CompTIA PT0-001 CompTIA PenTest+ Certification Exam Online Training
CompTIA PT0-001 Online Training
The questions for PT0-001 were last updated at Dec 12,2025.
- Exam Code: PT0-001
- Exam Name: CompTIA PenTest+ Certification Exam
- Certification Provider: CompTIA
- Latest update: Dec 12,2025
A penetration tester is required to exploit a WPS implementation weakness .
Which of the following tools will perform the attack?
- A . Karma
- B . Kismet
- C . Pixie
- D . NetStumbler
D
Explanation:
Reference: https://en.wikipedia.org/wiki/NetStumbler
A penetration tester has obtained access to an IP network subnet that contains ICS equipment intercommunication .
Which of the following attacks is MOST likely to succeed in creating a physical effect?
- A . DNS cache poisoning
- B . Record and replay
- C . Supervisory server SMB
- D . Blind SQL injection
CORRECT TEXT
You are a penetration tester running port scans on a server.
INSTRUCTIONS
Part1: Given the output, construct the command that was used to generate this output from the available options.
Part2: Once the command is appropriately constructed, use the given output to identify the potential attack vectors that should be investigated further.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
Part1
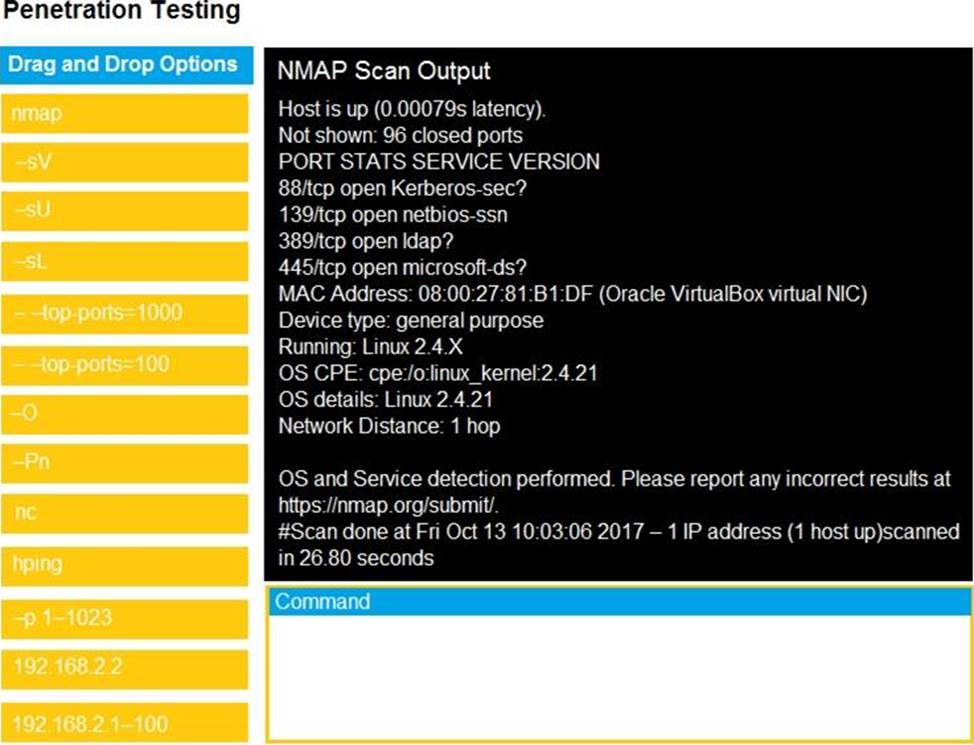
Part2
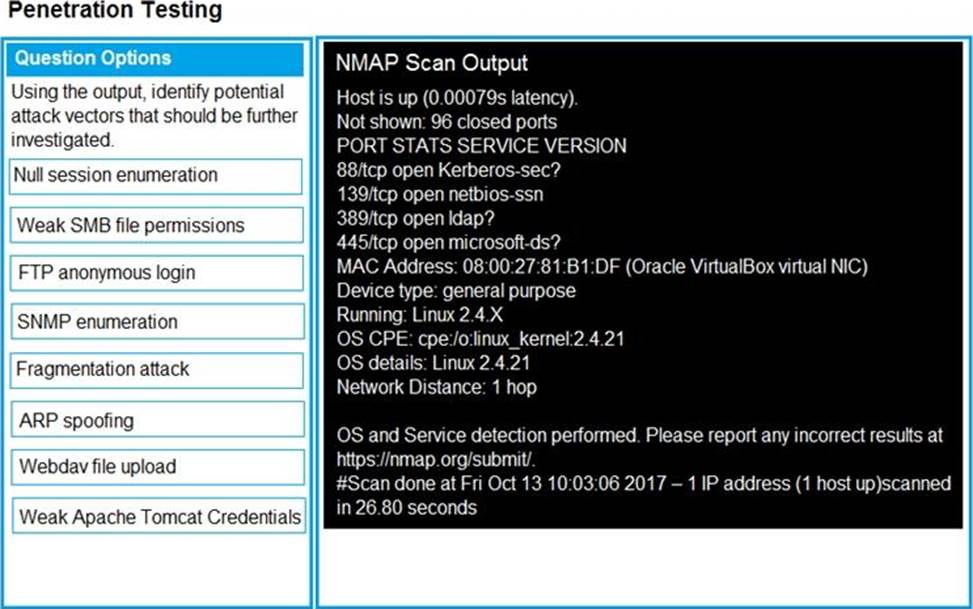
Part 2 C Weak SMB file permissions
A penetration tester is required to perform OSINT on staff at a target company after completing the infrastructure aspect .
Which of the following would be the BEST step for the penetration tester to take?
- A . Obtain staff information by calling the company and using social engineering techniques.
- B . Visit the client and use impersonation to obtain information from staff.
- C . Send spoofed emails to staff to see if staff will respond with sensitive information.
- D . Search the Internet for information on staff such as social networking sites.
A penetration tester is testing a web application and is logged in as a lower-privileged user. The tester runs arbitrary JavaScript within an application, which sends an XMLHttpRequest, resulting in exploiting features to which only an administrator should have access .
Which of the following controls would BEST mitigate the vulnerability?
- A . Implement authorization checks.
- B . Sanitize all the user input.
- C . Prevent directory traversal.
- D . Add client-side security controls
CORRECT TEXT
You are a penetration tester reviewing a client’s website through a web browser.
INSTRUCTIONS
Review all components of the website through the browser to determine if vulnerabilities are present.
Remediate ONLY the highest vulnerability from either the certificate, source, or cookies.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
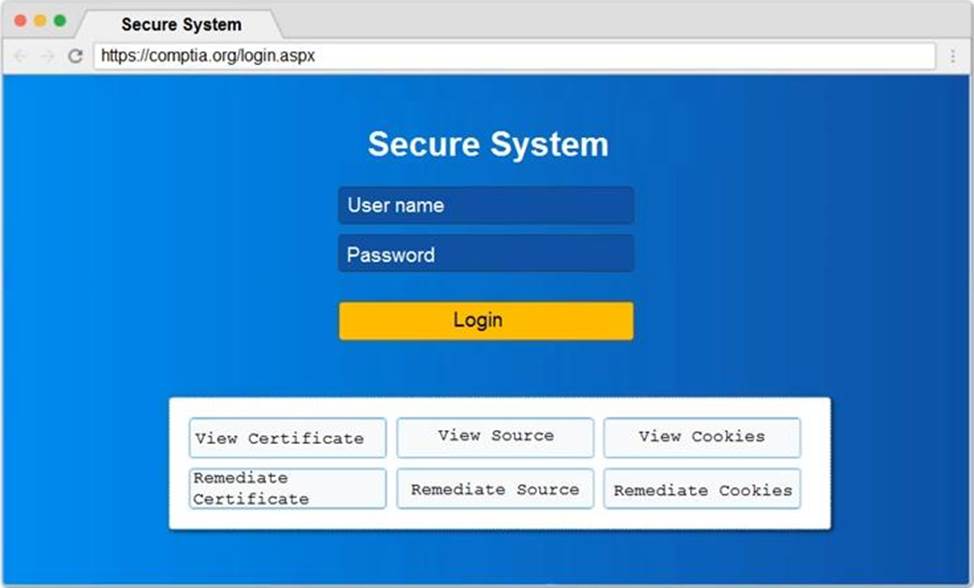
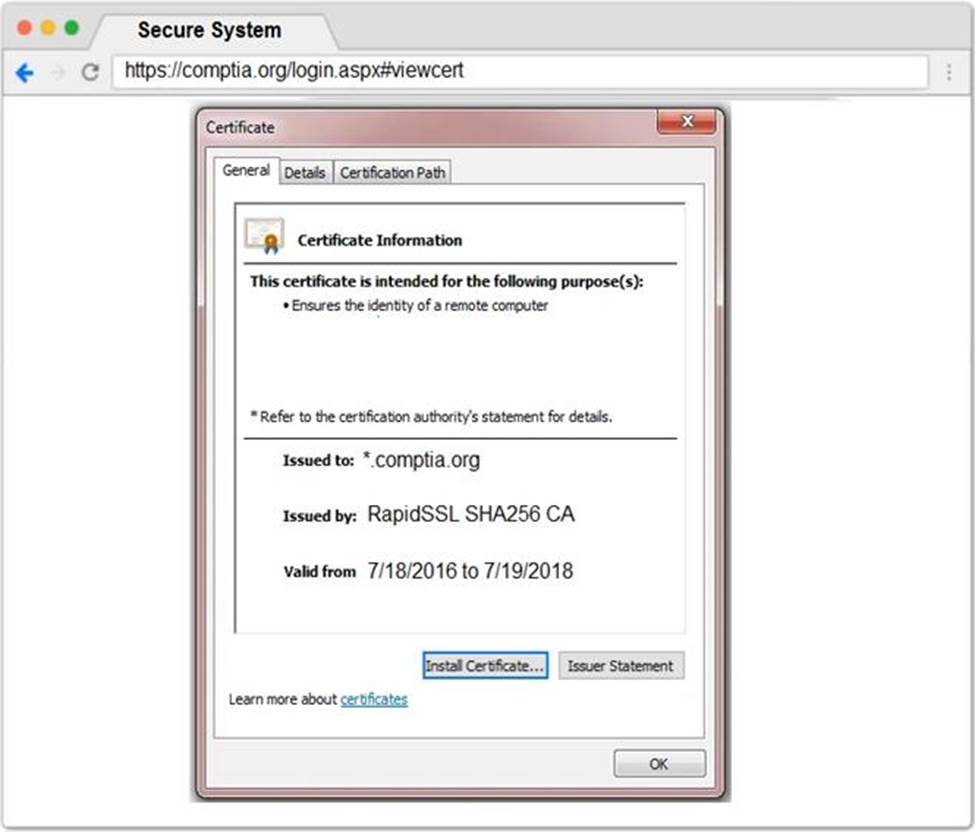
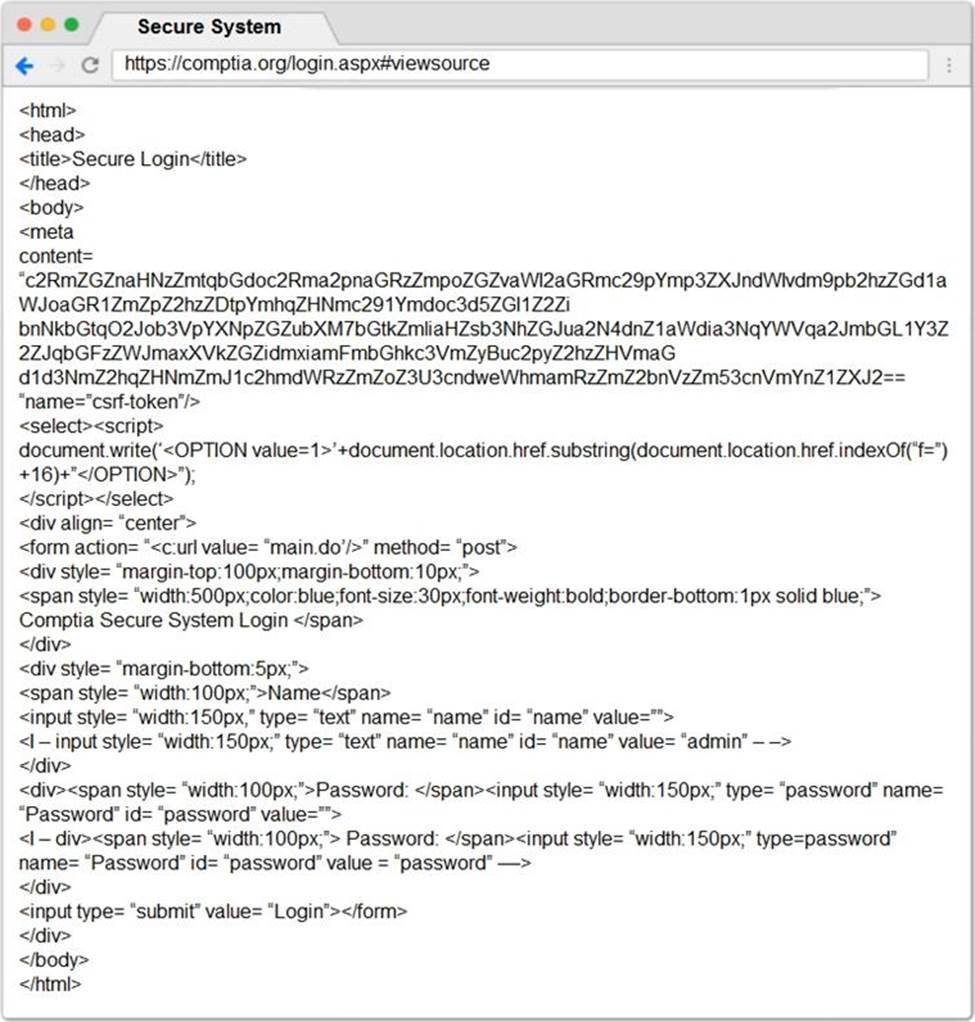
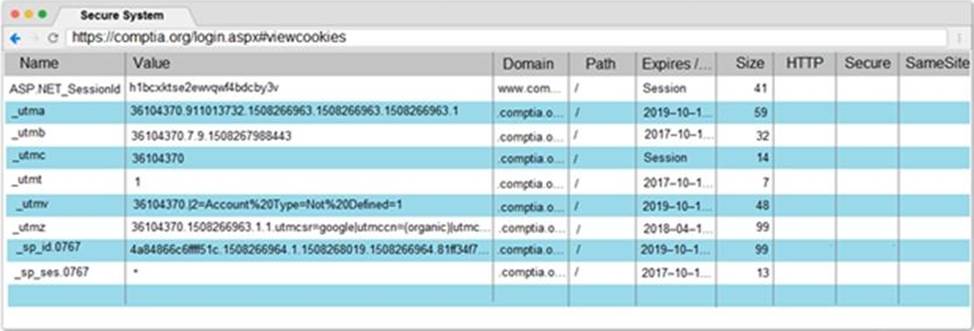
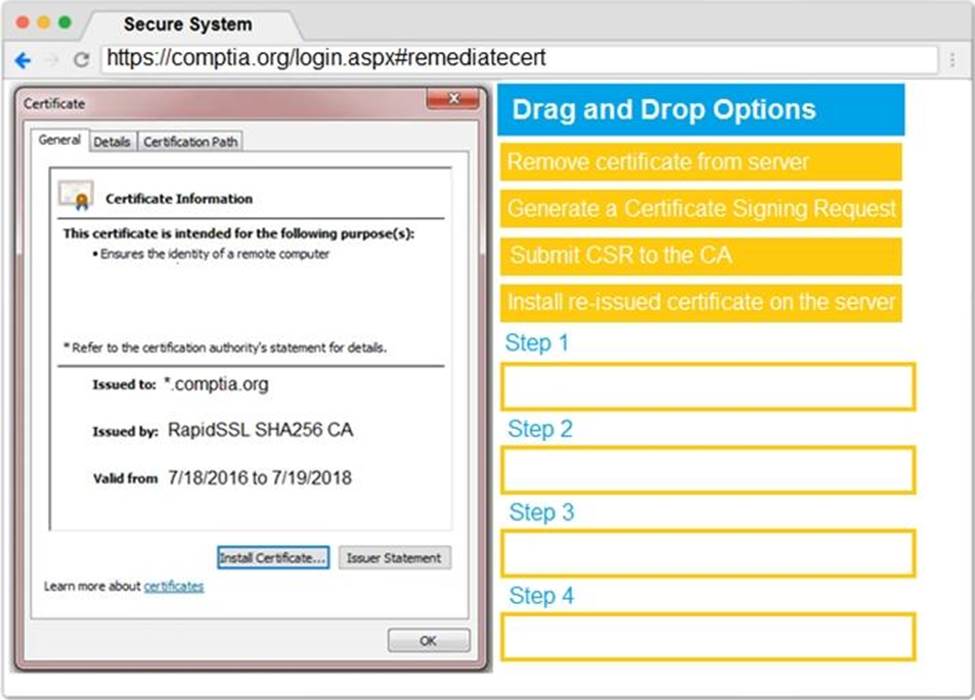
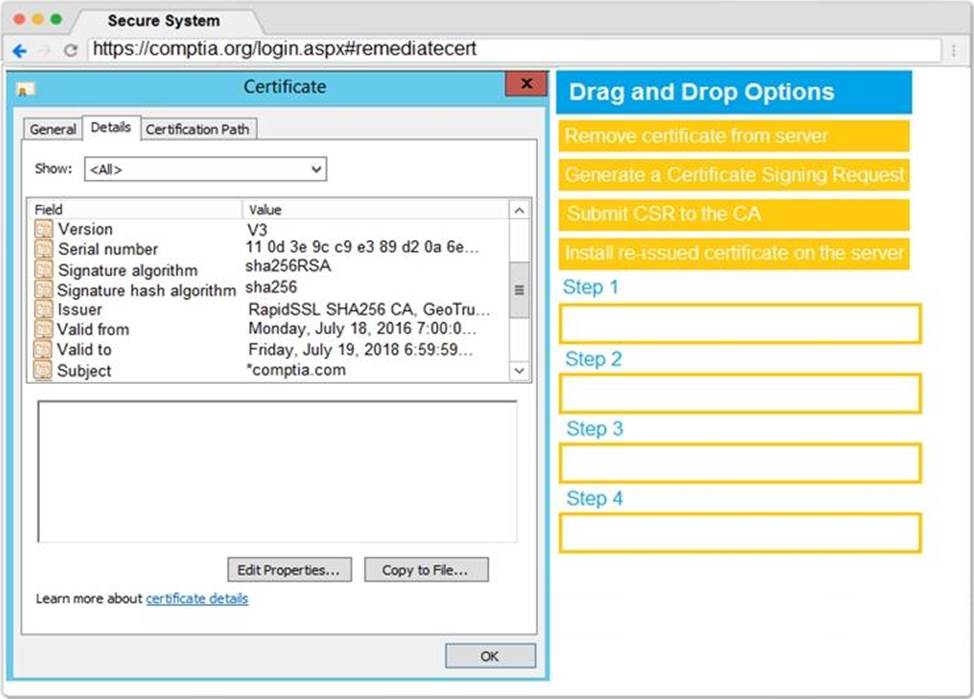
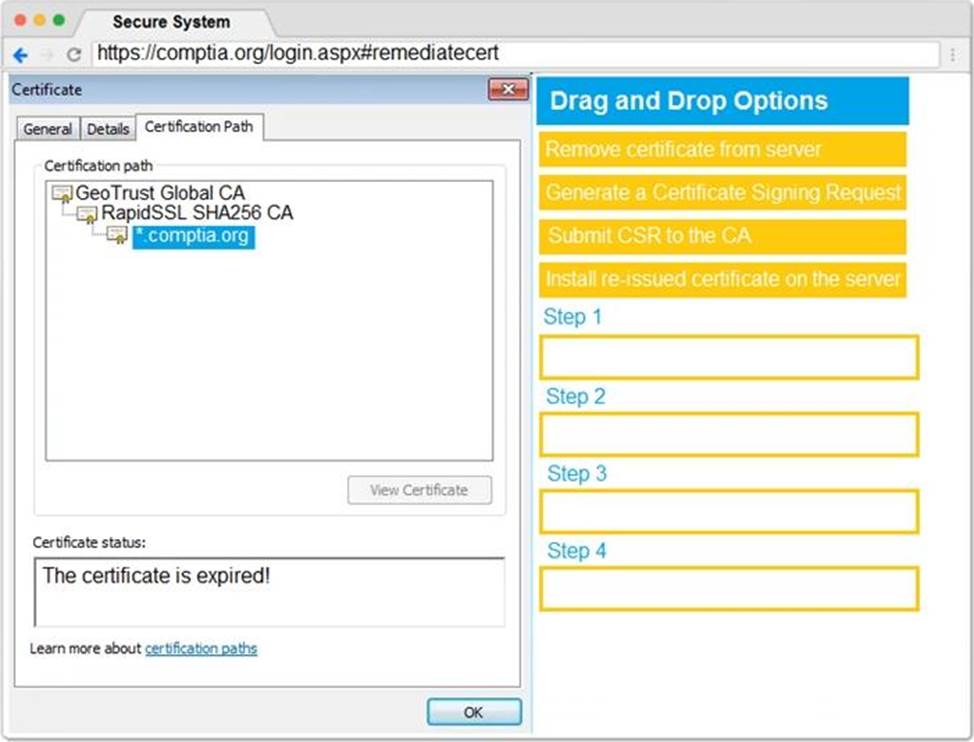
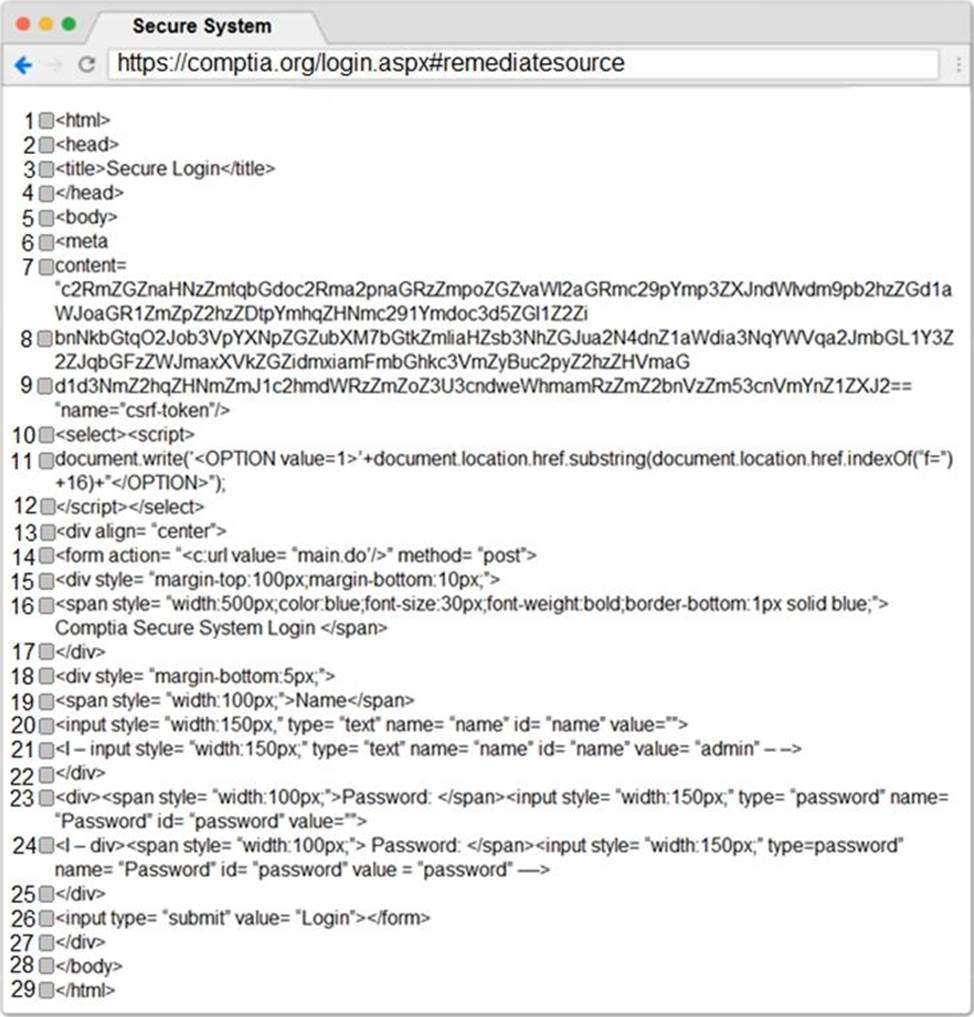
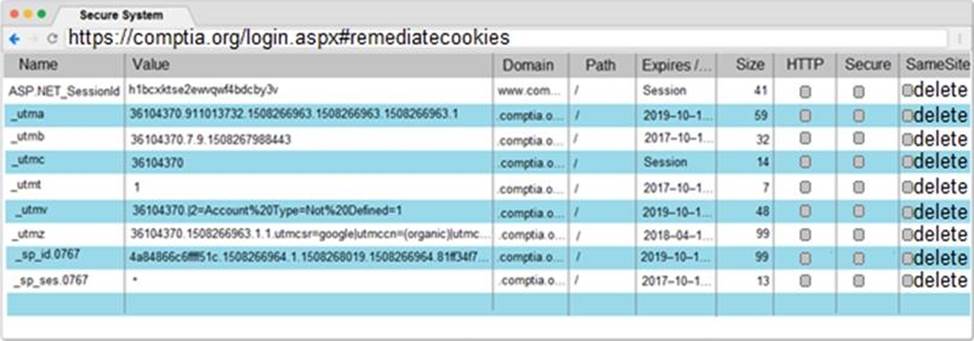
Step 2 – Submit CSR to the CA
Step 3 – Install re-issued certificate on the server
Step 4 – Remove Certificate from Server
A penetration tester runs a script that queries the domain controller for user service principal names .
Which of the following techniques is MOST likely being attempted?
- A . LSASS credential extraction
- B . Cpassword
- C . Cleartext credentials in LDAP
- D . Kerberoasting
D
Explanation:
Reference: https://attack.stealthbits.com/cracking-kerberos-tgs-tickets-using-kerberoasting
A security assessor is attempting to craft specialized XML files to test the security of the parsing functions during ingest into a Windows application.
Before beginning to test the application, which of the following should the assessor request from the organization?
- A . Sample SOAP messages
- B . The REST API documentation
- C . A protocol fuzzing utility
- D . An applicable XSD file
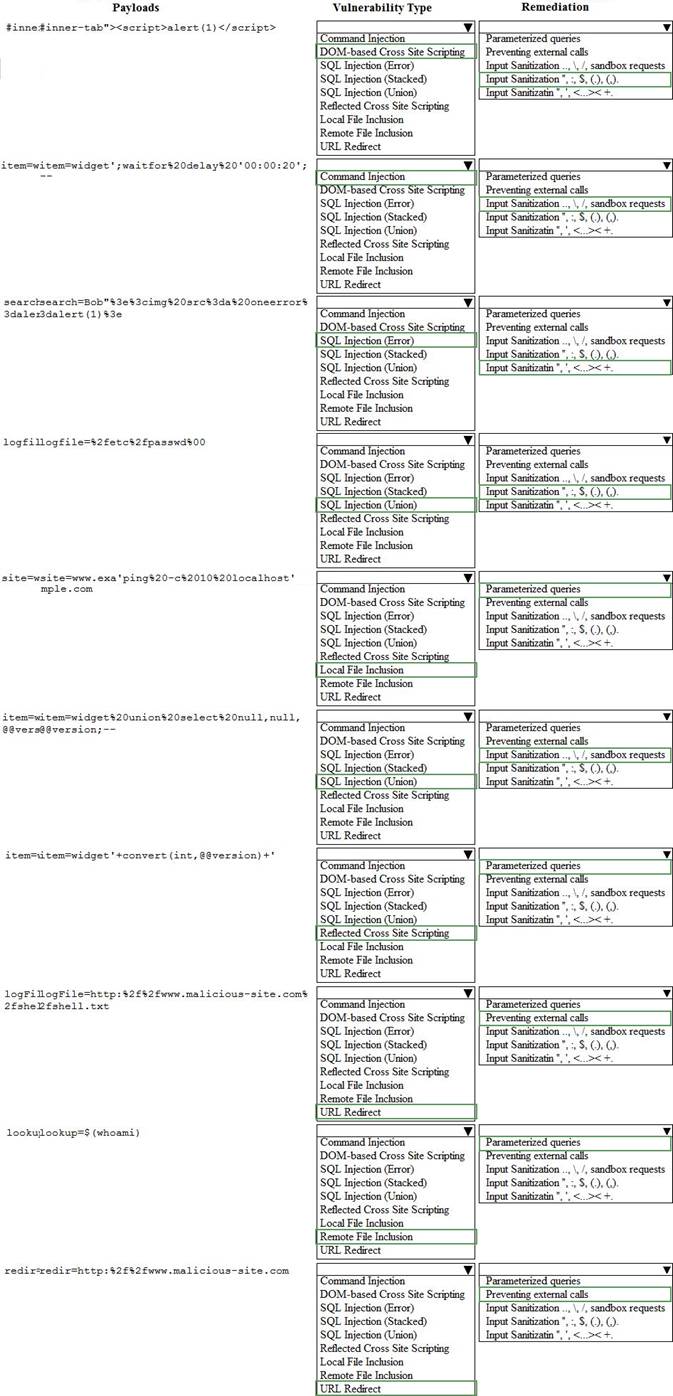
HOTSPOT
Instructions:
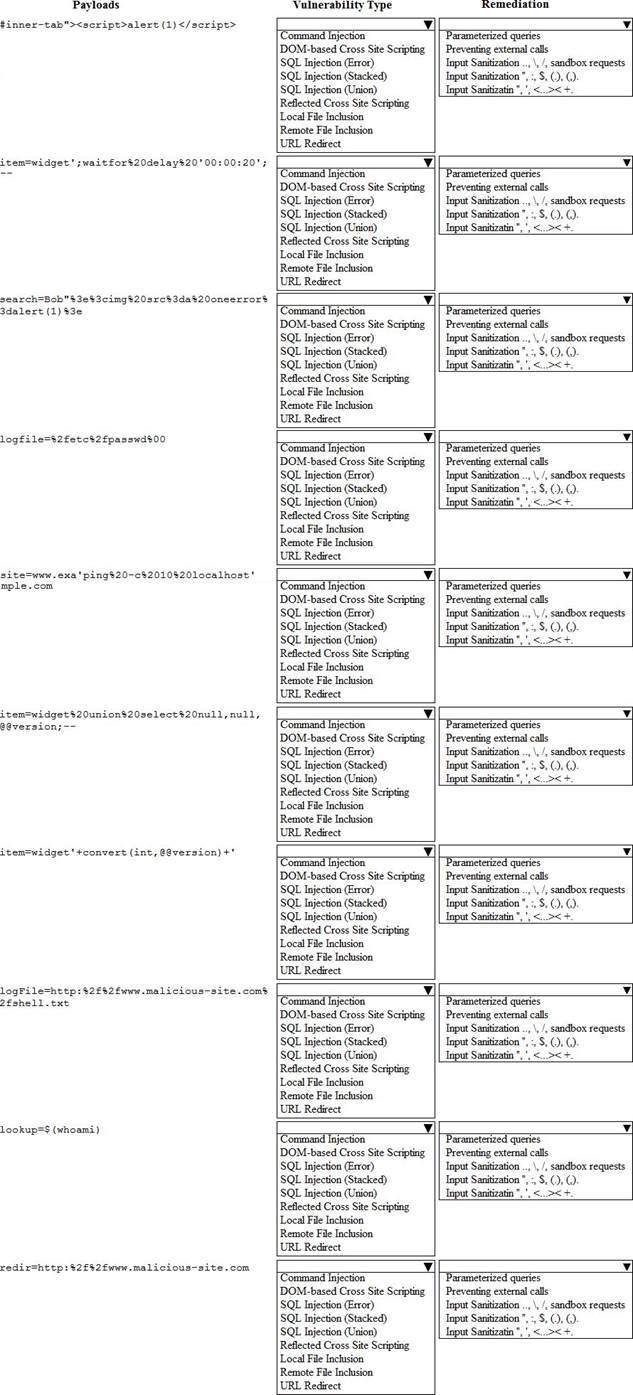
Given the following attack signatures, determine the attack type, and then identify the associated remediation to prevent the attack in the future.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
You are a security analyst tasked with hardening a web server.
You have been given a list of HTTP payloads that were flagged as malicious.
A penetration tester has successfully deployed an evil twin and is starting to see some victim traffic. The next step the penetration tester wants to take is to capture all the victim web traffic unencrypted .
Which of the following would BEST meet this goal?
- A . Perform an HTTP downgrade attack.
- B . Harvest the user credentials to decrypt traffic.
- C . Perform an MITM attack.
- D . Implement a CA attack by impersonating trusted CAs.
Latest PT0-001 Dumps Valid Version with 248 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

