CompTIA CAS-004 CompTIA Advanced Security Practitioner (CASP+) Exam Online Training
CompTIA CAS-004 Online Training
The questions for CAS-004 were last updated at Jan 28,2025.
- Exam Code: CAS-004
- Exam Name: CompTIA Advanced Security Practitioner (CASP+) Exam
- Certification Provider: CompTIA
- Latest update: Jan 28,2025
Clients are reporting slowness when attempting to access a series of load-balanced APIs that do not require authentication. The servers that host the APIs are showing heavy CPU utilization. No alerts are found on the WAFs sitting in front of the APIs.
Which of the following should a security engineer recommend to BEST remedy the performance issues in a timely manner?
- A . Implement rate limiting on the API.
- B . Implement geoblocking on the WAF.
- C . Implement OAuth 2.0 on the API.
- D . Implement input validation on the API.
An organization is considering a BYOD standard to support remote working. The first iteration of the solution will utilize only approved collaboration applications and the ability to move corporate data between those applications.
The security team has concerns about the following:
Unstructured data being exfiltrated after an employee leaves the organization
Data being exfiltrated as a result of compromised credentials
Sensitive information in emails being exfiltrated
Which of the following solutions should the security team implement to mitigate the risk of data loss?
- A . Mobile device management, remote wipe, and data loss detection
- B . Conditional access, DoH, and full disk encryption
- C . Mobile application management, MFA, and DRM
- D . Certificates, DLP, and geofencing
A Chief Information Officer is considering migrating all company data to the cloud to save money on expensive SAN storage.
Which of the following is a security concern that will MOST likely need to be addressed during migration?
- A . Latency
- B . Data exposure
- C . Data loss
- D . Data dispersion
Due to locality and budget constraints, an organization’s satellite office has a lower bandwidth allocation than other offices in the organization. As a result, the local security infrastructure staff is assessing architectural options that will help preserve network bandwidth and increase speed to both internal and external resources while not sacrificing threat visibility.
Which of the following would be the BEST option to implement?
- A . Distributed connection allocation
- B . Local caching
- C . Content delivery network
- D . SD-WAN vertical heterogeneity
A security analyst is concerned that a malicious piece of code was downloaded on a Linux system. After some research, the analyst determines that the suspected piece of code is performing a lot of input/output (I/O) on the disk drive.
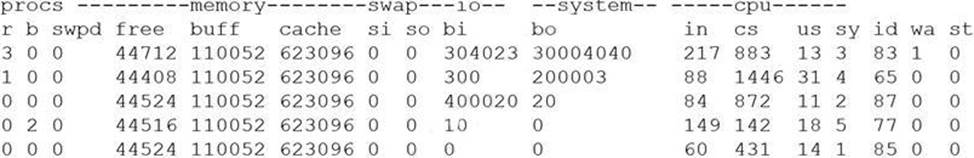
Based on the output above, from which of the following process IDs can the analyst begin an investigation?
- A . 65
- B . 77
- C . 83
- D . 87
Which of the following are risks associated with vendor lock-in? (Choose two.)
- A . The client can seamlessly move data.
- B . The vendor can change product offerings.
- C . The client receives a sufficient level of service.
- D . The client experiences decreased quality of service.
- E . The client can leverage a multicloud approach.
- F . The client experiences increased interoperability.
An organization recently experienced a ransomware attack. The security team leader is concerned about the attack reoccurring. However, no further security measures have been implemented.
Which of the following processes can be used to identify potential prevention recommendations?
- A . Detection
- B . Remediation
- C . Preparation
- D . Recovery
A security architect is implementing a web application that uses a database back end. Prior to the production, the architect is concerned about the possibility of XSS attacks and wants to identify
security controls that could be put in place to prevent these attacks.
Which of the following sources could the architect consult to address this security concern?
- A . SDLC
- B . OVAL
- C . IEEE
- D . OWASP
A security engineer was auditing an organization’s current software development practice and discovered that multiple open-source libraries were Integrated into the organization’s software. The organization currently performs SAST and DAST on the software it develops.
Which of the following should the organization incorporate into the SDLC to ensure the security of the open-source libraries?
- A . Perform additional SAST/DAST on the open-source libraries.
- B . Implement the SDLC security guidelines.
- C . Track the library versions and monitor the CVE website for related vulnerabilities.
- D . Perform unit testing of the open-source libraries.
A security analyst is investigating a possible buffer overflow attack.
The following output was found on a user’s workstation: graphic.linux_randomization.prg
Which of the following technologies would mitigate the manipulation of memory segments?
- A . NX bit
- B . ASLR
- C . DEP
- D . HSM
Latest CAS-004 Dumps Valid Version with 128 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

