CompTIA PT0-002 CompTIA PenTest+ Certification Exam Online Training
CompTIA PT0-002 Online Training
The questions for PT0-002 were last updated at Dec 06,2025.
- Exam Code: PT0-002
- Exam Name: CompTIA PenTest+ Certification Exam
- Certification Provider: CompTIA
- Latest update: Dec 06,2025
A penetration tester has been contracted to review wireless security. The tester has deployed a malicious wireless AP that mimics the configuration of the target enterprise WiFi. The penetration tester now wants to try to force nearby wireless stations to connect to the malicious AP.
Which of the following steps should the tester take NEXT?
- A . Send deauthentication frames to the stations.
- B . Perform jamming on all 2.4GHz and 5GHz channels.
- C . Set the malicious AP to broadcast within dynamic frequency selection channels.
- D . Modify the malicious AP configuration to not use a pre-shared key.
Given the following code:
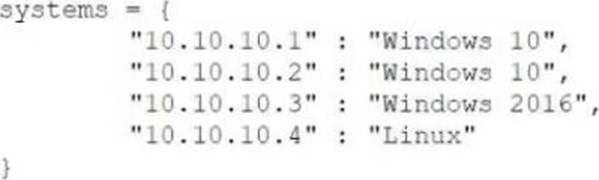
Which of the following data structures is systems?
- A . A tuple
- B . A tree
- C . An array
- D . A dictionary
A customer adds a requirement to the scope of a penetration test that states activities can only occur during normal business hours.
Which of the following BEST describes why this would be necessary?
- A . To meet PCI DSS testing requirements
- B . For testing of the customer’s SLA with the ISP
- C . Because of concerns regarding bandwidth limitations
- D . To ensure someone is available if something goes wrong
Which of the following would a company’s hunt team be MOST interested in seeing in a final report?
- A . Executive summary
- B . Attack TTPs
- C . Methodology
- D . Scope details
A penetration tester completed a vulnerability scan against a web server and identified a single but severe vulnerability.
Which of the following is the BEST way to ensure this is a true positive?
- A . Run another scanner to compare.
- B . Perform a manual test on the server.
- C . Check the results on the scanner.
- D . Look for the vulnerability online.
A company has hired a penetration tester to deploy and set up a rogue access point on the network.
Which of the following is the BEST tool to use to accomplish this goal?
- A . Wireshark
- B . Aircrack-ng
- C . Kismet
- D . Wifite
A penetration tester is reviewing the following SOW prior to engaging with a client:
“Network diagrams, logical and physical asset inventory, and employees’ names are to be treated as client confidential. Upon completion of the engagement, the penetration tester will submit findings to the client’s Chief Information Security Officer (CISO) via encrypted protocols and subsequently dispose of all findings by erasing them in a secure manner.”
Based on the information in the SOW, which of the following behaviors would be considered unethical? (Choose two.)
- A . Utilizing proprietary penetration-testing tools that are not available to the public or to the client for auditing and inspection
- B . Utilizing public-key cryptography to ensure findings are delivered to the CISO upon
completion of the
engagement - C . Failing to share with the client critical vulnerabilities that exist within the client architecture to appease the client’s senior leadership team
- D . Seeking help with the engagement in underground hacker forums by sharing the client’s public IP address
- E . Using a software-based erase tool to wipe the client’s findings from the penetration tester’s laptop
- F . Retaining the SOW within the penetration tester’s company for future use so the sales team can plan future engagements
A penetration tester analyzed a web-application log file and discovered an input that was sent to the company’s web application. The input contains a string that says "WAITFOR."
Which of the following attacks is being attempted?
- A . SQL injection
- B . HTML injection
- C . Remote command injection
- D . DLL injection
A penetration tester ran a ping CA command during an unknown environment test, and it returned a 128 TTL packet.
Which of the following OSs would MOST likely return a packet of this type?
- A . Windows
- B . Apple
- C . Linux
- D . Android
A penetration tester needs to upload the results of a port scan to a centralized security tool.
Which of the following commands would allow the tester to save the results in an interchangeable format?
- A . nmap -iL results 192.168.0.10-100
- B . nmap 192.168.0.10-100 -O > results
- C . nmap -A 192.168.0.10-100 -oX results
- D . nmap 192.168.0.10-100 | grep "results"
Latest PT0-002 Dumps Valid Version with 110 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

