CompTIA CS0-003 CompTIA Cybersecurity Analyst (CySA+) Exam Online Training
CompTIA CS0-003 Online Training
The questions for CS0-003 were last updated at Mar 01,2025.
- Exam Code: CS0-003
- Exam Name: CompTIA Cybersecurity Analyst (CySA+) Exam
- Certification Provider: CompTIA
- Latest update: Mar 01,2025
A digital forensics investigator works from duplicate images to preserve the integrity of the original evidence.
Which of the following types of media are most volatile and should be preserved? (Select two).
- A . Memory cache
- B . Registry file
- C . SSD storage
- D . Temporary filesystems
- E . Packet decoding
- F . Swap volume
A development team recently released a new version of a public-facing website for testing prior to
production. The development team is soliciting the help of various teams to validate the functionality of the website due to its high visibility.
Which of the following activities best describes the process the development team is initiating?
- A . Static analysis
- B . Stress testing
- C . Code review
- D . User acceptance testing
A security technician is testing a solution that will prevent outside entities from spoofing the company’s email domain, which is compatia.org. The testing is successful, and the security technician is prepared to fully implement the solution.
Which of the following actions should the technician take to accomplish this task?
- A . Add TXT @ "v=spfl mx include:_spf.comptia. org -all" to the DNS record.
- B . Add : XT @ "v=spfl mx include:_sp£.comptia.org -all" to the email server.
- C . Add TXT @ "v=spfl mx include:_sp£.comptia.org +all" to the domain controller.
- D . AddTXT @ "v=apfl mx lnclude:_spf .comptia.org +a 11" to the web server.
A security analyst who works in the SOC receives a new requirement to monitor for indicators of
compromise.
Which of the following is the first action the analyst should take in this situation?
- A . Develop a dashboard to track the indicators of compromise.
- B . Develop a query to search for the indicators of compromise.
- C . Develop a new signature to alert on the indicators of compromise.
- D . Develop a new signature to block the indicators of compromise.
During an investigation, an analyst discovers the following rule in an executive’s email client:
![]()
The executive is not aware of this rule.
Which of the following should the analyst do first to evaluate the potential impact of this security incident?
- A . Check the server logs to evaluate which emails were sent to <someaddress@domain,com>.
- B . Use the SIEM to correlate logging events from the email server and the domain server.
- C . Remove the rule from the email client and change the password.
- D . Recommend that the management team implement SPF and DKIM.
A security analyst is investigating a compromised Linux server.
The analyst issues the ps command and receives the following output:

Which of the following commands should the administrator run next to further analyze the compromised system?
- A . gbd /proc/1301
- B . rpm -V openssh-server
- C . /bin/Is -1 /proc/1301/exe
- D . kill -9 1301
The following output is from a tcpdump al the edge of the corporate network:
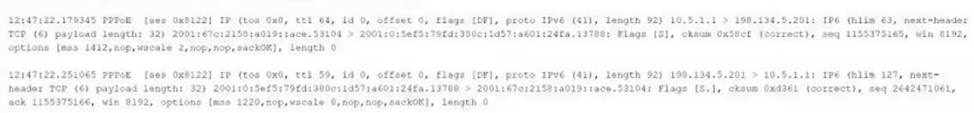
Which of the following best describes the potential security concern?
- A . Payload lengths may be used to overflow buffers enabling code execution.
- B . Encapsulated traffic may evade security monitoring and defenses
- C . This traffic exhibits a reconnaissance technique to create network footprints.
- D . The content of the traffic payload may permit VLAN hopping.
A company’s threat team has been reviewing recent security incidents and looking for a common theme. The team discovered the incidents were caused by incorrect configurations on the impacted systems. The issues were reported to support teams, but no action was taken.
Which of the following is the next step the company should take to ensure any future issues are remediated?
- A . Require support teams to develop a corrective control that ensures security failures are addressed once they are identified.
- B . Require support teams to develop a preventive control that ensures new systems are built with the required security configurations.
- C . Require support teams to develop a detective control that ensures they continuously assess systems for configuration errors.
- D . Require support teams to develop a managerial control that ensures systems have a documented configuration baseline.
A product manager is working with an analyst to design a new application that will perform as a data analytics platform and will be accessible via a web browser. The product manager suggests using a PaaS provider to host the application.
Which of the following is a security concern when using a PaaS solution?
- A . The use of infrastructure-as-code capabilities leads to an increased attack surface.
- B . Patching the underlying application server becomes the responsibility of the client.
- C . The application is unable to use encryption at the database level.
- D . Insecure application programming interfaces can lead to data compromise.
A security analyst performs a weekly vulnerability scan on a network that has 240 devices and receives a report with 2.450 pages.
Which of the following would most likely decrease the number of false positives?
- A . Manual validation
- B . Penetration testing
- C . A known-environment assessment
- D . Credentialed scanning
Latest CS0-003 Dumps Valid Version with 128 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

