DELL EMC D-CSF-SC-01 Dell NIST Cybersecurity Framework 2.0 Online Training
DELL EMC D-CSF-SC-01 Online Training
The questions for D-CSF-SC-01 were last updated at Feb 21,2025.
- Exam Code: D-CSF-SC-01
- Exam Name: Dell NIST Cybersecurity Framework 2.0
- Certification Provider: DELL EMC
- Latest update: Feb 21,2025
The primary goal of the COBIT 2019 governance system is to ensure that ___ aligns with the overall business strategy.
- A . Cybersecurity risks
- B . IT operations
- C . Network uptime
- D . External compliance standards
The ___________ component of the Detect Function is responsible for identifying unusual patterns or activities that may indicate a threat.
- A . Incident Response
- B . Anomalies and Events
- C . Threat Assessment
- D . Disaster Recovery
Tiers in the NIST Cybersecurity Framework help organizations assess their level of ___.
- A . Technical maturity
- B . Cybersecurity governance
- C . Risk management
- D . Vendor compliance
An organization is creating a customized version of the NIST Cybersecurity Framework to align with its unique risk profile and business requirements. They are currently mapping their organizational priorities and risk tolerance to the framework functions.
Which part of the NIST Framework are they focusing on?
- A . Core
- B . Tiers
- C . Profiles
- D . Objectives
Match each Detect Function component with its primary purpose.
Component
Continuous Monitoring
Anomalies and Events
Detection Processes
Threat Intelligence
Purpose
A) Real-time observation for suspicious activities
B) Identifying unusual patterns
C) Formalizing detection protocols
D) Analyzing data to identify threats
- A . Continuous Monitoring – A
Anomalies and Events – B
Detection Processes – C
Threat Intelligence – D - B . Continuous Monitoring – A
Anomalies and Events – B
Detection Processes – D
Threat Intelligence – C - C . Continuous Monitoring – A
Anomalies and Events – C
Detection Processes – B
Threat Intelligence – D - D . Continuous Monitoring – D
Anomalies and Events – B
Detection Processes – C
Threat Intelligence – A
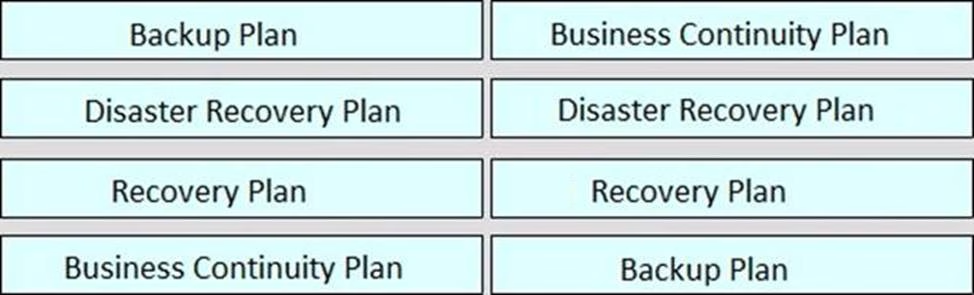
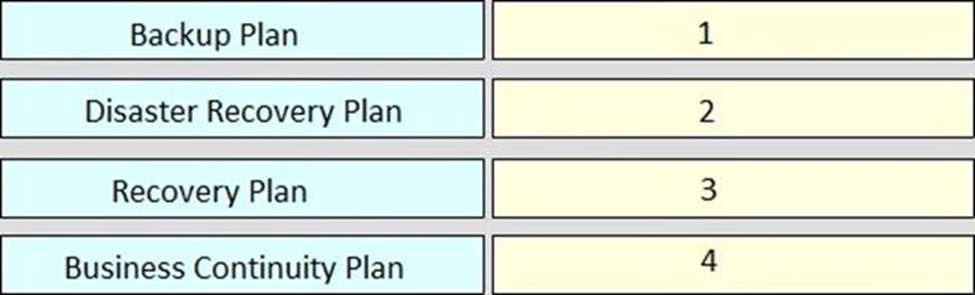
Rank order the relative severity of impact to an organization of each plan, where “1” signifies the most impact and “4” signifies the least impact.
Which protective technologies are typically associated with the Protect Function? (Select two)
- A . Data encryption
- B . Business impact analysis
- C . Access management
- D . Threat intelligence analysis
What is the primary purpose of the COBIT 2019 governance framework in the context of cybersecurity?
- A . To improve firewall configurations
- B . To ensure alignment between business goals and cybersecurity strategy
- C . To enforce external compliance regulations
- D . To manage software development processes
COBIT 2019’s focus on cybersecurity risk aligns with which NIST Cybersecurity Framework component?
- A . Respond
- B . Profiles
- C . Governance
- D . Tiers
The ___ function of the NIST Cybersecurity Framework ensures timely identification of cybersecurity events.
- A . Respond
- B . Identify
- C . Detect
- D . Recover
Latest D-CSF-SC-01 Dumps Valid Version with 175 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund