Citrix 1Y0-440 Architecting a Citrix Networking Solution Online Training
Citrix 1Y0-440 Online Training
The questions for 1Y0-440 were last updated at Feb 26,2026.
- Exam Code: 1Y0-440
- Exam Name: Architecting a Citrix Networking Solution
- Certification Provider: Citrix
- Latest update: Feb 26,2026
Scenario: A Citrix Architect has deployed two MPX devices, 12.0.53.13 nc and MPX 11500 models, in a high availability (HA) pair for the Workspace labs team. The deployment method is two-arm. and the devices are installed behind a CISCO ASA 5585 firewall. The architect enables the following features on the Citrix ADC devices: Content Switching. SSL Offloading, Load Balancing, Citrix Gateway, Application Firewall in hybrid security, and Appflow. All are enabled to send monitoring information to Citrix Application Delivery Management 12.0.53.13 nc build. The architect is preparing to configure load balancing for Microsoft Exchange 2016 server.
The following requirements were discussed during the implementation:
✑ All traffic needs to be segregated based on applications, and the fewest number of IP addresses should be utilized during the configuration.
✑ All traffic should be secured, and any traffic coming into HTTP should be redirected to HTTPS.
✑ Single Sign-on should be created for Microsoft Outlook web access (OWA).
✑ Citrix ADC should recognize Uniform Resource Identifier (URI) and close the
session to Citrix ADC, when users hit the Logoff button in Microsoft Outlook web access.
✑ Users should be able to authenticate using user principal name (UPN).
✑ The Layer 7 monitor should be configured to monitor the Microsoft Outlook web access servers, and the monitor probes must be sent on SSL.
Which Responder policy can be utilized to redirect the users from http://mail.citrix.com to https://mail.citrix.com/owa?
- A . add responder action Act redirect ""https://mail.citrix.com/owa/"" -responseStatusCode 302 add responder policy pol "http.REQ.URL.PATH_AND_QUERY.EQ("/")" Act
- B . add responder action Act redirect ""https://mail.citrix.com/owa/"" -responseStatusCode 307 add responder policy pol "HTTP.REQ.IS_NOTVALID Act
- C . add responder action Act redirect ""http://mail.citrix.com/owa/"" -responseStatusCode 302 add responder policy pol "HTTP.REQ.IS_NOTVALID Act
- D . add responder action Act redirect ""http://mail.citrix.com/owa/"" -responseStatusCode 302 add responder policy pol "http.REQ.URL.PATH_AND_QUERY.EQ("/")" Act
Scenario: A Citrix Architect has set up NetScaler MPX devices in high availability mode with version 12.0.53.13 nc. These are placed behind a Cisco ASA 5505 Firewall. The Cisco ASA Firewall is configured to block traffic using access control lists. The network address translation (NAT) is also performed on the firewall.
The following requirements were captured by the architect during the discussion held as part of the NetScaler security implementation project with the customer’s security team:
The NetScaler MPX device:
✑ should monitor the rate of traffic either on a specific virtual entity or on the device. It should be able to mitigate the attacks from a hostile client sending a flood of requests. The NetScaler device should be able to stop the HTTP, TCP, and DNS based requests.
✑ needs to protect backend servers from overloading.
✑ needs to queue all the incoming requests on the virtual server level instead of the service level.
✑ should provide protection against well-known Windows exploits, virus-infected personal computers, centrally managed automated botnets, compromised webservers, known spammers/hackers, and phishing proxies.
✑ should provide flexibility to enforce the decided level of security check inspections for the requests originating from a specific geolocation database.
✑ should block the traffic based on a pre-determined header length, URL length, and cookie length. The device should ensure that characters such as a single straight quote (“); backslash (); and semicolon (;) are either blocked, transformed, or dropped while being sent to the backend server.
Which security feature should the architect configure to meet these requirements?
- A . Global Server Load balancing with Dynamic RTT
- B . Global Server Load Balancing with DNS views
- C . Geolocation-based blocking using Application Firewall
- D . geolocation-based blocking using Responder policies
- E . Global Server Load Balancing with Mac Based Forwarding
A Citrix Architect can execute a configuration job using a DeployMasterConfiguration template on a Citrix ADC____deployed________. (Choose the correct option to complete sentence:
- A . MPX; In high availability
- B . CPX: without partitions
- C . CPX; In high availability
- D . MPX; as a cluster Instance
- E . SDX; with more than 6 partitions
A Citrix Architect needs to make sure that maximum concurrent AAA user sessions are limited to 4000 as a security restriction.
Which authentication setting can the architect utilize to view the current configuration?
- A . Global Session Settings
- B . AAA Parameters
- C . Active User Session
- D . AAA Virtual Server
Scenario: A Citrix Architect needs to assess an existing on-premises NetScaler deployment which includes Advanced Endpoint Analysis scans. During a previous security audit, the team discovered that certain endpoint devices were able to perform unauthorized actions despite NOT meeting pre-established criteria.
The issue was isolated to several endpoint analysis (EPA) scan settings.
Click the Exhibit button to view the endpoint security requirements and configured EPA policy settings.

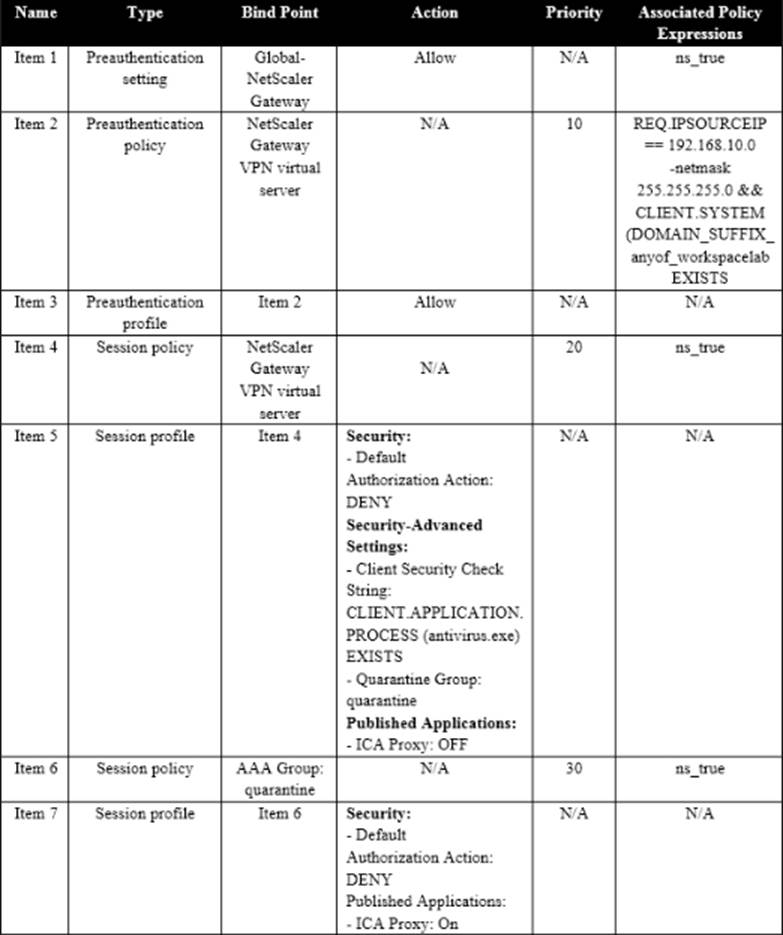
Which setting is preventing the security requirements of the organization from being met?
- A . Item 3
- B . Item 4
- C . Item 2
- D . Item 6
Which four settings can a Citrix Architect use to create a configuration job using Citrix Application Delivery Management? (Choose four.)
- A . Action
- B . File
- C . Configuration Template
- D . StyleBooks
- E . Event Manager
- F . Instance
- G . Record and Play
Which response is returned by the Citrix ADC, if a negative response is present in the local cache?
- A . NXDOMAIN
- B . NXDATA
- C . NODOMAIN
- D . NO DATA
Which two NetScaler cookies indicate the validity of the Authentication, Authorization and Accounting (AAA) session for users? (Choose two.)
- A . NSC_WT
- B . NSC_TMAS
- C . NSC_AAAC
- D . NSC_TMAA
Which three methods can a Citrix Architect use to assess the capabilities of a network infrastructure? (Choose three.)
- A . Review existing monitoring solutions for periods of latency, lost packets, and insufficient bandwidth.
- B . Map the location of the users against the existing network topology.
- C . Alter firewall rules of existing network to fit into the new NetScaler Deployment.
- D . Examine the topology for single points of failure and potential bottlenecks.
- E . Ensure that users and computers are in the correct organizational units (OUs).
Scenario: A Citrix Architect needs to assess an existing Citrix ADC configuration. The customer recently found that members of certain administrator groups were receiving permissions on the production Citrix ADC appliances that do NOT align with the designed security requirements.
Click the Exhibit button to view the configured command policies for the production Citrix ADC deployment.
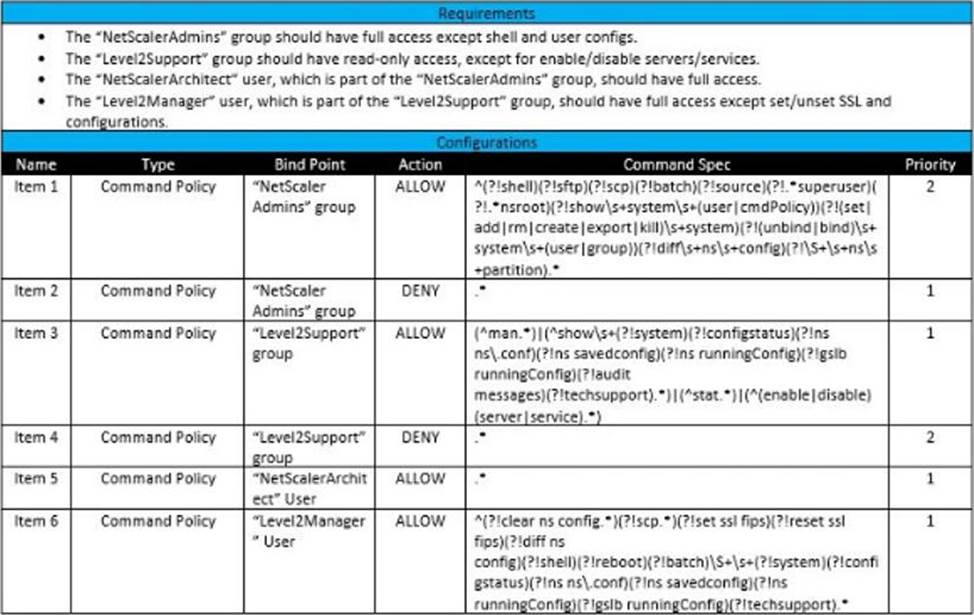
To align the command policy configuration with the security requirements of the organization, the__________for________________should change. (Choose the correct option to complete the sentence.)
- A . command spec; Item 6
- B . priority; Item 5
- C . command spec; Item 3
- D . action; Item 4
- E . priority; Item 2
- F . action; Item 1
Latest 1Y0-440 Dumps Valid Version with 63 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

