CompTIA CS0-002 CompTIA Cybersecurity Analyst (CySA+) Certification Exam Online Training
CompTIA CS0-002 Online Training
The questions for CS0-002 were last updated at Jan 02,2026.
- Exam Code: CS0-002
- Exam Name: CompTIA Cybersecurity Analyst (CySA+) Certification Exam
- Certification Provider: CompTIA
- Latest update: Jan 02,2026
A security analyst is reviewing the network security monitoring logs listed below:
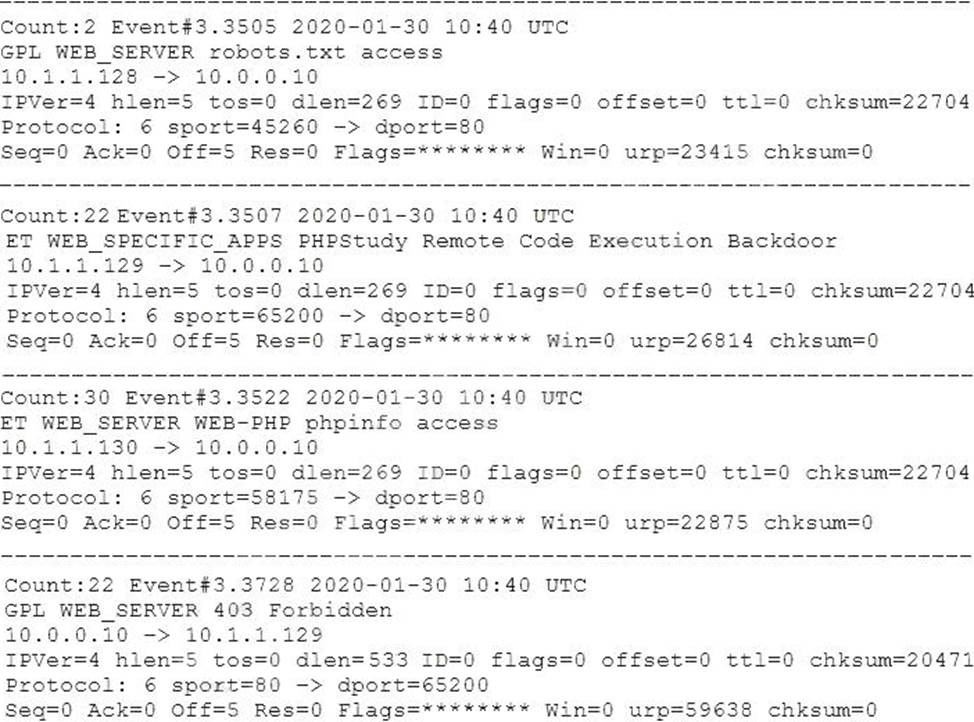
Which of the following is the analyst MOST likely observing? (Select TWO).
- A . 10.1.1.128 sent malicious requests, and the alert is a false positive.
- B . 10.1.1.129 sent potential malicious requests to the web server.
- C . 10.1.1.129 sent non-malicious requests, and the alert is a false positive.
- D . 10.1.1.128 sent potential malicious traffic to the web server.
- E . 10.1.1 .129 successfully exploited a vulnerability on the web server.
In web application scanning, static analysis refers to scanning:
- A . the system for vulnerabilities before installing the application.
- B . the compiled code of the application to detect possible issues.
- C . an application that is installed and active on a system.
- D . an application that is installed on a system that is assigned a static IP.
A security analyst discovered a specific series of IP addresses that are targeting an organization. None of the attacks have been successful.
Which of the following should the security analyst perform NEXT?
- A . Begin blocking all IP addresses within that subnet.
- B . Determine the attack vector and total attack surface.
- C . Begin a kill chain analysis to determine the impact.
- D . Conduct threat research on the IP addresses
Which of the following technologies can be used to store digital certificates and is typically used in high security implementations where integrity is paramount?
- A . HSM
- B . eFuse
- C . UEFI
- D . Self-encrypting drive
CORRECT TEXT
SIMULATION
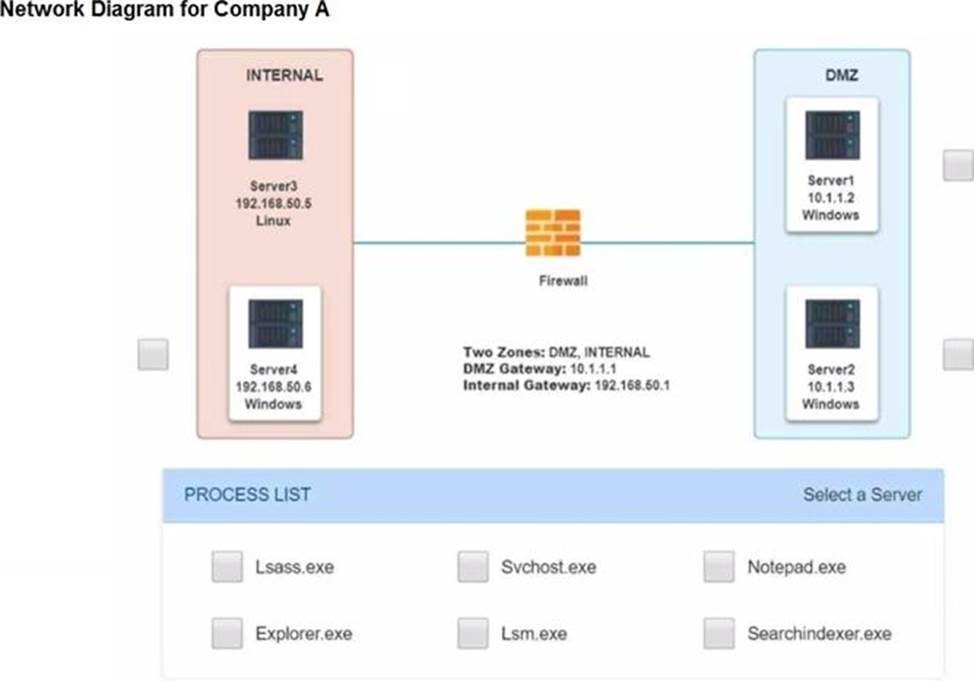
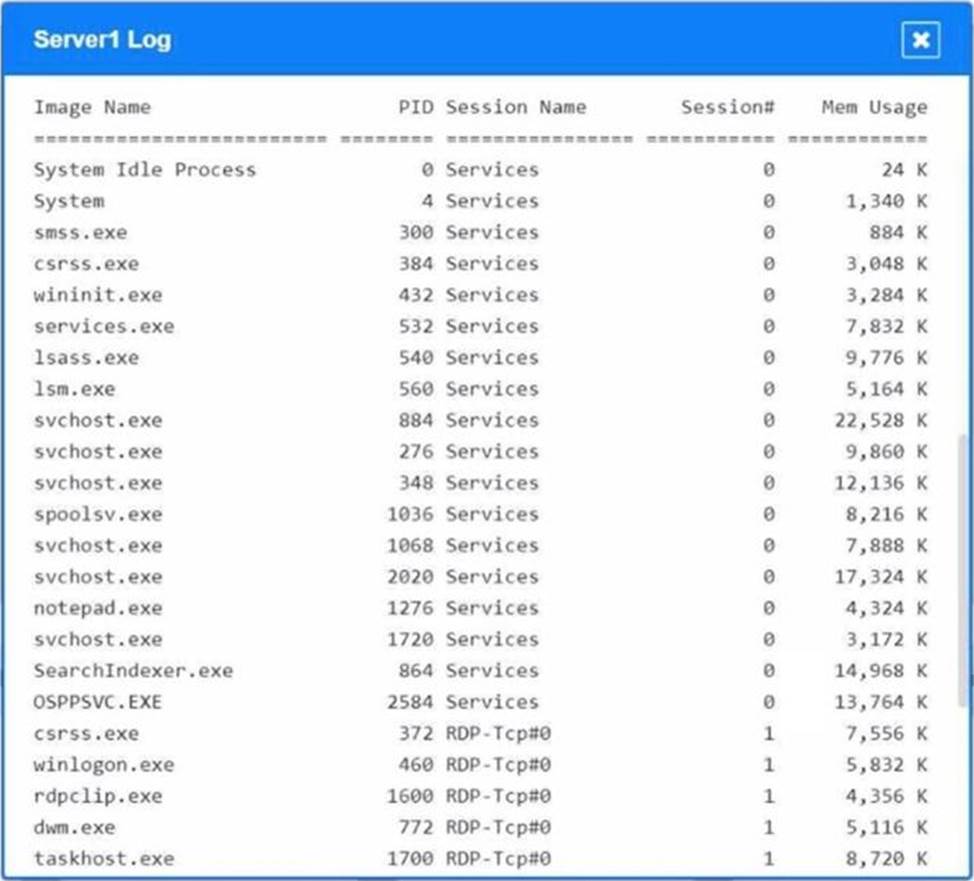
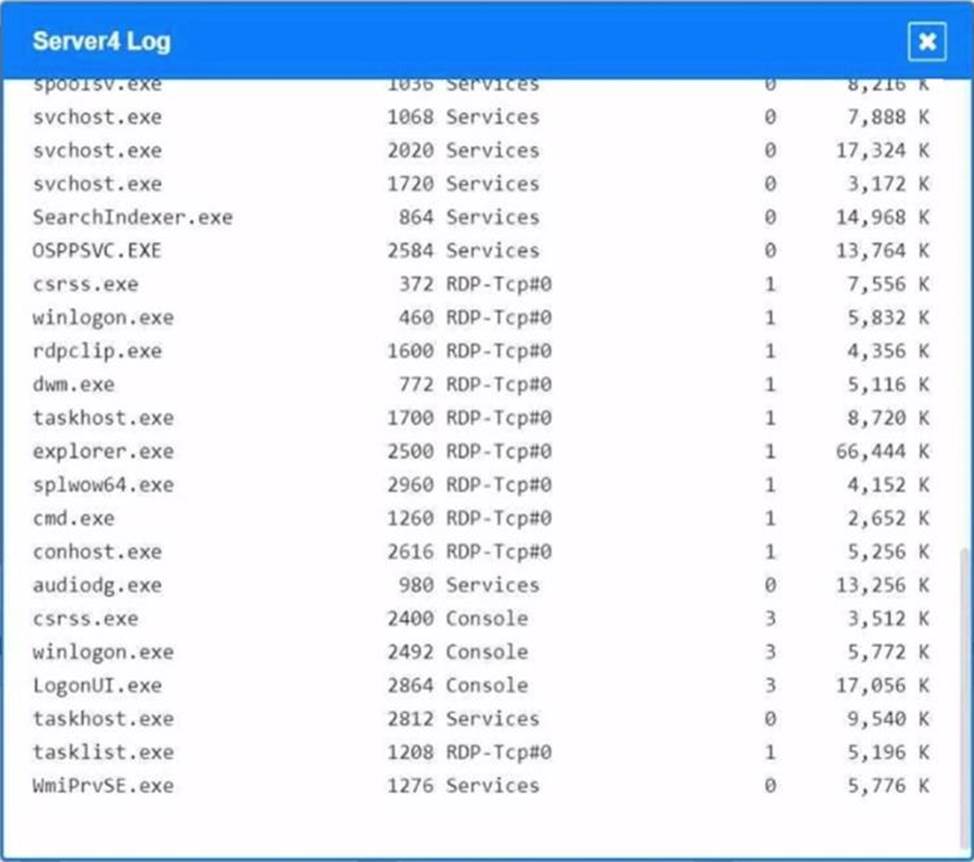
Malware is suspected on a server in the environment.
The analyst is provided with the output of commands from servers in the environment and needs to review all output files in order to determine which process running on one of the servers may be malware.
INSTRUCTIONS
Servers 1, 2, and 4 are clickable. Select the Server and the process that host the malware.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
An organization developed a comprehensive modern response policy Executive management approved the policy and its associated procedures.
Which of the following activities would be MOST beneficial to evaluate personnel’s familiarity with incident response procedures?
- A . A simulated breach scenario evolving the incident response team
- B . Completion of annual information security awareness training by ail employees
- C . Tabtetop activities involving business continuity team members
- D . Completion of lessons-learned documentation by the computer security incident response team
- E . External and internal penetration testing by a third party
A team of security analysts has been alerted to potential malware activity. The initial examination indicates one of the affected workstations is beaconing on TCP port 80 to five IP addresses and attempting to spread across the network over port 445.
Which of the following should be the team’s NEXT step during the detection phase of this response process?
