CompTIA CS0-002 CompTIA Cybersecurity Analyst (CySA+) Certification Exam Online Training
CompTIA CS0-002 Online Training
The questions for CS0-002 were last updated at Dec 14,2025.
- Exam Code: CS0-002
- Exam Name: CompTIA Cybersecurity Analyst (CySA+) Certification Exam
- Certification Provider: CompTIA
- Latest update: Dec 14,2025
Which of me following BEST articulates the benefit of leveraging SCAP in an organization’s cybersecurity analysis toolset?
- A . It automatically performs remedial configuration changes lo enterprise security services
- B . It enables standard checklist and vulnerability analysis expressions for automaton
- C . It establishes a continuous integration environment for software development operations
- D . It provides validation of suspected system vulnerabilities through workflow orchestration
A company’s blocklist has outgrown the current technologies in place. The ACLS are at maximum, and the IPS signatures only allow a certain
amount of space for domains to be added, creating the need for multiple signatures.
Which of the following configuration changes to the existing controls would be the MOST appropriate to improve performance?
- A . Create an IDS for the current blocklist to determine which domains are showing activity and may need to be removed.
- B . Implement a host-file based solution that will use a list of all domains to deny for all machines on the network
- C . Review the current blocklist to determine which domains can be removed from the list and then update the ACLs and IPS signatures.
- D . Review the current blocklist and prioritize it based on the level of threat severity. Add the domains with the highest severity to the blocklist and remove the lower-severity threats from it.
A system’s authority to operate (ATO) is set to expire in four days. Because of other activities and limited staffing, the organization has neglected to start reauthentication activities until now.
The cybersecurity group just performed a vulnerability scan with the partial set of results shown below:
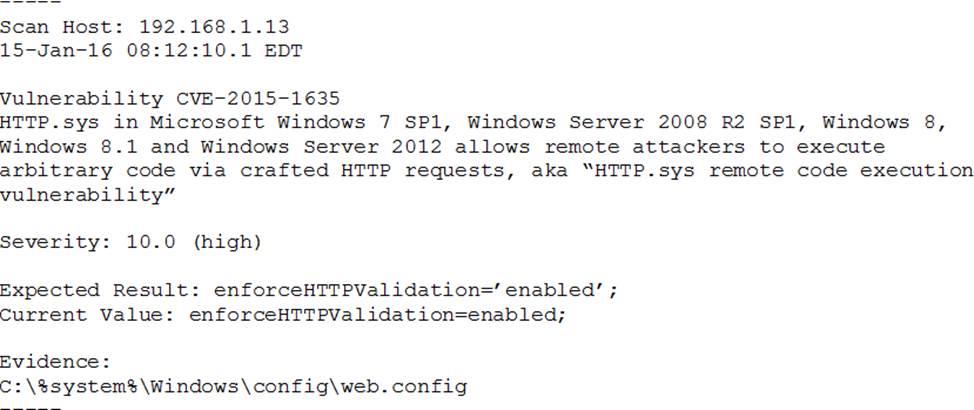
Based on the scenario and the output from the vulnerability scan, which of the following should the security team do with this finding?
- A . Remediate by going to the web config file, searching for the enforce HTTP validation setting, and manually updating to the correct setting.
- B . Accept this risk for now because this is a “high” severity, but testing will require more than the four days available, and the system ATO needs to be competed.
- C . Ignore it. This is false positive, and the organization needs to focus its efforts on other findings.
- D . Ensure HTTP validation is enabled by rebooting the server.
Portions of a legacy application are being refactored to discontinue the use of dynamic SQL.
Which of the following would be BEST to implement in the legacy application?
- A . Multifactor authentication
- B . Web-application firewall
- C . SQL injection
- D . Parameterized queries
- E . Input validation
A Chief Security Officer (CSO) is working on the communication requirements (or an organization’s incident response plan.
In addition to technical response activities, which of the following is the main reason why communication must be addressed in an effective incident response program?
- A . Public relations must receive information promptly in order to notify the community.
- B . Improper communications can create unnecessary complexity and delay response actions.
- C . Organizational personnel must only interact with trusted members of the law enforcement community.
- D . Senior leadership should act as the only voice for the incident response team when working with forensics teams.
A Chief Security Officer (CSO) is working on the communication requirements (or an organization’s incident response plan.
In addition to technical response activities, which of the following is the main reason why communication must be addressed in an effective incident response program?
- A . Public relations must receive information promptly in order to notify the community.
- B . Improper communications can create unnecessary complexity and delay response actions.
- C . Organizational personnel must only interact with trusted members of the law enforcement community.
- D . Senior leadership should act as the only voice for the incident response team when working with forensics teams.
A Chief Security Officer (CSO) is working on the communication requirements (or an organization’s incident response plan.
In addition to technical response activities, which of the following is the main reason why communication must be addressed in an effective incident response program?
- A . Public relations must receive information promptly in order to notify the community.
- B . Improper communications can create unnecessary complexity and delay response actions.
- C . Organizational personnel must only interact with trusted members of the law enforcement community.
- D . Senior leadership should act as the only voice for the incident response team when working with forensics teams.
A Chief Security Officer (CSO) is working on the communication requirements (or an organization’s incident response plan.
In addition to technical response activities, which of the following is the main reason why communication must be addressed in an effective incident response program?
- A . Public relations must receive information promptly in order to notify the community.
- B . Improper communications can create unnecessary complexity and delay response actions.
- C . Organizational personnel must only interact with trusted members of the law enforcement community.
- D . Senior leadership should act as the only voice for the incident response team when working with forensics teams.
A network attack that is exploiting a vulnerability in the SNMP is detected.
Which of the following should the cybersecurity analyst do FIRST?
- A . Apply the required patches to remediate the vulnerability.
- B . Escalate the incident to senior management for guidance.
- C . Disable all privileged user accounts on the network.
- D . Temporarily block the attacking IP address.
Latest CS0-002 Dumps Valid Version with 220 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund


Thank you for this test, Greatful :):)