Check Point 156-915.77 Check Point Certified Security Expert Update Blade Online Training
Check Point 156-915.77 Online Training
The questions for 156-915.77 were last updated at Apr 08,2025.
- Exam Code: 156-915.77
- Exam Name: Check Point Certified Security Expert Update Blade
- Certification Provider: Check Point
- Latest update: Apr 08,2025
Control connections between the Security Management Server and the Gateway are not encrypted by the VPN Community.
How are these connections secured?
- A . They are encrypted and authenticated using SIC.
- B . They are not encrypted, but are authenticated by the Gateway
- C . They are secured by PPTP
- D . They are not secured.
If Bob wanted to create a Management High Availability configuration, what is the minimum number of Security Management servers required in order to achieve his goal?
- A . Three
- B . Two
- C . Four
- D . One
David wants to manage hundreds of gateways using a central management tool.
What tool would David use to accomplish his goal?
- A . Smart Provisioning
- B . Smart Blade
- C . Smart Dashboard
- D . Smart LSM
From the following output of cphaprob state, which Cluster XL mode is this?
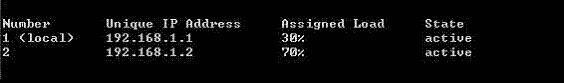
- A . New mode
- B . Multicast mode
- C . Legacy mode
- D . Unicast mode
Which of the following is NOT a feature of Cluster XL?
- A . Enhanced throughput in all Cluster XL modes (2 gateway cluster compared with 1 gateway)
- B . Transparent failover in case of device failures
- C . Zero downtime for mission-critical environments with State Synchronization
- D . Transparent upgrades
In which case is a Sticky Decision Function relevant?
- A . Load Sharing – Unicast
- B . Load Balancing – Forward
- C . High Availability
- D . Load Sharing – Multicast
You configure a Check Point QoS Rule Base with two rules: an HTTP rule with a weight of 40, and the Default Rule with a weight of 10.
If the only traffic passing through your QoS Module is HTTP traffic, what percent of bandwidth will be allocated to the HTTP traffic?
- A . 80%
- B . 40%
- C . 100%
- D . 50%
You have pushed a policy to your firewall and you are not able to access the firewall.
What command will allow you to remove the current policy from the machine?
- A . fw purge policy
- B . fw fetch policy
- C . fw purge active
- D . fw unload local
How do you verify the Check Point kernel running on a firewall?
- A . fw ctl get kernel
- B . fw ctl pstat
- C . fw kernel
- D . fw ver -k
The process ________________ compiles $FWDIR/conf/*. W files into machine language.
- A . fw gen
- B . cpd
- C . fwd
- D . fwm
Latest 156-915.77 Dumps Valid Version with 846 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

