CompTIA CAS-004 CompTIA Advanced Security Practitioner (CASP+) Exam Online Training
CompTIA CAS-004 Online Training
The questions for CAS-004 were last updated at Jan 28,2025.
- Exam Code: CAS-004
- Exam Name: CompTIA Advanced Security Practitioner (CASP+) Exam
- Certification Provider: CompTIA
- Latest update: Jan 28,2025
A security analyst notices a number of SIEM events that show the following activity:
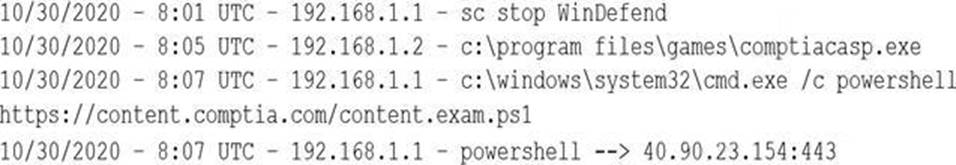
Which of the following response actions should the analyst take FIRST?
- A . Disable powershell.exe on all Microsoft Windows endpoints.
- B . Restart Microsoft Windows Defender.
- C . Configure the forward proxy to block 40.90.23.154.
- D . Disable local administrator privileges on the endpoints.
A company hired a third party to develop software as part of its strategy to be quicker to market. The company’s policy outlines the following requirements: https://i.postimg.cc/8P9sB3zx/image.png
The credentials used to publish production software to the container registry should be stored in a secure location.
Access should be restricted to the pipeline service account, without the ability for the third-party developer to read the credentials directly.
Which of the following would be the BEST recommendation for storing and monitoring access to these shared credentials?
- A . TPM
- B . Local secure password file
- C . MFA
- D . Key vault
A business stores personal client data of individuals residing in the EU in order to process requests for mortgage loan approvals.
Which of the following does the business’s IT manager need to consider?
- A . The availability of personal data
- B . The right to personal data erasure
- C . The company’s annual revenue
- D . The language of the web application
A company publishes several APIs for customers and is required to use keys to segregate customer data sets.
Which of the following would be BEST to use to store customer keys?
- A . A trusted platform module
- B . A hardware security module
- C . A localized key store
- D . A public key infrastructure
An organization wants to perform a scan of all its systems against best practice security configurations.
Which of the following SCAP standards, when combined, will enable the organization to view each of the configuration checks in a machine-readable checklist format for fill automation? (Choose two.)
- A . ARF
- B . XCCDF
- C . CPE
- D . CVE
- E . CVSS
- F . OVAL
A company is migrating from company-owned phones to a BYOD strategy for mobile devices. The pilot program will start with the executive management team and be rolled out to the rest of the staff in phases. The company’s Chief Financial Officer loses a phone multiple times a year.
Which of the following will MOST likely secure the data on the lost device?
- A . Require a VPN to be active to access company data.
- B . Set up different profiles based on the person’s risk.
- C . Remotely wipe the device.
- D . Require MFA to access company applications.
A security architect works for a manufacturing organization that has many different branch offices. The architect is looking for a way to reduce traffic and ensure the branch offices receive the latest copy of revoked certificates issued by the CA at the organization’s headquarters location. The solution must also have the lowest power requirement on the CA.
Which of the following is the BEST solution?
- A . Deploy an RA on each branch office.
- B . Use Delta CRLs at the branches.
- C . Configure clients to use OCSP.
- D . Send the new CRLs by using GPO.
After a security incident, a network security engineer discovers that a portion of the company’s sensitive external traffic has been redirected through a secondary ISP that is not normally used.
Which of the following would BEST secure the routes while allowing the network to function in the event of a single provider failure?
- A . Disable BGP and implement a single static route for each internal network.
- B . Implement a BGP route reflector.
- C . Implement an inbound BGP prefix list.
- D . Disable BGP and implement OSPF.
A company’s SOC has received threat intelligence about an active campaign utilizing a specific vulnerability. The company would like to determine whether it is vulnerable to this active campaign.
Which of the following should the company use to make this determination?
- A . Threat hunting
- B . A system penetration test
- C . Log analysis within the SIEM tool
- D . The Cyber Kill Chain
A security engineer needs to recommend a solution that will meet the following requirements:
Identify sensitive data in the provider’s network
Maintain compliance with company and regulatory guidelines
Detect and respond to insider threats, privileged user threats, and compromised accounts Enforce datacentric security, such as encryption, tokenization, and access control
Which of the following solutions should the security engineer recommend to address these requirements?
- A . WAF
- B . CASB
- C . SWG
- D . DLP
Latest CAS-004 Dumps Valid Version with 128 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

