version with 110 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

