CompTIA CAS-004 CompTIA Advanced Security Practitioner (CASP+) Exam Online Training
CompTIA CAS-004 Online Training
The questions for CAS-004 were last updated at Jan 29,2025.
- Exam Code: CAS-004
- Exam Name: CompTIA Advanced Security Practitioner (CASP+) Exam
- Certification Provider: CompTIA
- Latest update: Jan 29,2025
A company suspects a web server may have been infiltrated by a rival corporation.
The security engineer reviews the web server logs and finds the following:
![]()
The security engineer looks at the code with a developer, and they determine the log entry is created when the following line is run:
![]()
Which of the following is an appropriate security control the company should implement?
- A . Restrict directory permission to read-only access.
- B . Use server-side processing to avoid XSS vulnerabilities in path input.
- C . Separate the items in the system call to prevent command injection.
- D . Parameterize a query in the path variable to prevent SQL injection.
A company that uses AD is migrating services from LDAP to secure LDAP. During the pilot phase, services are not connecting properly to secure LDAP.
Block is an except of output from the troubleshooting session:
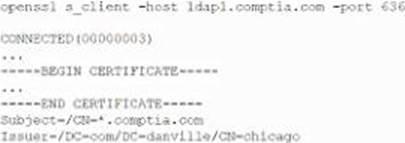
Which of the following BEST explains why secure LDAP is not working? (Select TWO.)
- A . The clients may not trust idapt by default.
- B . The secure LDAP service is not started, so no connections can be made.
- C . Danvills.com is under a DDoS-inator attack and cannot respond to OCSP requests.
- D . Secure LDAP should be running on UDP rather than TCP.
- E . The company is using the wrong port. It should be using port 389 for secure LDAP.
- F . Secure LDAP does not support wildcard certificates.
- G . The clients may not trust Chicago by default.
A threat analyst notices the following URL while going through the HTTP logs.
![]()
Which of the following attack types is the threat analyst seeing?
- A . SQL injection
- B . CSRF
- C . Session hijacking
- D . XSS
The Chief information Officer (CIO) of a large bank, which uses multiple third-party organizations to deliver a service, is concerned about the handling and security of customer data by the parties.
Which of the following should be implemented to BEST manage the risk?
- A . Establish a review committee that assesses the importance of suppliers and ranks them according to contract renewals. At the time of contract renewal, incorporate designs and operational controls into the contracts and a right-to-audit clause. Regularly assess the supplier’s post-contract renewal with a dedicated risk management team.
- B . Establish a team using members from first line risk, the business unit, and vendor management to assess only design security controls of all suppliers. Store findings from the reviews in a database for all other business units and risk teams to reference.
- C . Establish an audit program that regularly reviews all suppliers regardless of the data they access, how they access the data, and the type of data, Review all design and operational controls based on best practice standard and report the finding back to upper management.
- D . Establish a governance program that rates suppliers based on their access to data, the type of data, and how they access the data Assign key controls that are reviewed and managed based on the supplier’s rating. Report finding units that rely on the suppliers and the various risk teams.
Company A is establishing a contractual with Company B. The terms of the agreement are formalized in a document covering the payment terms, limitation of liability, and intellectual property rights.
Which of the following documents will MOST likely contain these elements
- A . Company A-B SLA v2.docx
- B . Company A OLA v1b.docx
- C . Company A MSA v3.docx
- D . Company A MOU v1.docx
- E . Company A-B NDA v03.docx
A company requires a task to be carried by more than one person concurrently. This is an example of:
- A . separation of d duties.
- B . dual control
- C . least privilege
- D . job rotation
A health company has reached the physical and computing capabilities in its datacenter, but the computing demand continues to increase. The infrastructure is fully virtualized and runs custom and commercial healthcare application that process sensitive health and payment information.
Which of the following should the company implement to ensure it can meet the computing demand while complying with healthcare standard for virtualization and cloud computing?
- A . Hybrid IaaS solution in a single-tenancy cloud
- B . Pass solution in a multinency cloud
- C . SaaS solution in a community cloud
- D . Private SaaS solution in a single tenancy cloud.
A developer implement the following code snippet.

Which of the following vulnerabilities does the code snippet resolve?
- A . SQL inject
- B . Buffer overflow
- C . Missing session limit
- D . Information leakage
A security analyst is investigating a series of suspicious emails by employees to the security team. The email appear to come from a current business partner and do not contain images or URLs. No images or URLs were stripped from the message by the security tools the company uses instead, the emails only include the following in plain text.
![]()
Which of the following should the security analyst perform?
- A . Contact the security department at the business partner and alert them to the email event.
- B . Block the IP address for the business partner at the perimeter firewall.
- C . Pull the devices of the affected employees from the network in case they are infected with a zero-day virus.
- D . Configure the email gateway to automatically quarantine all messages originating from the business partner.
A financial services company wants to migrate its email services from on-premises servers to a cloud-based email solution. The Chief information Security Officer (CISO) must brief board of directors on the potential security concerns related to this migration.
The board is concerned about the following.
* Transactions being required by unauthorized individual
* Complete discretion regarding client names, account numbers, and investment information.
* Malicious attacker using email to distribute malware and ransom ware.
* Exfiltration of sensitivity company information.
The cloud-based email solution will provide an6-malware, reputation-based scanning, signature-based scanning, and sandboxing.
Which of the following is the BEST option to resolve the board’s concerns for this email migration?
- A . Data loss prevention
- B . Endpoint detection response
- C . SSL VPN
- D . Application whitelisting
Latest CAS-004 Dumps Valid Version with 128 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

