CompTIA N10-008 CompTIA Network+Exam Online Training
CompTIA N10-008 Online Training
The questions for N10-008 were last updated at Apr 03,2025.
- Exam Code: N10-008
- Exam Name: CompTIA Network+Exam
- Certification Provider: CompTIA
- Latest update: Apr 03,2025
A systems administrator needs to improve WiFi performance in a densely populated office tower and use the latest standard. There is a mix of devices that use 2.4 GHz and 5 GHz.
Which of the following should the systems administrator select to meet this requirement?
- A . 802.11ac
- B . 802.11ax
- C . 802.11g
- D . 802.11n
A systems administrator needs to improve WiFi performance in a densely populated office tower and use the latest standard. There is a mix of devices that use 2.4 GHz and 5 GHz.
Which of the following should the systems administrator select to meet this requirement?
- A . 802.11ac
- B . 802.11ax
- C . 802.11g
- D . 802.11n
Which of the following would be BEST to use to detect a MAC spoofing attack?
- A . Internet Control Message Protocol
- B . Reverse Address Resolution Protocol
- C . Dynamic Host Configuration Protocol
- D . Internet Message Access Protocol
A technician receives feedback that some users are experiencing high amounts of jitter while using the wireless network. While troubleshooting the network, the technician uses the ping command with the IP address of the default gateway and verifies large variations in latency. The technician thinks the issue may be interference from other networks and non-802.11 devices.
Which of the following tools should the technician use to troubleshoot the issue?
- A . NetFlow analyzer
- B . Bandwidth analyzer
- C . Protocol analyzer
- D . Spectrum analyzer
Wireless users are reporting intermittent internet connectivity. Connectivity is restored when the users disconnect and reconnect, utilizing the web authentication process each time. The network administrator can see the devices connected to the APs at all times.
Which of the following steps will MOST likely determine the cause of the issue?
- A . Verify the session time-out configuration on the captive portal settings
- B . Check for encryption protocol mismatch on the client’s wireless settings
- C . Confirm that a valid passphrase is being used during the web authentication
- D . Investigate for a client’s disassociation caused by an evil twin AP
A network administrator walks into a datacenter and notices an unknown person is following closely. The administrator stops and directs the person to the security desk.
Which of the following attacks did the network administrator prevent?
- A . Evil twin
- B . Tailgating
- C . Piggybacking
- D . Shoulder surfing
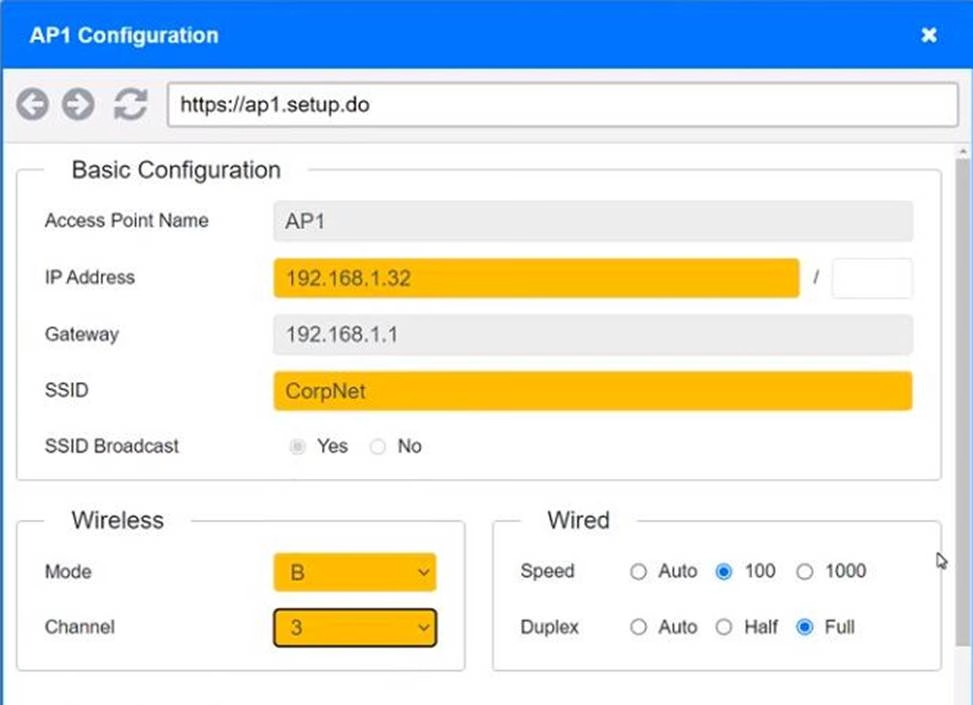
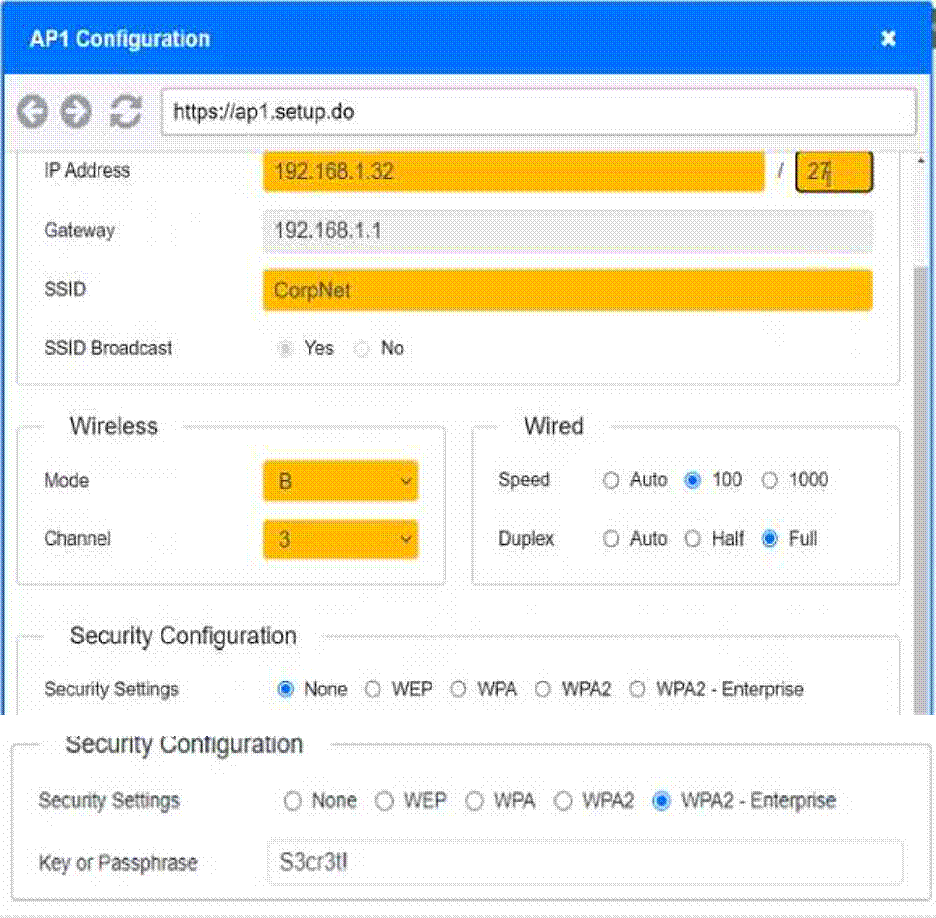
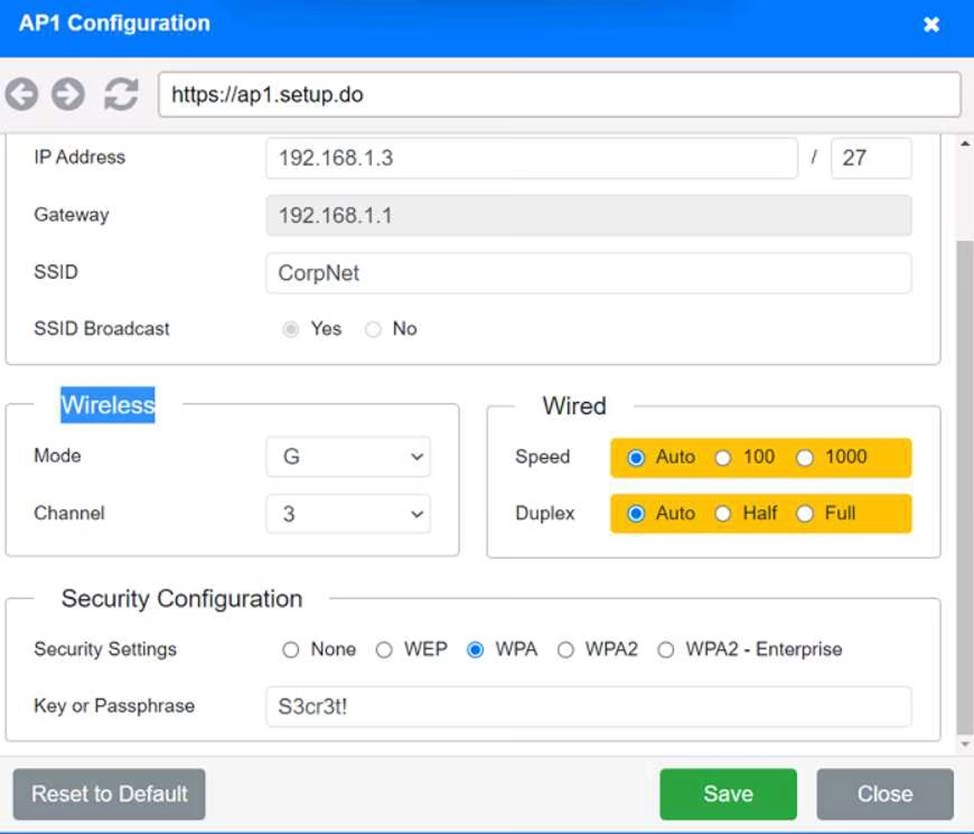
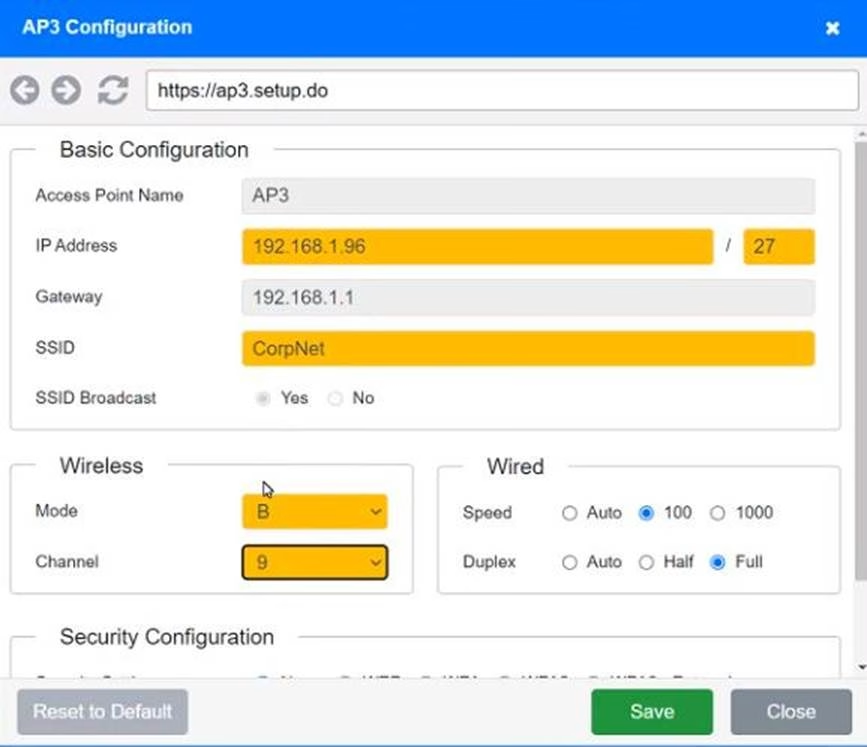
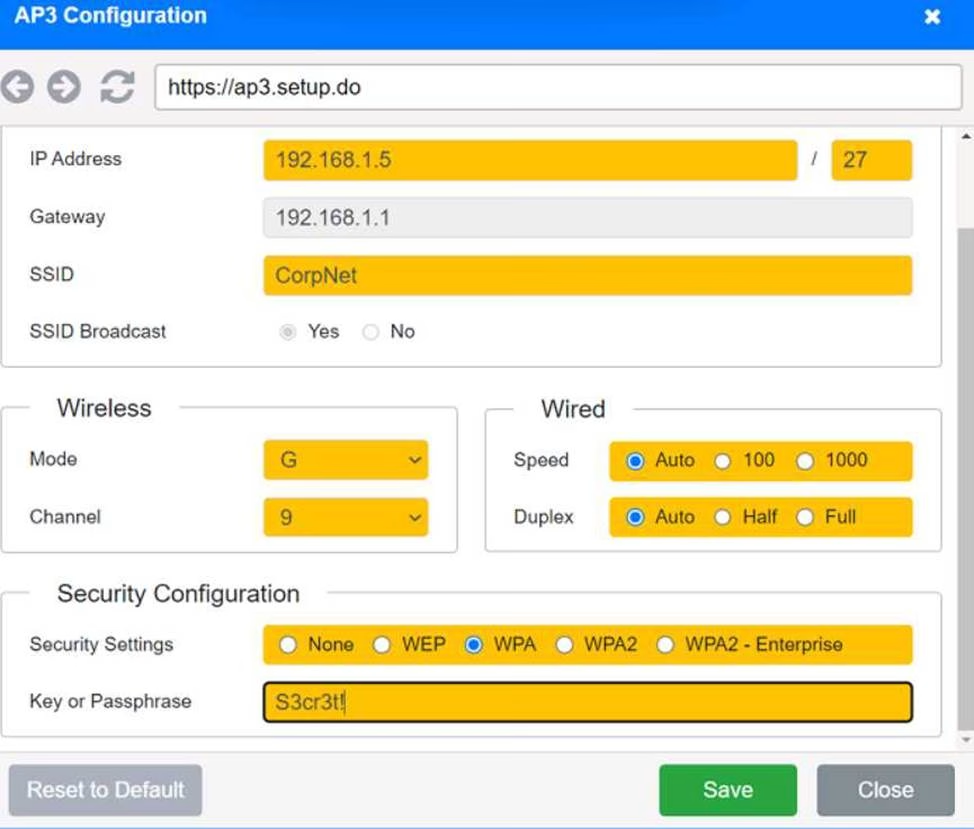
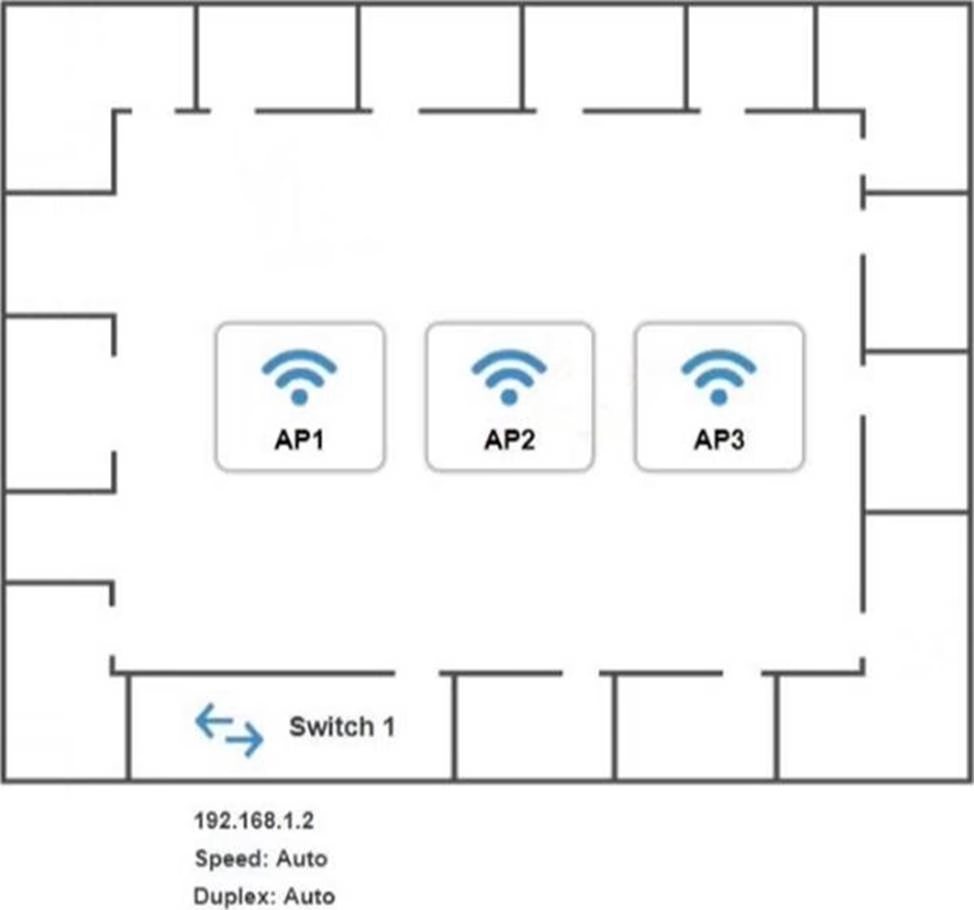
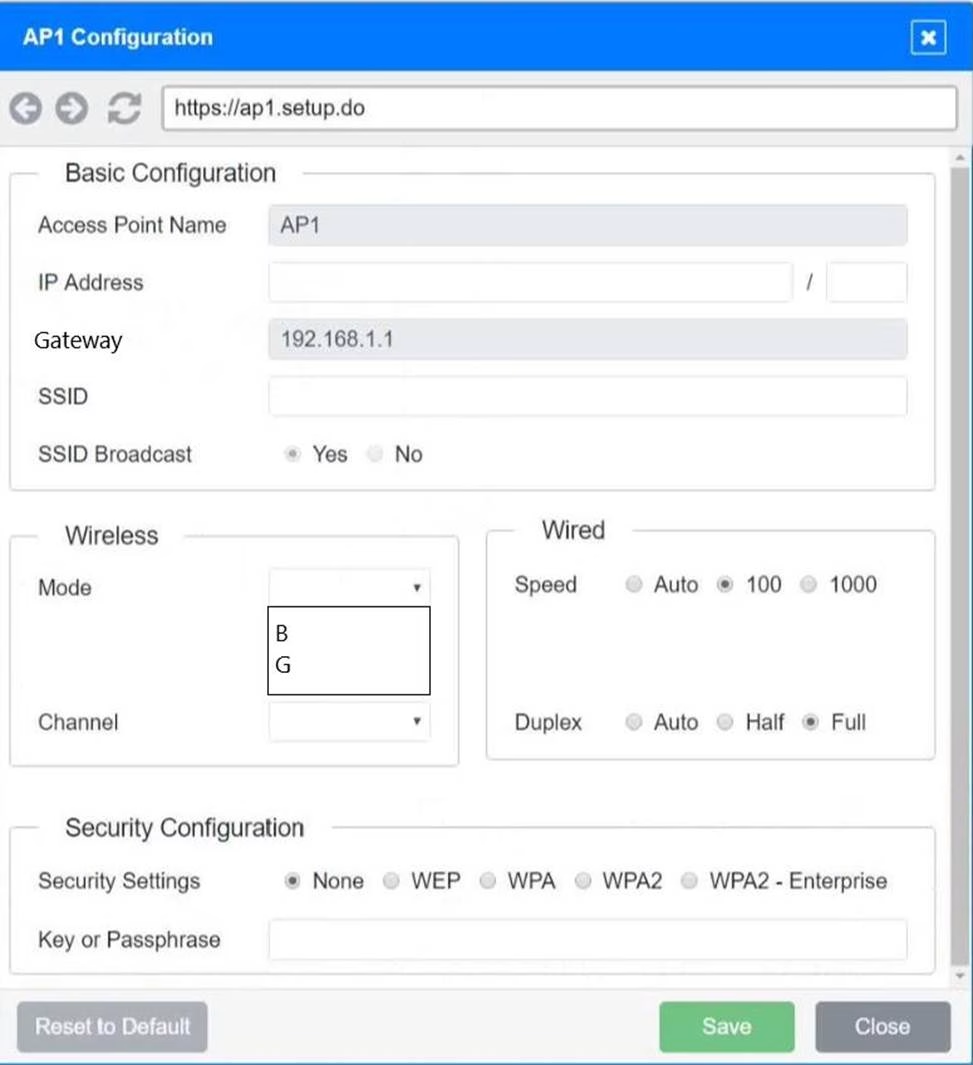
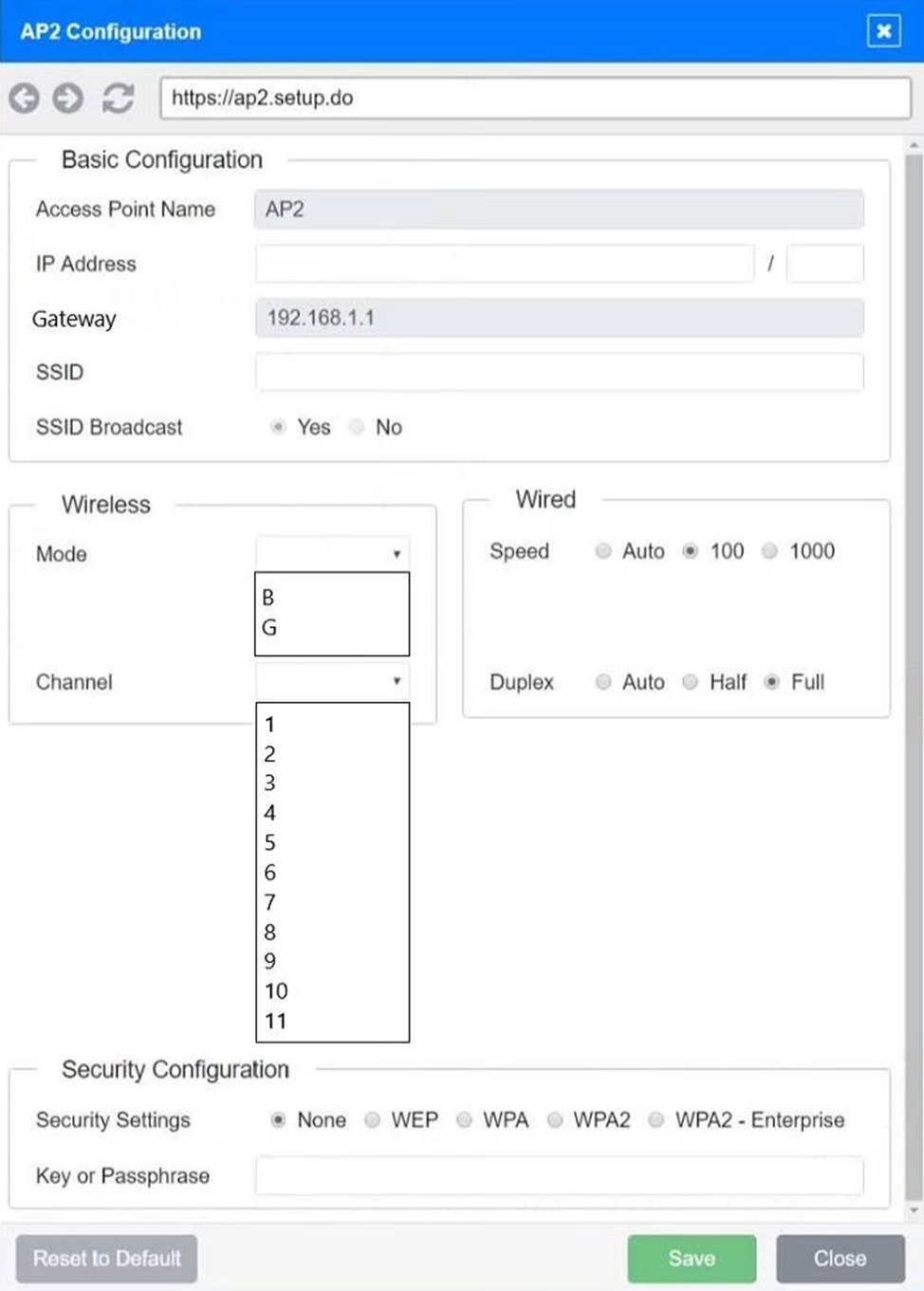
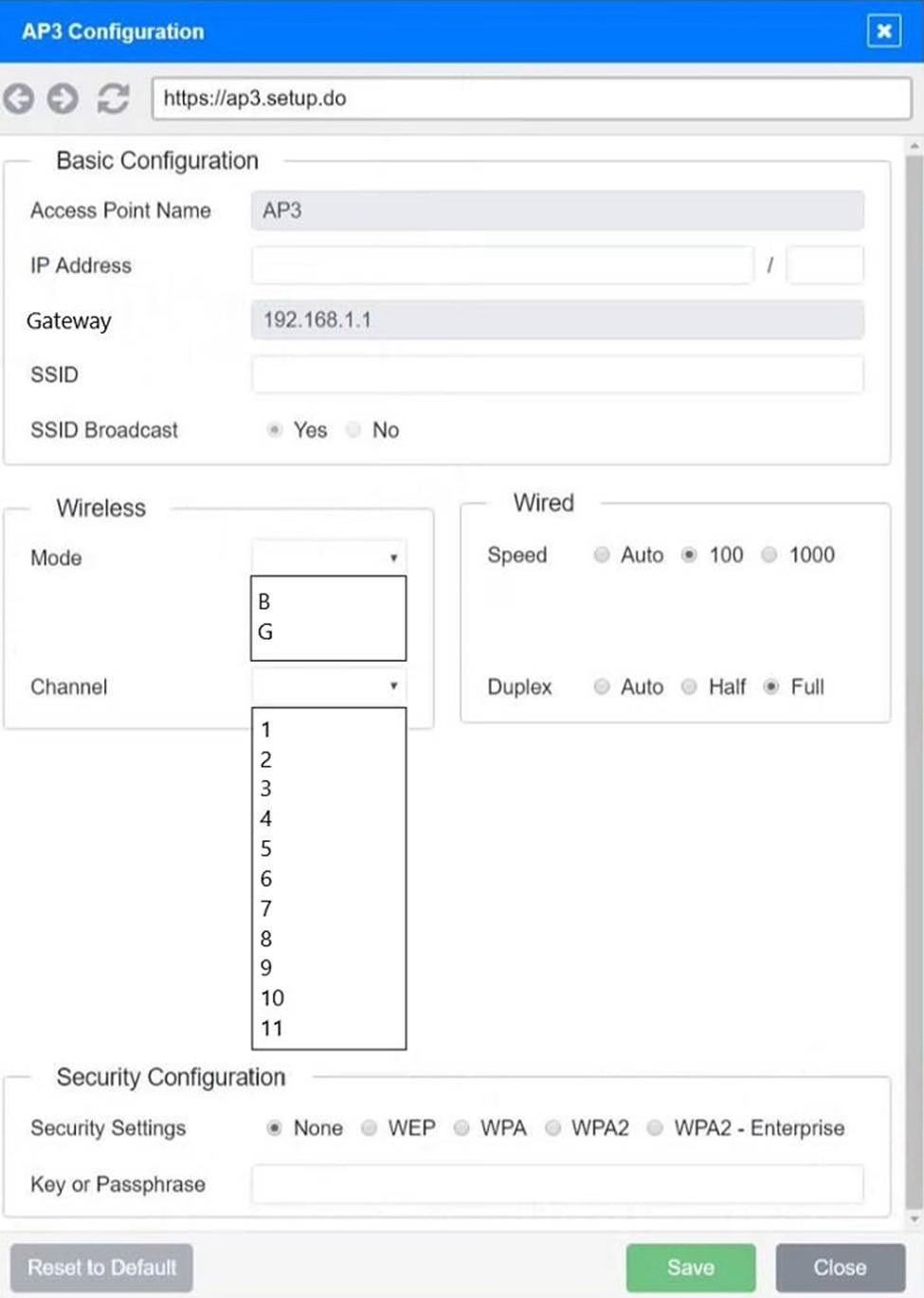
SIMULATION
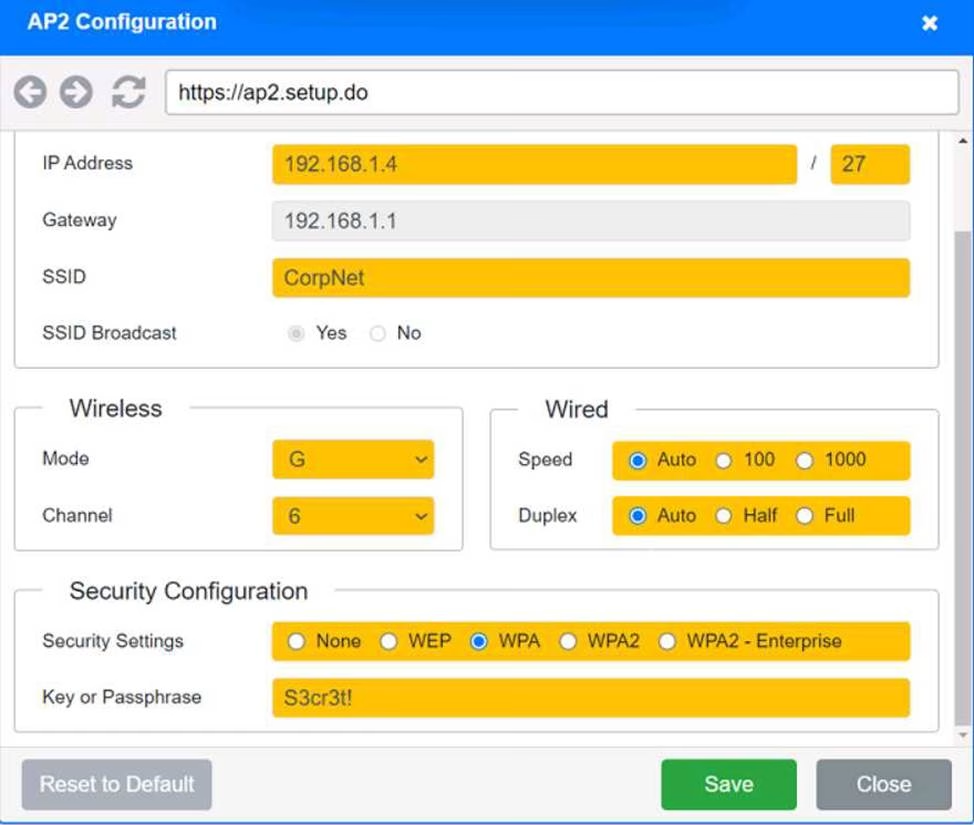
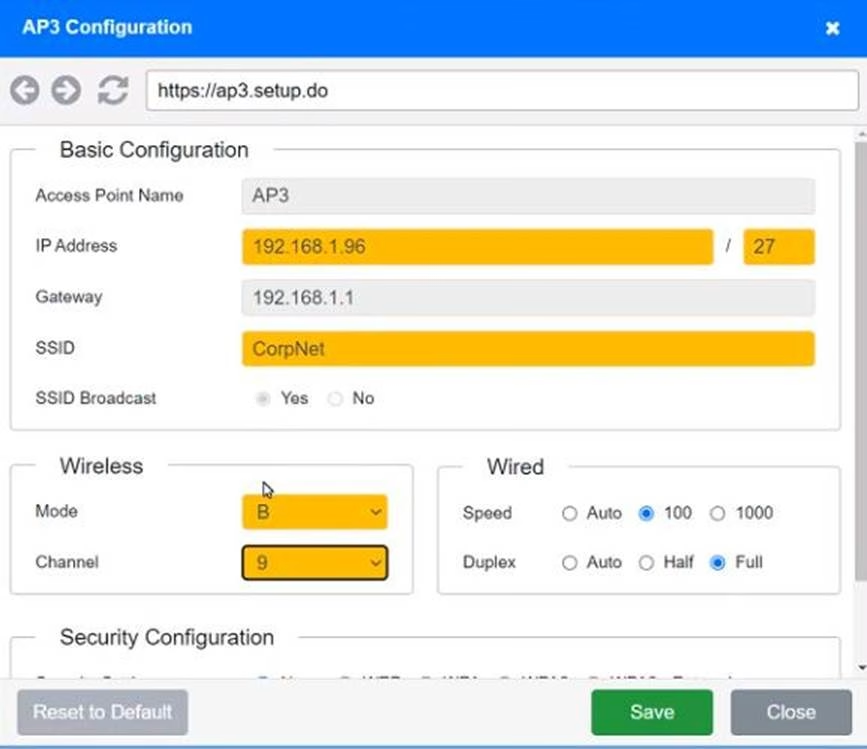
You have been tasked with setting up a wireless network in an office. The network will consist of 3 Access Points and a single switch.
The network must meet the following parameters:
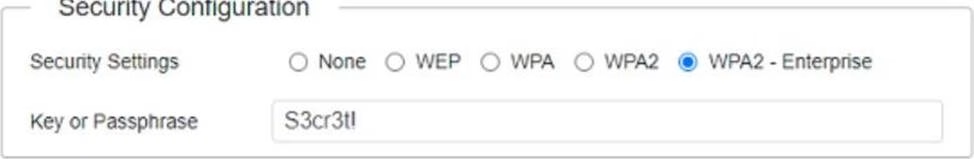
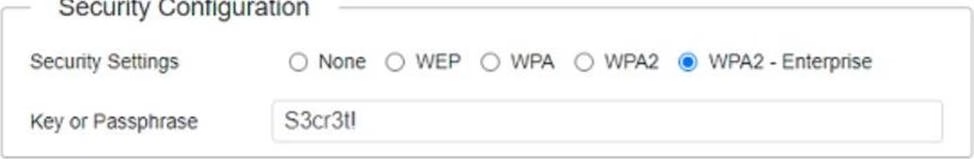
The SSIDs need to be configured as CorpNet with a key of S3cr3t!
The wireless signals should not interfere with each other
The subnet the Access Points and switch are on should only support 30 devices maximum The Access Points should be configured to only support TKIP clients at a maximum speed
INSTRUCTONS
Click on the wireless devices and review their information and adjust the settings of the access points to meet the given requirements.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
A network is experiencing a number of CRC errors during normal network communication.
At which of the following layers of the OSI model will the administrator MOST likely start to troubleshoot?
- A . Layer 1
- B . Layer 2
- C . Layer 3
- D . Layer 4
- E . Layer 5
- F . Layer 6
- G . Layer 7
A client recently added 100 users who are using VMs. All users have since reported slow or unresponsive desktops. Reports show minimal network congestion, zero packet loss, and acceptable packet delay.
Which of the following metrics will MOST accurately show the underlying performance issues? (Choose two.)
- A . CPU usage
- B . Memory
- C . Temperature
- D . Bandwidth
- E . Latency
- F . Jitter
Client devices cannot enter a network, and the network administrator determines the DHCP scope is exhausted. The administrator wants to avoid creating a new DHCP pool.
Which of the following can the administrator perform to resolve the issue?
- A . Install load balancers
- B . Install more switches
- C . Decrease the number of VLANs
- D . Reduce the lease time
Latest N10-008 Dumps Valid Version with 132 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund