Check Point 156-915.77 Check Point Certified Security Expert Update Blade Online Training
Check Point 156-915.77 Online Training
The questions for 156-915.77 were last updated at Nov 24,2024.
- Exam Code: 156-915.77
- Exam Name: Check Point Certified Security Expert Update Blade
- Certification Provider: Check Point
- Latest update: Nov 24,2024
In Cluster XL, _______ is defined by default as a critical device.
- A . fw.d
- B . protect.exe
- C . PROT_SRV.EXE
- D . Filter
Refer to Exhibit below: Match the Cluster XL modes with their configurations.
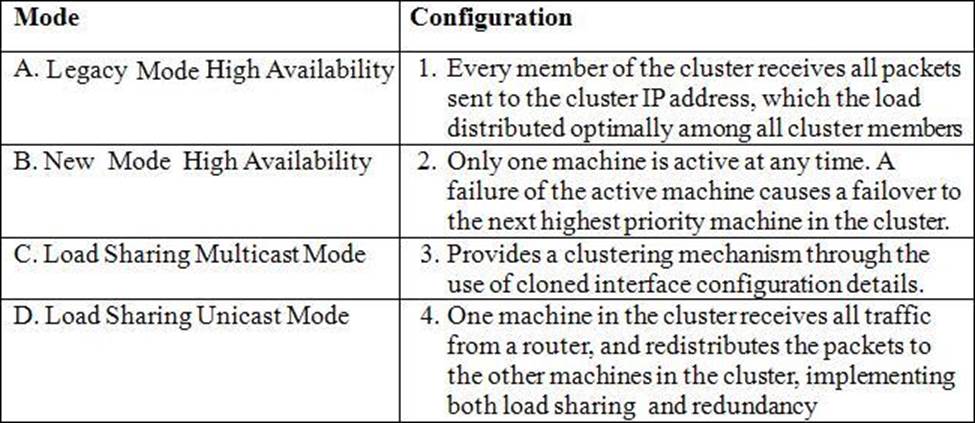
- A . A – 3, B – 2, C – 4, D – 1
- B . A – 2, B – 3, C – 1, D – 4
- C . A – 2, B – 3, C – 4, D – 1
- D . A – 3, B – 2, C – 1, D – 4
When synchronizing clusters, which of the following statements is NOT true?
- A . The state of connections using resources is maintained by a Security Server, so these connections cannot be synchronized.
- B . In the case of a failover, accounting information on the failed member may be lost despite a properly working synchronization.
- C . Only cluster members running on the same OS platform can be synchronized.
- D . Client Authentication or Session Authentication connections through a cluster member will be lost if the cluster member fails.
When synchronizing clusters, which of the following statements is NOT true?
- A . User Authentication connections will be lost by the cluster.
- B . An SMTP resource connection using CVP will be maintained by the cluster.
- C . In the case of a failover, accounting information on the failed member may be lost despite a properly working synchronization.
- D . Only cluster members running on the same OS platform can be synchronized.
When a failed cluster member recovers, which of the following actions is NOT taken by the recovering member?
- A . It will try to take the policy from one of the other cluster members.
- B . It will not check for any updated policy and load the last installed policy with a warning message indicating that the Security Policy needs to be installed from the Security Management Server.
- C . If the Security Management Server has a newer policy, it will be retrieved, else the local policy will be loaded.
- D . It compares its local policy to the one on the Security Management Server.
When a failed cluster member recovers, which of the following actions is NOT taken by the recovering member?
- A . It will try to take the policy from one of the other cluster members.
- B . It will not check for any updated policy and load the last installed policy with a warning message indicating that the Security Policy needs to be installed from the Security Management Server.
- C . If the Security Management Server has a newer policy, it will be retrieved, else the local policy will be loaded.
- D . It compares its local policy to the one on the Security Management Server.
When a failed cluster member recovers, which of the following actions is NOT taken by the recovering member?
- A . It will try to take the policy from one of the other cluster members.
- B . It will not check for any updated policy and load the last installed policy with a warning message indicating that the Security Policy needs to be installed from the Security Management Server.
- C . If the Security Management Server has a newer policy, it will be retrieved, else the local policy will be loaded.
- D . It compares its local policy to the one on the Security Management Server.
The synchronization network may only include switches and hubs.
You are the Mega Corp Security Administrator. This company uses a firewall cluster, consisting of two cluster members. The cluster generally works well but one day you find that the cluster is behaving strangely. You assume that there is a connectivity problem with the cluster synchronization cluster link (cross-over cable).
Which of the following commands is the best for testing the connectivity of the crossover cable?
- A . telnet <IP address of the synchronization interface on the other cluster member>
- B . ifconfig -a
- C . ping <IP address of the synchronization interface on the other cluster member>
- D . arping <IP address of the synchronization interface on the other cluster member>
You have a High Availability Cluster XL configuration. Machines are not synchronized.
What happens to connections on failover?
- A . Connections cannot be established until cluster members are fully synchronized.
- B . It is not possible to configure High Availability that is not synchronized.
- C . Old connections are lost but can be reestablished.
- D . Old connections are lost but are automatically recovered whenever the failed machine recovers.
Latest 156-915.77 Dumps Valid Version with 846 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