- A . Escalate the incident to management, who will then engage the network infrastructure team to keep them informed.
- B . Depending on system criticality, remove each affected device from the network by disabling wired and wireless connections.
- C . Engage the engineering team to block SMB traffic internally and outbound HTTP traffic to the five IP addresses.
- D . Identify potentially affected systems by creating a correlation search in the SIEM based on the network traffic.
The SFTP server logs show thousands of failed login attempts from hundreds of IP addresses worldwide.
Which of the following controls would BEST protect the service?
- A . Whitelisting authorized IP addresses
- B . Enforcing more complex password requirements
- C . Blacklisting unauthorized IP addresses
- D . Establishing a sinkhole service
A cybersecurity analyst is reading a daily intelligence digest of new vulnerabilities. The type of vulnerability that should be disseminated FIRST is one that:
- A . enables remote code execution that is being exploited in the wild.
- B . enables data leakage but is not known to be in the environment
- C . enables lateral movement and was reported as a proof of concept
- D . affected the organization in the past but was probably contained and eradicated
Which of the following BEST describes the process by which code is developed, tested, and deployed in small batches?
- A . Agile
- B . Waterfall
- C . SDLC
- D . Dynamic code analysis
Latest CS0-002 Dumps Valid Version with 220 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund


Thank you for this test, Greatful :):)