CompTIA CS0-003 CompTIA Cybersecurity Analyst (CySA+) Exam Online Training
CompTIA CS0-003 Online Training
The questions for CS0-003 were last updated at Mar 01,2025.
- Exam Code: CS0-003
- Exam Name: CompTIA Cybersecurity Analyst (CySA+) Exam
- Certification Provider: CompTIA
- Latest update: Mar 01,2025
A Chief Information Officer wants to implement a BYOD strategy for all company laptops and mobile phones. The Chief Information Security Officer is concerned with ensuring all devices are patched and running some sort of protection against malicious software.
Which of the following existing technical controls should a security analyst recommend to best meet all the requirements?
- A . EDR
- B . Port security
- C . NAC
- D . Segmentation
A security analyst discovers the accounting department is hosting an accounts receivable form on a public document service. Anyone with the link can access it.
Which of the following threats applies to this situation?
- A . Potential data loss to external users
- B . Loss of public/private key management
- C . Cloud-based authentication attack
- D . Identification and authentication failures
A security analyst is supporting an embedded software team.
Which of the following is the best recommendation to ensure proper error handling at runtime?
- A . Perform static code analysis.
- B . Require application fuzzing.
- C . Enforce input validation.
- D . Perform a code review.
The steering committee for information security management annually reviews the security incident register for the organization to look for trends and systematic issues. The steering committee wants to rank the risks based on past incidents to improve the security program for next year.
Below is the incident register for the organization:
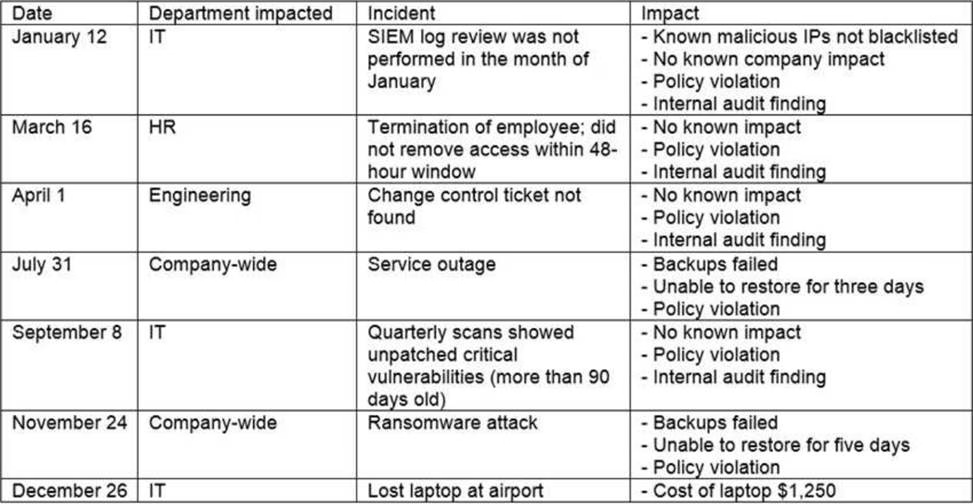
Which of the following should the organization consider investing in first due to the potential impact of availability?
- A . Hire a managed service provider to help with vulnerability management.
- B . Build a warm site in case of system outages.
- C . Invest in a failover and redundant system, as necessary.
- D . Hire additional staff for the IT department to assist with vulnerability management and log review.
A cybersecurity analyst is concerned about attacks that use advanced evasion techniques.
Which of the following would best mitigate such attacks?
- A . Keeping IPS rules up to date
- B . Installing a proxy server
- C . Applying network segmentation
- D . Updating the antivirus software
Legacy medical equipment, which contains sensitive data, cannot be patched.
Which of the following is the best solution to improve the equipment’s security posture?
- A . Move the legacy systems behind a WAR
- B . Implement an air gap for the legacy systems.
- C . Place the legacy systems in the perimeter network.
- D . Implement a VPN between the legacy systems and the local network.
