CompTIA 220-1001 CompTIA A+ Certification Exam: Core 1 Online Training
CompTIA 220-1001 Online Training
The questions for 220-1001 were last updated at Dec 29,2025.
- Exam Code: 220-1001
- Exam Name: CompTIA A+ Certification Exam: Core 1
- Certification Provider: CompTIA
- Latest update: Dec 29,2025
An end user wants to have a second monitor installed on a laptop.
Which of the following would allow a technician to configure the laptop to show both screens once the cable is connected?
- A . Plug an external monitor into the USB port.
- B . Use the Fn and function key combination
- C . Adjust the monitor display settings.
- D . Enable DisplayPort.
Multiple users report that the network printer, which is connected through the print server, is not printing.
Which of the following should a technician do FIRST to remedy this situation?
- A . Replace the USB cable.
- B . Reinstall the drivers on users’ PCs.
- C . have users restart their PCs.
- D . Clear the print queue.
An ISP has notified a SOHO user of a usage increase on the user’s network. The user is concerned the WiFi network is being utilized by unauthorized users.
Which of the following would minimize the unauthorized use of the WiFi network?
- A . Implement MAC filtering
- B . Enable NAT
- C . Create a network DMZ
- D . Upgrade the encryption standards
CORRECT TEXT
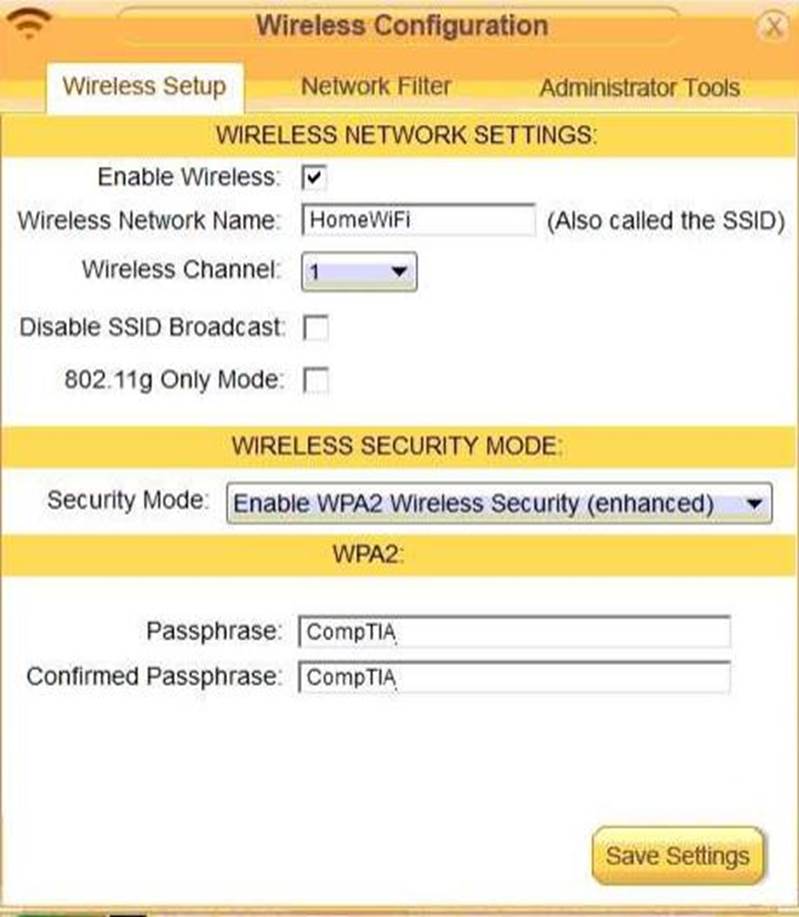
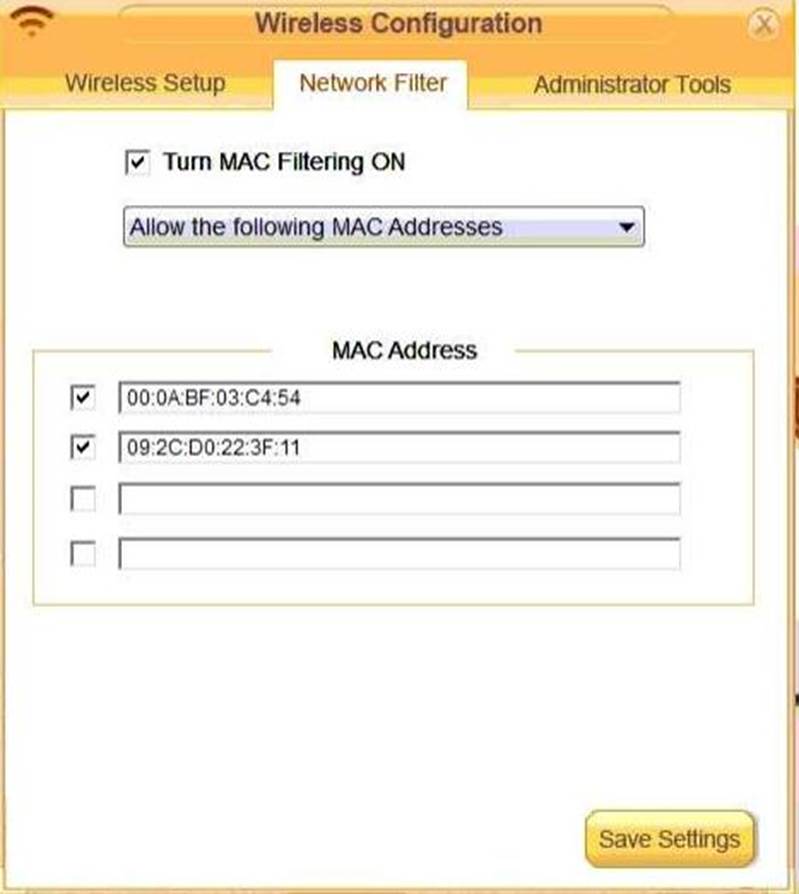
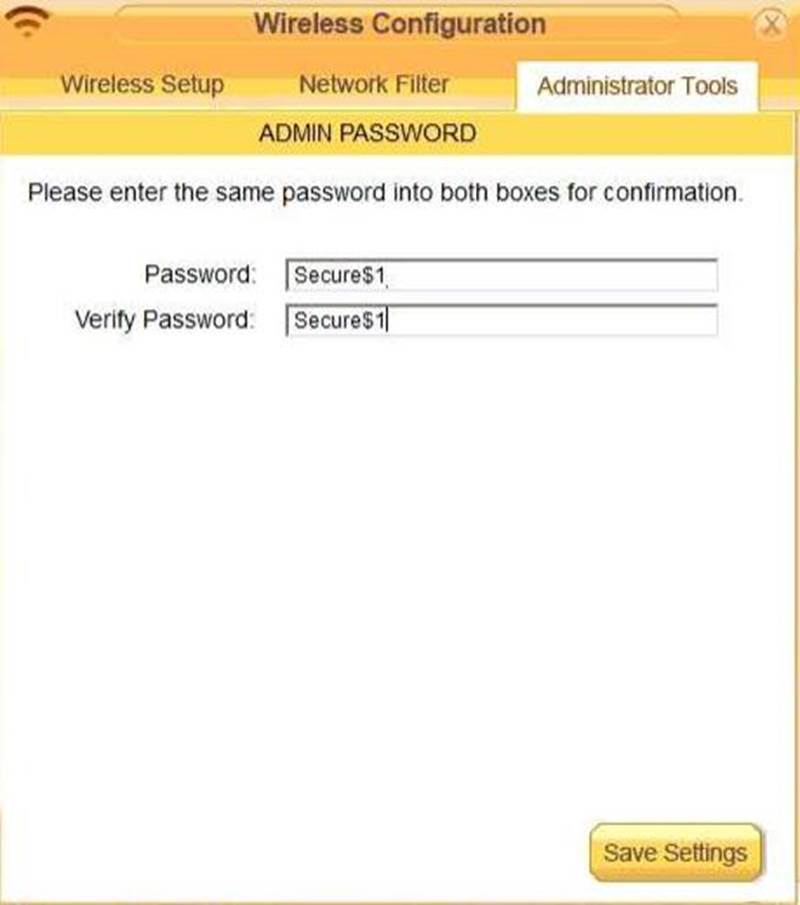
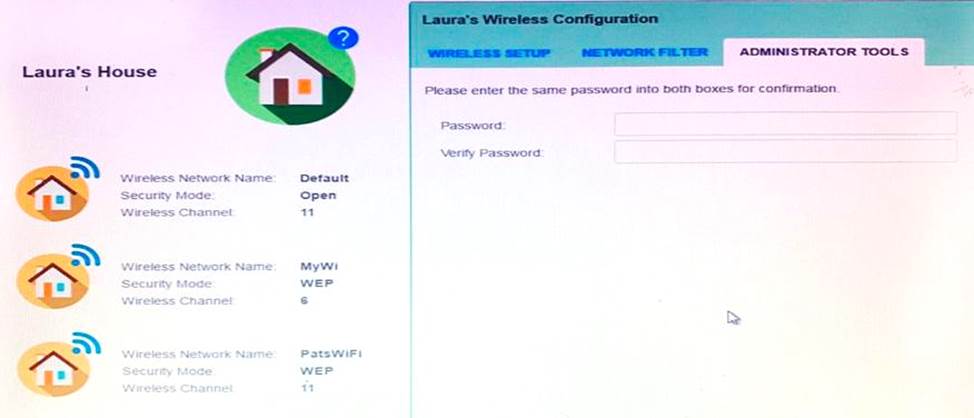
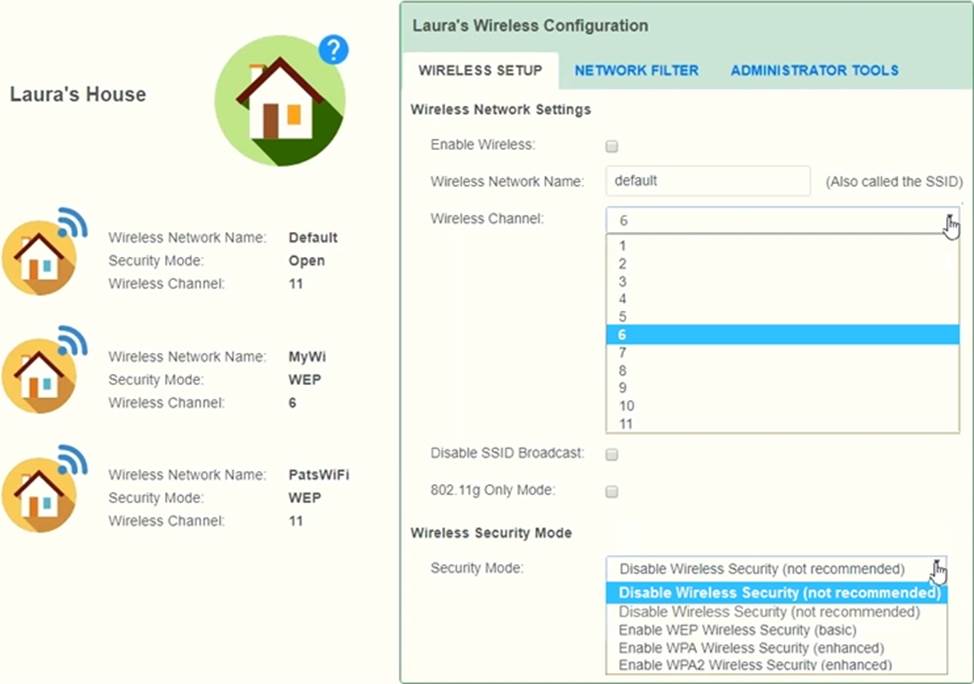
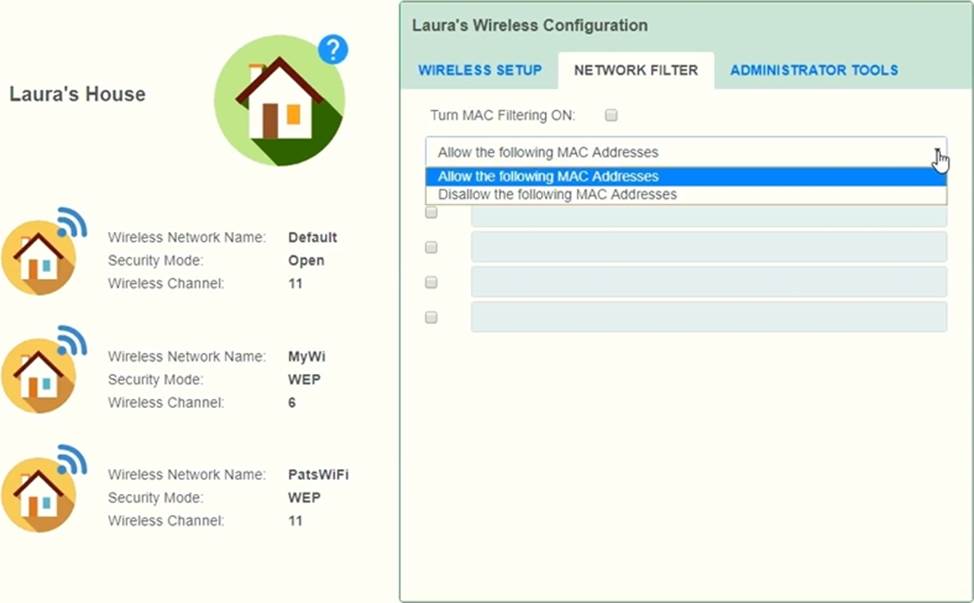
Laura, a customer, has instructed you to configure her home office wireless access point.
She plans to use the wireless network for finances and has requested that the network be setup with the highest encryption possible.
Additionally, Laura knows that her neighbors have wireless networks and wants to ensure that her network is not being interfered with by the other networks.
She requests that the default settings be changed to the following.
Wireless Name: HomeWiFi
Shared Key: CompTIA
Router Password: Secure$1
Finally, Laura wants to ensure that only her laptop and Smartphone can connect to the network.
Laptop: IP Address 192.168.1.100
Hardware Address: 00:0A:BF:03:C4:54
Smartphone: IP Address 192.168.1.101
Hardware Address: 09:2C:D0:22:3F:11
INSTRUCTIONS
Configure Laura’s wireless network using the network adapter window.
If at any time you would like to bring back the initial state of the situation, please click the Reset All button.
A customer recently moved a high-end graphics card from a known-working computer to a different computer. The computer works without issue when viewing email and web pages or when using certain applications. However, when a game with high-end graphics requirements is opened, the program will run for a few minutes before the computer shuts down.
Which of the following is MOST likely causing the problem?
- A . Power supply wattage
- B . Video RAM
- C . CPU frequency
- D . Monitor resolution
A user is unable to access websites and has reported connectivity issues with pop-ups on the screen. A technician removes malware, and then is able to ping the router and access the websites.
Which of the following NEXT steps should the technician perform in troubleshooting this issue? (Choose two.)
- A . Documents findings, actions, and outcomes.
- B . Reboot the device to verify the fix.
- C . Reconnect the device to the network.
- D . Verify the settings in IPConfig.
- E . Research the problem based on symptoms.
- F . Run a virus scan.
A network administrator is troubleshooting a notebook that is not loading the local Windows 10 operating system. All the computers inside the company are installed using UEFI mode selected. The message on the screen shows a failed attempt to connect to a PXE server.
When requested, the end user reported trying to improve the computer’s speed by changing some BIOS configurations randomly.
Which of the following should the network administrator check FIRST inside BIOS?
- A . C-states should be configured to 2
- B . Secure Boot should be enabled
- C . Wake-on-LAN should be unchecked
- D . The PXE server address should be set
A network administrator must install a device that will proactively stop outside attacks from reaching the LAN.
Which of the following devices would BEST meet the organization’s needs?
- A . IPS
- B . IDS.
- C . Proxy server
- D . Authentication server.
Which of the following resources in the MOST critical when using cloud file-storage synchronization applications?
- A . Disk speed
- B . I/O bandwidth
- C . RAM utilization
- D . CPU utilization
Which of the following ports are used for secure sessions? (Select two.)
- A . 22
- B . 23
- C . 25
- D . 80
- E . 110
- F . 443
Latest 220-1001 Dumps Valid Version with 718 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund