CompTIA PT0-001 CompTIA PenTest+ Certification Exam Online Training
CompTIA PT0-001 Online Training
The questions for PT0-001 were last updated at Dec 23,2025.
- Exam Code: PT0-001
- Exam Name: CompTIA PenTest+ Certification Exam
- Certification Provider: CompTIA
- Latest update: Dec 23,2025
A penetration tester runs the following on a machine:
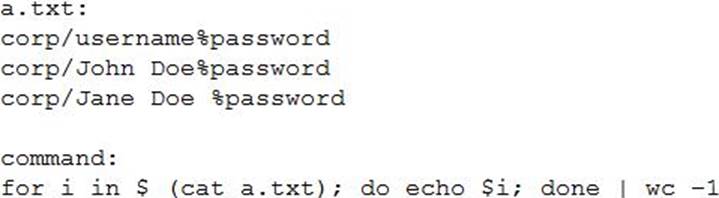
Which of the following will be returned?
- A . 1
- B . 3
- C . 5
- D . 6
Which of the following commands will allow a tester to enumerate potential unquoted services paths on a host?
- A . wmic environment get name, variablevalue, username / findstr /i “Path” | findstr /i “service”
- B . wmic service get /format:hform > c:tempservices.html
- C . wmic startup get caption, location, command | findstr /i “service” | findstr /v /i “%”
- D . wmic service get name, displayname, patchname, startmode | findstr /i “auto” | findstr /i /v “c:windows\” | findstr /i /v “””
D
Explanation:
Reference: https://medium.com/@SumitVerma101/windows-privilege-escalation-part-1-unquoted-servicepath-c7a011a8d8ae
When performing compliance-based assessments, which of the following is the MOST important Key consideration?
- A . Additional rate
- B . Company policy
- C . Impact tolerance
- D . Industry type
A penetration tester notices that the X-Frame-Optjons header on a web application is not set .
Which of the following would a malicious actor do to exploit this configuration setting?
- A . Use path modification to escape the application’s framework.
- B . Create a frame that overlays the application.
- C . Inject a malicious iframe containing JavaScript.
- D . Pass an iframe attribute that is malicious.
A penetration tester successfully exploits a Windows host and dumps the hashes.
Which of the following hashes can the penetration tester use to perform a pass-the-hash attack?
A)
![]()
B)
![]()
C)
![]()
D)
![]()
- A . Option A
- B . Option B
- C . Option C
- D . Option D
A penetration tester is performing a black-box test of a client web application, and the scan host is unable to access it. The client has sent screenshots showing the system is functioning correctly .
Which of the following is MOST likely the issue?
- A . The penetration tester was not provided with a WSDL file.
- B . The penetration tester needs an OAuth bearer token.
- C . The tester has provided an incorrect password for the application.
- D . An IPS/WAF whitelist is in place to protect the environment.
An engineer, who is conducting a penetration test for a web application, discovers the user login process sends from field data using the HTTP GET method.
To mitigate the risk of exposing sensitive information, the form should be sent using an:
- A . HTTP POST method.
- B . HTTP OPTIONS method.
- C . HTTP PUT method.
- D . HTTP TRACE method.
A client needs to be PCI compliant and has external-facing web servers .
Which of the following CVSS vulnerability scores would automatically bring the client out of compliance standards such as PCI 3.x?
- A . 2.9
- B . 3.0
- C . 4.0
- D . 5.9
C
Explanation:
Reference: https://qualysguard.qg2.apps.qualys.com/qwebhelp/fo_portal/knowledgebase/pci_exceptions.htm
A consultant is performing a social engineering attack against a client. The consultant was able to collect a number of usernames and passwords using a phishing campaign. The consultant is given credentials to log on to various employees email accounts.
Given the findings, which of the following should the consultant recommend be implemented?
- A . Strong password policy
- B . Password encryption
- C . Email system hardening
- D . Two-factor authentication
A penetration tester has access to a local machine running Linux, but the account has limited privileges .
Which of the following types of files could the tester BEST use for privilege escalation?
- A . Binaries stored in /usr/bin
- B . Files with permission 4xxx
- C . Files stored in /root directory
- D . Files with the wrong ACL rules configured
Latest PT0-001 Dumps Valid Version with 248 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

