CompTIA CS0-002 CompTIA Cybersecurity Analyst (CySA+) Certification Exam Online Training
CompTIA CS0-002 Online Training
The questions for CS0-002 were last updated at Jan 02,2026.
- Exam Code: CS0-002
- Exam Name: CompTIA Cybersecurity Analyst (CySA+) Certification Exam
- Certification Provider: CompTIA
- Latest update: Jan 02,2026
A company’s security administrator needs to automate several security processes related to testing for the existence of changes within the environment Conditionally other processes will need to be created based on input from prior processes
Which of the following is the BEST method for accomplishing this task?
- A . Machine learning and process monitoring
- B . API integration and data enrichment
- C . Workflow orchestration and scripting
- D . Continuous integration and configuration management
An employee in the billing department accidentally sent a spreadsheet containing payment card data to a recipient outside the organization. The employee intended to send the spreadsheet to an internal staff member with a similar name and was unaware of the mistake until the recipient replied to the message.
In addition to retraining the employee, which of the following would prevent this from happening in the future?
- A . Implement outgoing filter rules to quarantine messages that contain card data
- B . Configure the outgoing mail filter to allow attachments only to addresses on the whitelist
- C . Remove all external recipients from the employee’s address book
- D . Set the outgoing mail filter to strip spreadsheet attachments from all messages.
A security analyst is reviewing the following log from an email security service.
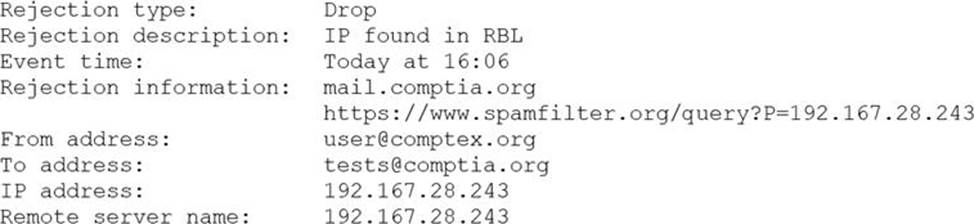
Which of the following BEST describes the reason why the email was blocked?
- A . The To address is invalid.
- B . The email originated from the www.spamfilter.org URL.
- C . The IP address and the remote server name are the same.
- D . The IP address was blacklisted.
- E . The From address is invalid.
Legacy medical equipment, which contains sensitive data, cannot be patched.
Which of the following is the BEST solution to improve the equipment’s security posture?
- A . Move the legacy systems behind a WAF
- B . Implement an air gap for the legacy systems.
- C . Implement a VPN between the legacy systems and the local network.
- D . Place the legacy systems in the DMZ
Massivelog log has grown to 40GB on a Windows server At this size, local tools are unable to read the file, and it cannot be moved off the virtual server where it is located.
Which of the following lines of PowerShell script will allow a user to extract the last 10.000 lines of the loq for review?
- A . tail -10000 Massivelog.log > extract.txt
- B . info tail n -10000 Massivelog.log | extract.txt;
- C . get content ‘./Massivelog.log’ CLast 10000 | extract.txt
- D . get-content ‘./Massivelog.log’ CLast 10000 > extract.txt;
A software development team asked a security analyst to review some code for security vulnerabilities.
Which of the following would BEST assist the security analyst while performing this task?
- A . Static analysis
- B . Dynamic analysis
- C . Regression testing
- D . User acceptance testing
A company recently experienced multiple DNS DDoS attacks, and the information security analyst must provide a DDoS solution to deploy in the company’s datacenter.
Which of the following would BEST prevent future attacks?
- A . Configure a sinkhole on the router.
- B . Buy a UTM to block the number of requests.
- C . Route the queries on the DNS server to 127.0.0.1.
- D . Call the Internet service provider to block the attack.
A Chief Information Security Officer (CISO) is concerned the development team, which consists of contractors, has too much access to customer data. Developers use personal workstations, giving the company little to no visibility into the development activities.
Which of the following would be BEST to implement to alleviate the CISO’s concern?
- A . DLP
- B . Encryption
- C . Test data
- D . NDA
During the forensic analysis of a compromised machine, a security analyst discovers some binaries that are exhibiting abnormal behaviors. After extracting the strings, the analyst finds unexpected content.
Which of the following is the NEXT step the analyst should take?
- A . Only allow whitelisted binaries to execute.
- B . Run an antivirus against the binaries to check for malware.
- C . Use file integrity monitoring to validate the digital signature.
- D . Validate the binaries’ hashes from a trusted source.
A security analyst is researching an incident and uncovers several details that may link to other incidents. The security analyst wants to determine if other incidents are related to the current incident.
Which of the following threat research methodologies would be MOST appropriate for the analyst to use?
- A . Reputation data
- B . CVSS score
- C . Risk assessment
- D . Behavioral analysis
Latest CS0-002 Dumps Valid Version with 220 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund


Thank you for this test, Greatful :):)