A security analyst notices the following proxy log entries:
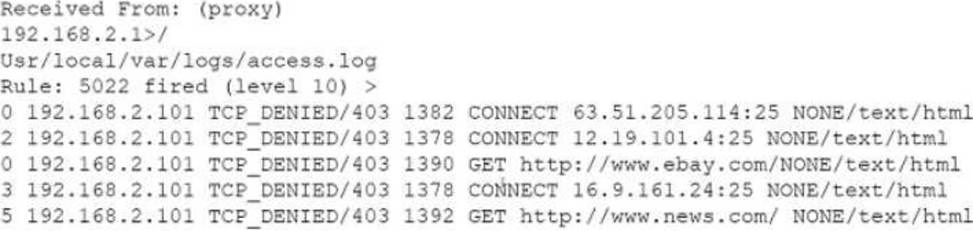
Which of the following is the user attempting to do based on the log entries?
- A . Use a DoS attack on external hosts.
- B . Exfiltrate data.
- C . Scan the network.
- D . Relay email.
A company’s legal department is concerned that its incident response plan does not cover the countless ways security incidents can occur. The department has asked a security analyst to help tailor the response plan to provide broad coverage for many situations.
Which of the following is the best way to achieve this goal?
- A . Focus on incidents that have a high chance of reputation harm.
- B . Focus on common attack vectors first.
- C . Focus on incidents that affect critical systems.
- D . Focus on incidents that may require law enforcement support.
During a company’s most recent incident, a vulnerability in custom software was exploited on an externally facing server by an APT.
The lessons-learned report noted the following:
• The development team used a new software language that was not supported by the security team’s automated assessment tools.
• During the deployment, the security assessment team was unfamiliar with the new language and struggled to evaluate the software during advanced testing. Therefore, the vulnerability was not detected.
• The current IPS did not have effective signatures and policies in place to detect and prevent
runtime attacks on the new application.
To allow this new technology to be deployed securely going forward, which of the following will BEST address these findings? (Choose two.)
- A . Train the security assessment team to evaluate the new language and verify that best practices for secure coding have been followed
- B . Work with the automated assessment-tool vendor to add support for the new language so these vulnerabilities are discovered automatically
- C . Contact the human resources department to hire new security team members who are already familiar with the new language
- D . Run the software on isolated systems so when they are compromised, the attacker cannot pivot to adjacent systems
- E . Instruct only the development team to document the remediation steps for this vulnerability
- F . Outsource development and hosting of the applications in the new language to a third-party vendor so the risk is transferred to that provider
Given the Nmap request below:
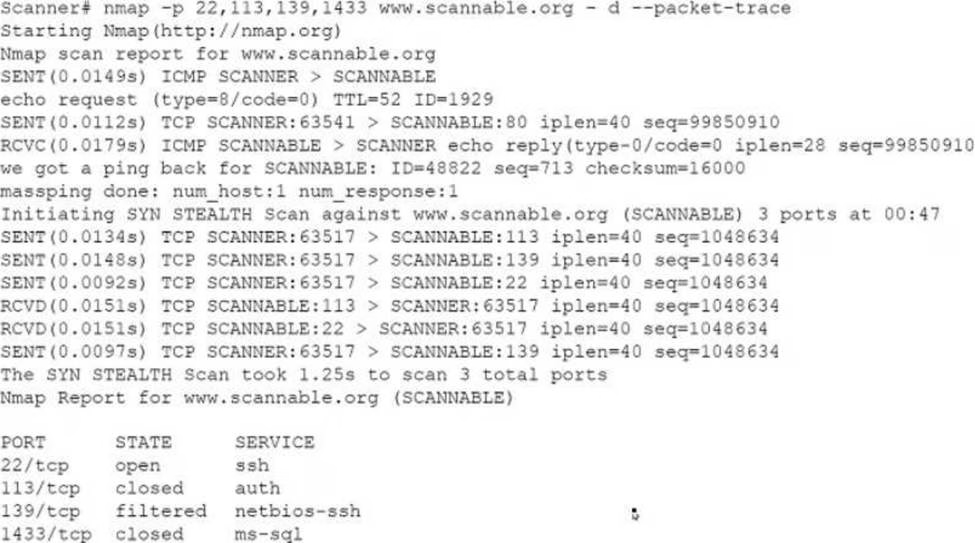
Which of the following actions will an attacker be able to initiate directly against this host?
- A . Password sniffing
- B . ARP spoofing
- C . A brute-force attack
- D . An SQL injection
Latest CS0-003 Dumps Valid Version with 128 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

