CompTIA CS0-003 CompTIA Cybersecurity Analyst (CySA+) Exam Online Training
CompTIA CS0-003 Online Training
The questions for CS0-003 were last updated at Mar 01,2025.
- Exam Code: CS0-003
- Exam Name: CompTIA Cybersecurity Analyst (CySA+) Exam
- Certification Provider: CompTIA
- Latest update: Mar 01,2025
An analyst has been asked to validate the potential risk of a new ransomware campaign that the Chief Financial Officer read about in the newspaper. The company is a manufacturer of a very small spring used in the newest fighter jet and is a critical piece of the supply chain for this aircraft.
Which of the following would be the best threat intelligence source to learn about this new campaign?
- A . Information sharing organization
- B . Blogs/forums
- C . Cybersecurity incident response team
- D . Deep/dark web
An incident response team finished responding to a significant security incident. The management team has asked the lead analyst to provide an after-action report that includes lessons learned.
Which of the following is the most likely reason to include lessons learned?
- A . To satisfy regulatory requirements for incident reporting
- B . To hold other departments accountable
- C . To identify areas of improvement in the incident response process
- D . To highlight the notable practices of the organization’s incident response team
A vulnerability management team is unable to patch all vulnerabilities found during their weekly scans.
Using the third-party scoring system described below, the team patches the most urgent vulnerabilities:
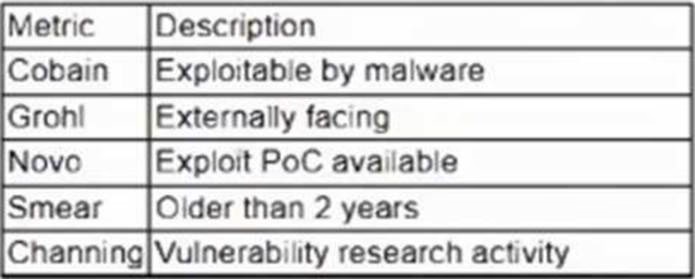
Additionally, the vulnerability management team feels that the metrics Smear and Channing are less important than the others, so these will be lower in priority.
Which of the following vulnerabilities should be patched first, given the above third-party scoring system?
- A . InLoud:
Cobain: Yes
Grohl: No
Novo: Yes
Smear: Yes
Channing: No - B . TSpirit:
Cobain: Yes
Grohl: Yes
Novo: Yes
Smear: No
Channing: No - C . ENameless:
Cobain: Yes
Grohl: No
Novo: Yes
Smear: No
Channing: No - D . PBleach:
Cobain: Yes
Grohl: No
Novo: No
Smear: No
Channing: Yes
A user downloads software that contains malware onto a computer that eventually infects numerous other systems.
Which of the following has the user become?
- A . Hacklivist
- B . Advanced persistent threat
- C . Insider threat
- D . Script kiddie
An organization has activated the CSIRT. A security analyst believes a single virtual server was compromised and immediately isolated from the network.
Which of the following should the CSIRT conduct next?
- A . Take a snapshot of the compromised server and verify its integrity
- B . Restore the affected server to remove any malware
- C . Contact the appropriate government agency to investigate
- D . Research the malware strain to perform attribution
During an incident, an analyst needs to acquire evidence for later investigation.
Which of the following must be collected first in a computer system, related to its volatility level?
- A . Disk contents
- B . Backup data
- C . Temporary files
- D . Running processes
A security analyst is trying to identify possible network addresses from different source networks belonging to the same company and region.
Which of the following shell script functions could help achieve the goal?
- A . function w() { a=$(ping -c 1 $1 | awk-F ”/” ’END{print $1}’) && echo “$1 | $a” }
- B . function x() { b=traceroute -m 40 $1 | awk ’END{print $1}’) && echo “$1 | $b” }
- C . function y() { dig $(dig -x $1 | grep PTR | tail -n 1 | awk -F ”.in-addr” ’{print $1}’).origin.asn.cymru.com TXT +short }
- D . function z() { c=$(geoiplookup$1) && echo “$1 | $c” }
A security analyst is writing a shell script to identify IP addresses from the same country.
Which of the following functions would help the analyst achieve the objective?
- A . function w() { info=$(ping -c 1 $1 | awk -F “/” ‘END{print $1}’) && echo “$1 | $info” }
- B . function x() { info=$(geoiplookup $1) && echo “$1 | $info” }
- C . function y() { info=$(dig -x $1 | grep PTR | tail -n 1 ) && echo “$1 | $info” }
- D . function z() { info=$(traceroute -m 40 $1 | awk ‘END{print $1}’) && echo “$1 | $info” }
A security analyst obtained the following table of results from a recent vulnerability assessment that was conducted against a single web server in the environment:
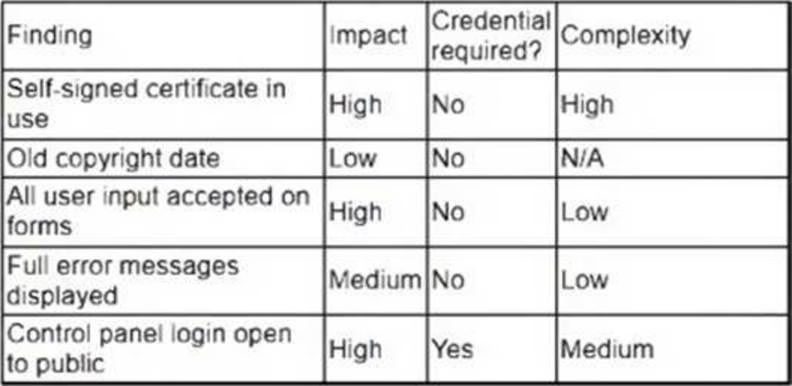
Which of the following should be completed first to remediate the findings?
- A . Ask the web development team to update the page contents
- B . Add the IP address allow listing for control panel access
- C . Purchase an appropriate certificate from a trusted root CA
- D . Perform proper sanitization on all fields
A user reports a malware alert to the help desk. A technician verities the alert, determines the workstation is classified as a low-severity device, and uses network controls to block access. The technician then assigns the ticket to a security analyst who will complete the eradication and recovery processes.
Which of the following should the security analyst do next?
- A . Document the procedures and walk through the incident training guide.
- B . Reverse engineer the malware to determine its purpose and risk to the organization.
- C . Sanitize the workstation and verify countermeasures are restored.
- D . Isolate the workstation and issue a new computer to the user.
Latest CS0-003 Dumps Valid Version with 128 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

