Check Point 156-215.81 Check Point Certified Security Administrator R81 Online Training
Check Point 156-215.81 Online Training
The questions for 156-215.81 were last updated at Apr 24,2025.
- Exam Code: 156-215.81
- Exam Name: Check Point Certified Security Administrator R81
- Certification Provider: Check Point
- Latest update: Apr 24,2025
What is the Transport layer of the TCP/IP model responsible for?
- A . It transports packets as datagrams along different routes to reach their destination.
- B . It manages the flow of data between two hosts to ensure that the packets are correctly assembled and delivered to the target application.
- C . It defines the protocols that are used to exchange data between networks and how host programs interact with the Application layer.
- D . It deals with all aspects of the physical components of network connectivity and connects with different network types.
Is it possible to have more than one administrator connected to a Security Management Server at once?
- A . Yes, but only if all connected administrators connect with read-only permissions.
- B . Yes, but objects edited by one administrator will be locked for editing by others until the session is published.
- C . No, only one administrator at a time can connect to a Security Management Server
- D . Yes, but only one of those administrators will have write-permissions. All others will have read-only permission.
Which of the following is considered a "Subscription Blade", requiring renewal every 1-3 years?
- A . IPS blade
- B . IPSEC VPN Blade
- C . Identity Awareness Blade
- D . Firewall Blade
The ______ software blade package uses CPU-level and OS-level sandboxing in order to
detect and block malware.
- A . Next Generation Threat Prevention
- B . Next Generation Threat Emulation
- C . Next Generation Threat Extraction
- D . Next Generation Firewall
What are the types of Software Containers?
- A . Smart Console, Security Management, and Security Gateway
- B . Security Management, Security Gateway, and Endpoint Security
- C . Security Management, Log & Monitoring, and Security Policy
- D . Security Management, Standalone, and Security Gateway
Please choose correct command syntax to add an “emailserver1” host with IP address 10.50.23.90 using GAiA management CLI?
- A . host name myHost12 ip-address 10.50.23.90
- B . mgmt add host name ip-address 10.50.23.90
- C . add host name emailserver1 ip-address 10.50.23.90
- D . mgmt add host name emailserver1 ip-address 10.50.23.90
CPU-level of your Security gateway is peaking to 100% causing problems with traffic. You suspect that the problem might be the Threat Prevention settings.
The following Threat Prevention Profile has been created.
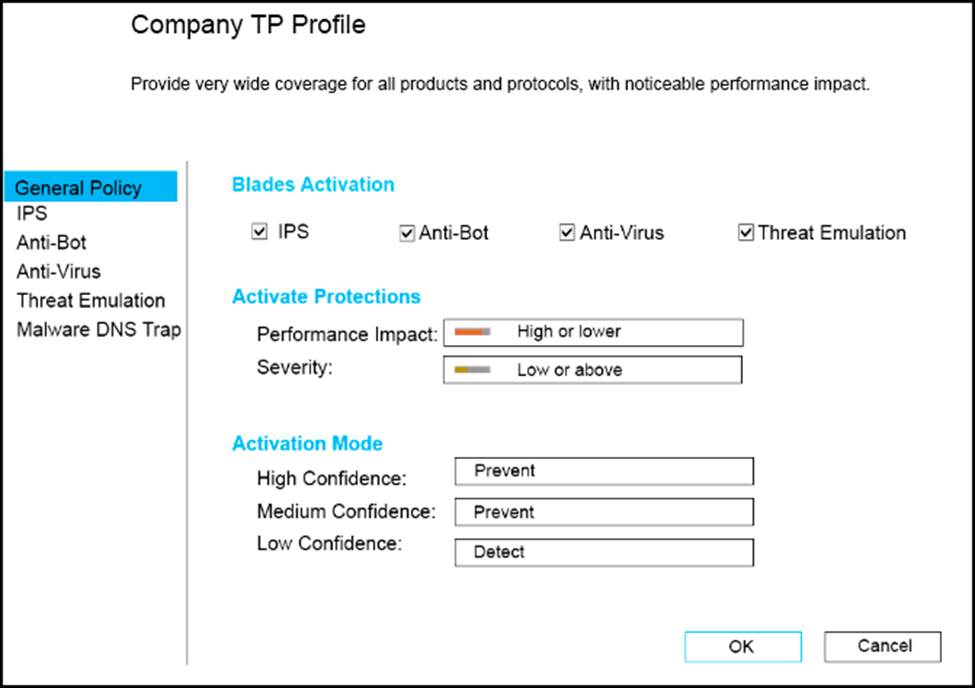
How could you tune the profile in order to lower the CPU load still maintaining security at good level? Select the BEST answer.
- A . Set High Confidence to Low and Low Confidence to Inactive.
- B . Set the Performance Impact to Medium or lower.
- C . The problem is not with the Threat Prevention Profile. Consider adding more memory to the appliance.
- D . Set the Performance Impact to Very Low Confidence to Prevent.
If the Active Security Management Server fails or if it becomes necessary to change the Active to Standby, the following steps must be taken to prevent data loss. Providing the Active Security Management Server is responsible, which of these steps should NOT be performed:
- A . Rename the hostname of the Standby member to match exactly the hostname of the Active member.
- B . Change the Standby Security Management Server to Active.
- C . Change the Active Security Management Server to Standby.
- D . Manually synchronize the Active and Standby Security Management Servers.
Name the authentication method that requires token authenticator.
- A . SecureID
- B . Radius
- C . DynamicID
- D . TACACS
What is the BEST method to deploy Identity Awareness for roaming users?
- A . Use Office Mode
- B . Use identity agents
- C . Share user identities between gateways
- D . Use captive portal
Latest 156-215.81 Dumps Valid Version with 425 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

