DELL EMC D-CSF-SC-23 NIST Cybersecurity Framework 2023 Exam Online Training
DELL EMC D-CSF-SC-23 Online Training
The questions for D-CSF-SC-23 were last updated at Apr 06,2025.
- Exam Code: D-CSF-SC-23
- Exam Name: NIST Cybersecurity Framework 2023 Exam
- Certification Provider: DELL EMC
- Latest update: Apr 06,2025
What could be considered a set of cybersecurity activities, desired outcomes, and applicable references that are common across critical infrastructure sectors and align to five concurrent and continuous functions?
- A . Baseline
- B . Core
- C . Profile
- D . Governance
Refer to the exhibit.
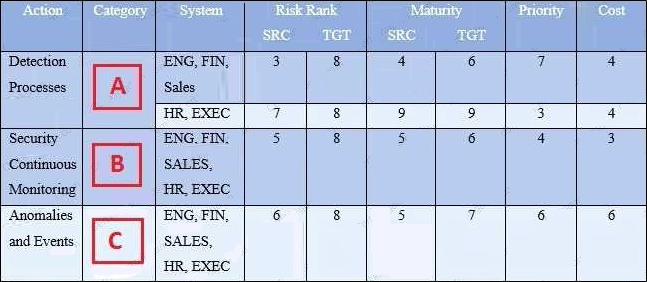
Your organization’s security team has been working with various business units to understand their business requirements, risk tolerance, and resources used to create a Framework Profile. Based on the Profile provided, what entries correspond to labels A, B, and C?

- A . Option A
- B . Option B
- C . Option C
What term refers to a partially equipped, environmentally conditioned work space used to relocate operations in the event of a significant disruption?
- A . Hot site
- B . Warm site
- C . Mirror site
- D . Secondary site
What common process conducted by organizations when protecting digital assets is outside the scope of the NIST Cybersecurity Framework?
- A . Recover
- B . Identify
- C . Protect
- D . Investigate
What are the main components of the NIST Cybersecurity Framework?
- A . Core, Categories, and Tiers
- B . Functions, Profiles, and Tiers
- C . Categories, Tiers, and Profiles
- D . Core, Tiers, and Profiles
The Disaster Recovery Plan must document what effort in order to address unrecoverable assets?
- A . RTO savings
- B . Recovery priority
- C . Recovery resources
- D . Recovery resources
To generate an accurate risk assessment, organizations need to gather information in what areas?
- A . Assets, Threats, Vulnerabilities, and Impact
- B . Assets, Vulnerabilities, Security, and Response
- C . Inventory, Security, Response, and Impact
- D . Inventory, Threats, Security, and Impact
You need to review your current security baseline policy for your company and determine which security controls need to be applied to the baseline and what changes have occurred since the last update.
Which category addresses this need?
- A . ID.AM
- B . PR.IP
- C . PR.MA
- D . ID.SC
What specifically addresses cyber-attacks against an organization’s IT systems?
- A . Continuity of Support Plan
- B . Business Continuity Plan
- C . Continuity of Operations Plan
- D . Incident Response Plan
The CSF recommends that the Communication Plan for an IRP include audience, method of communication, frequency, and what other element?
- A . Incident category
- B . Message criteria
- C . Incident severity
- D . Templates to use
Latest D-CSF-SC-23 Dumps Valid Version with 110 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

